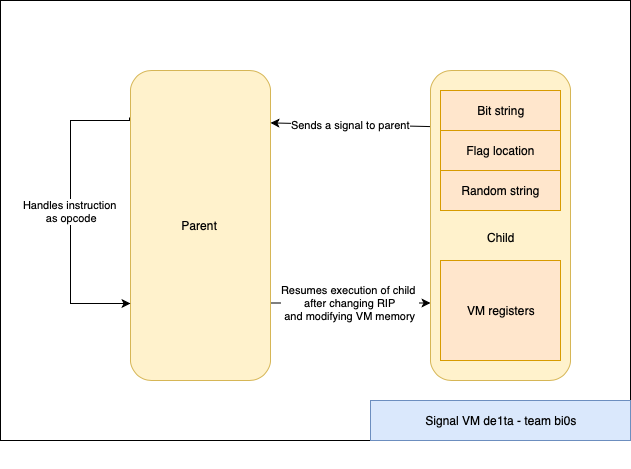
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| from sage.all import *
s=[[65, 108, 109, 111, 115, 116, 32],
[104, 101, 97, 118, 101, 110, 32],
[119, 101, 115, 116, 32, 118, 105],
[114, 103, 105, 110, 105, 97, 44],
[32, 98, 108, 117, 101, 32, 114],
[105, 100, 103, 101, 32, 109, 111],
[117, 110, 116, 97, 105, 110, 115]]
s = Matrix(IntegerModRing(256),s)
s = s.transpose()
c = [214, 77, 45, 133, 119, 151, 96, 98, 43, 136, 134, 202, 114, 151, 235, 137, 152, 243, 120, 38, 131, 41, 94, 39, 67, 251, 184, 23, 124, 206, 58, 115, 207, 251, 199, 156, 96, 175, 156, 200, 117, 205, 55, 123, 59, 155, 78, 195, 218, 216, 206, 113, 43, 48, 104, 70, 11, 255, 60, 241, 241, 69, 196, 208, 196, 255, 81, 241, 136, 81]
l = []
for i in range(0,len(c),7):
l.append(c[i:i+7])
l = Matrix(IntegerModRing(256),l)
flag = "".join("".join(map(chr,s.inverse()*l[i])) for i in range(10))
print flag
|