tl;dr
- Finding Chat application
- Extract unread message count from NTUSER.dat.
- Extract the last executed timestamp of the chat application.
- Extract the Version of the chat application.
Challenge Points: 140
Challenge Solves: 45
Challenge Author: g4rud4
Challenge Description
Download the challenge file from here
MD5 Hash: ermittlung.raw 110305F3CF71432B4DFAFD1538CDF850
Initial Analysis
We are given with a memory dump. So let us find out the profile.
Finding Profile
1 | $ volatility -f ermittlung.raw imageinfo |
