tl;dr
- Create a Linux profile for Ubuntu 18.04 (5.4.0-42-generic) in Volatility
- Use
linux_bashplugin to get link to the repo andlinux_find_fileplugin to recover the filepath - Decode the keyboard stream data to retrieve the flag
tl;dr
linux_bash plugin to get link to the repo and linux_find_file plugin to recover the filepathtl;dr
Challenge author: Freakston, silverf3lix
Senpai plis find me a way.
This is a fairly simple maze challenge implemented in rust.
At the start of the main function of the challenge miz we can see there is a some sort of a initialization going on at a function named miz::bacharu::Kikai::new::h3a113b790cc2bb5c
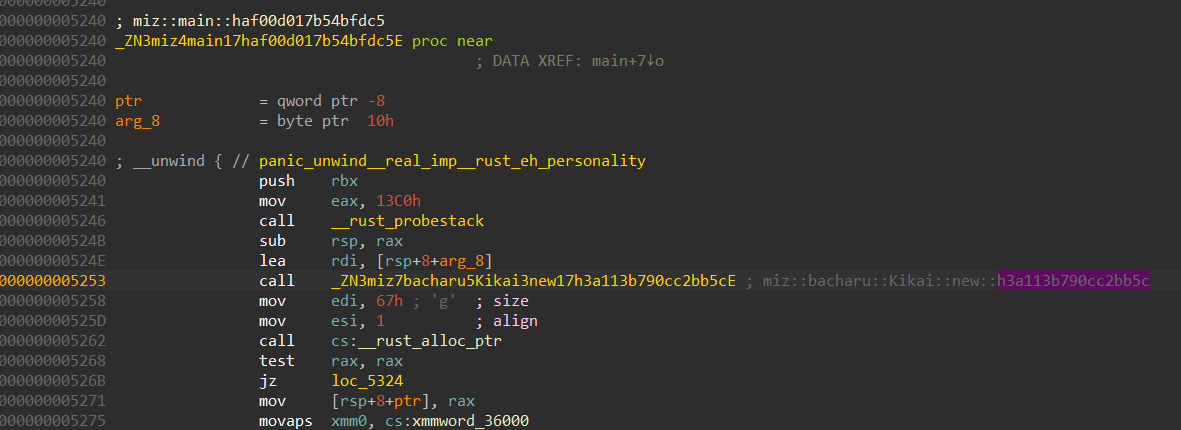
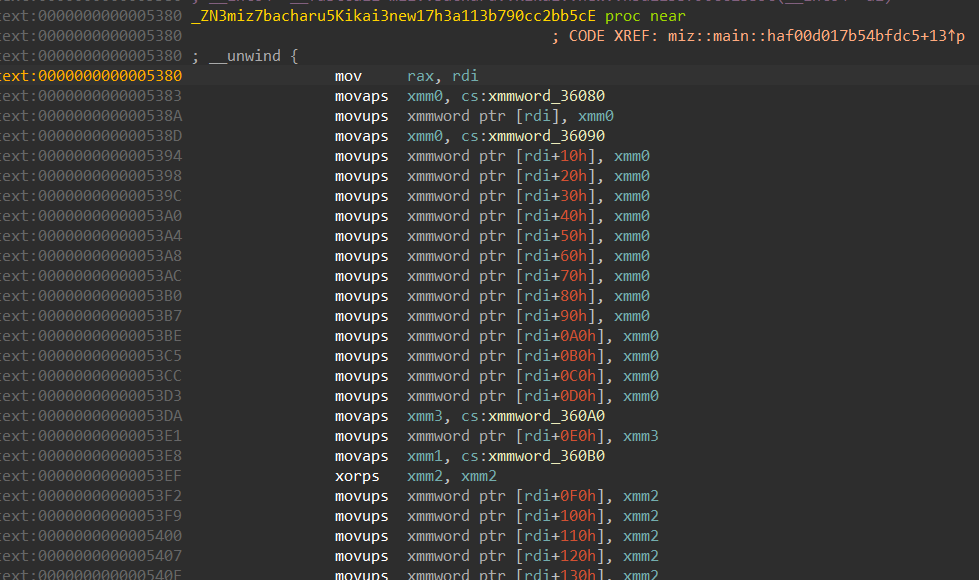
We can see from here than this function takes care of initializing the maze. We can extract the maze bytes either directly from here or during runtime, which ever is preferred.
Moving forward we can see that the function is also getting our input, and sending it over to another function miz::bacharu::Kikai::run::h14398f1fc265e61e
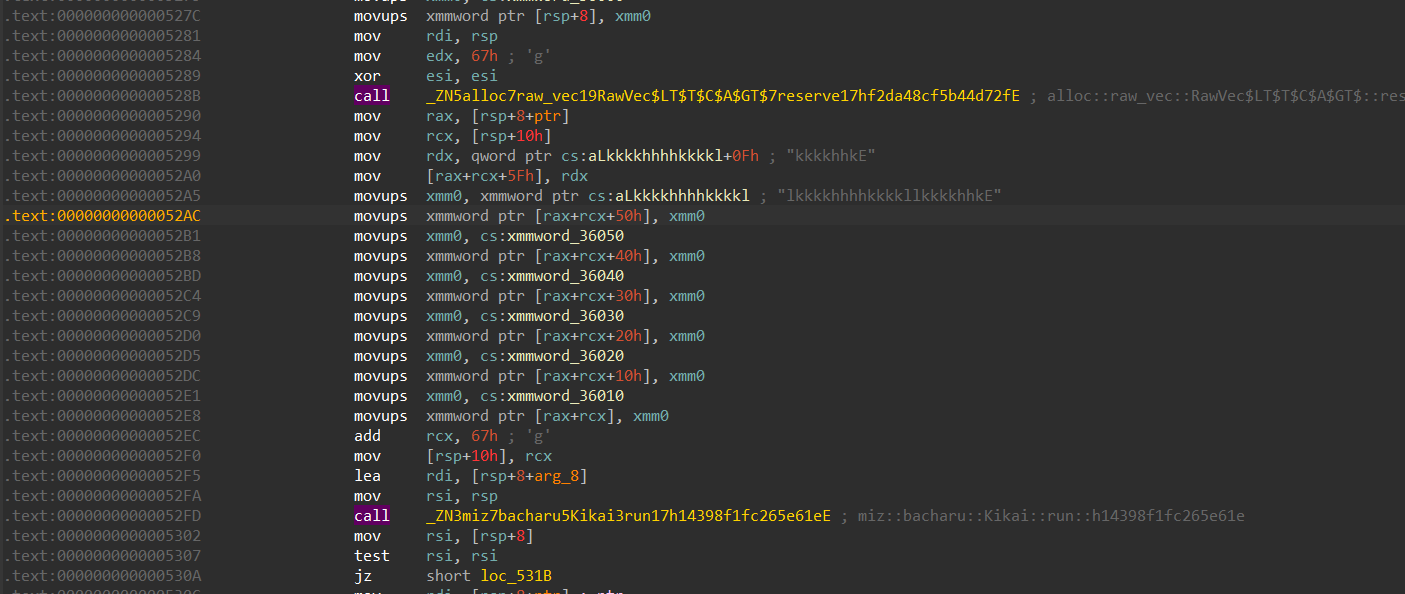
The function miz::bacharu::Kikai::run takes care of the maze logic, the up, left, down and right.
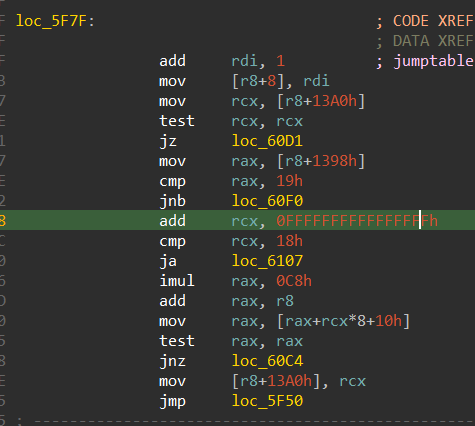
We can see that the case “h” takes care of going left, which is by subtracting 1 from the y coordinate
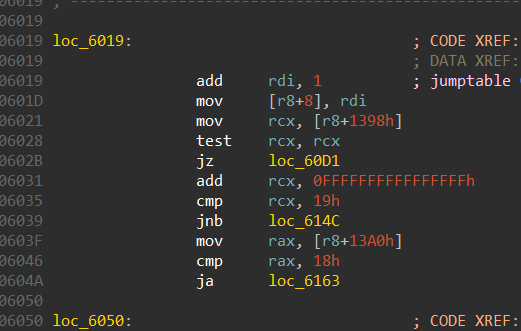
Similarly, case “j” is to go up, it does this by subtracting 1 from the x coordinate.
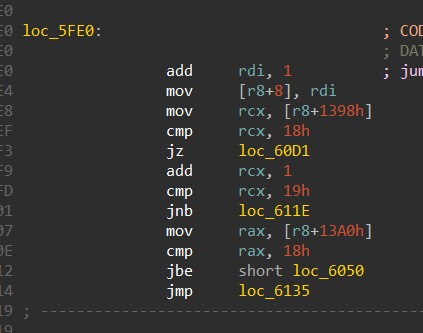
Case “k” takes care of going down the maze, it adds 1 to the x coordinate
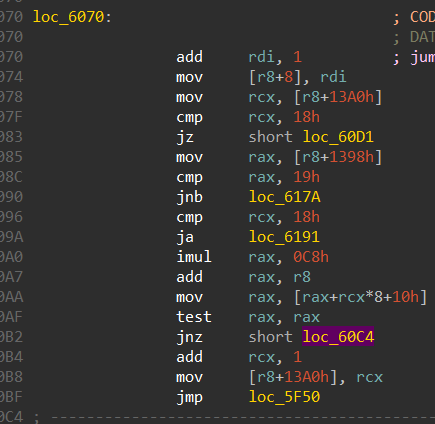
This case takes care of going right in the maze, it does so by adding 1 to the y coordinate
From this function we can also get the bounds of the maze which is 24 x 25, where there are 25 rows and 24 columns.
And the properties of the maze are,
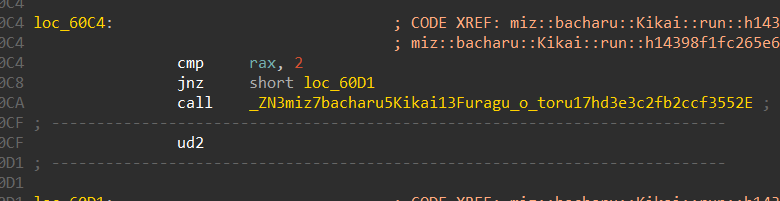
We can also see that this is the function miz::bacharu::Kikai::Furagu_o_toru::hd3e3c2fb2ccf3552 is the win function, and this is called when we traverse till we reach the number 2 in the maze.
Constructing the maze should be easy since we have its bounds,
1 | miz = [[1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1] |
The start position can be retrieved while debugging and it is (0, 13). The end position is
(24, 19)
To solve this maze we can make use of the python library mazelib
Here is the script,
1 | from mazelib import Maze |
The final moves to be sent as input comes out to be,
llkkhhhhkkkkhhhhjjhhhhhhkkllkkkkkkhhkkllkklljjlllllljjhhjjllllllkklljjllkklljjllkkkkhhhhkkkkllkkkkhh
Flag: inctf{mizes_are_fun_or_get}
tl;dr
strncat in merge allows for an overwrite onto the next regiontl;dr
Challenge Points: 245
Challenge Solves: 20
Challenge author: EvilMuffinHa
Solved by: AmunRha, Freakston, barlabhi
This is a simple VM which has around 25-27 opcodes with instructions simple enough to be emulated. This is a stack based VM.
The VM implements several constraints on the input bytes which can be solved using z3 SMT solver.
The VM implemented a puzzle called kenken
I chose python to write the disassembler in with several helper functions, at first I tried extracting the constrains one by one, which eventually worked, but then I was able to write a automatic extractor for the disassembly.
There were two files, one the binary and the data file in which the list of instructions contain.
This when fed to the z3 solution script will get us the required input.
Most of the operations take their operands from the stack, so there wasn’t much complexity in terms of implementation.
p.s. This will be a short write up
1 | def disasm(op, c): |
Commenting the lines specified can get us the extracted constrains.
I wrote a small parser on my disassembly which will get the proper constraints.
1 | equations = {"add_2":[], "add_3":[], "equate_3": [], "equate_4":[], "mod_equate_2":[], "sub_2":[], "equal_2":[]} |
There were in total 8 different constraints applied on the input bytes, which was added to z3.
1 | def set_idx(set_to): |
Running the script gives us the disassembly, and the extracted constraints
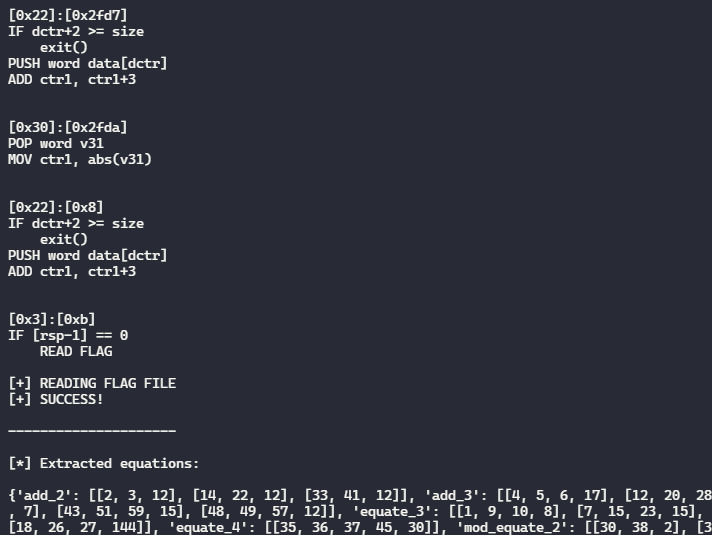
and pasting the extracted constraints to z3, gives us the input to be given,
pB738150rHt60714NP501s92420G3xUY013;Wo{=69h42Ob736B1y{@?1047uw`6
Sending this over the given nc connection, gives us the flag,
Flag: flag{kenken_is_just_z3_064c4}
Links to required files,
2k Disassembler Script - 2k_disassembler.py
Helper Script - helper.py
z3 solver script - z3_solver.py
tl;dr
__malloc_hook to one_gadgettl;dr
tl;dr
tl;dr
char candle counter stored in the wax structure and trigger uaf.tl;dr
tl;dr
1 / 2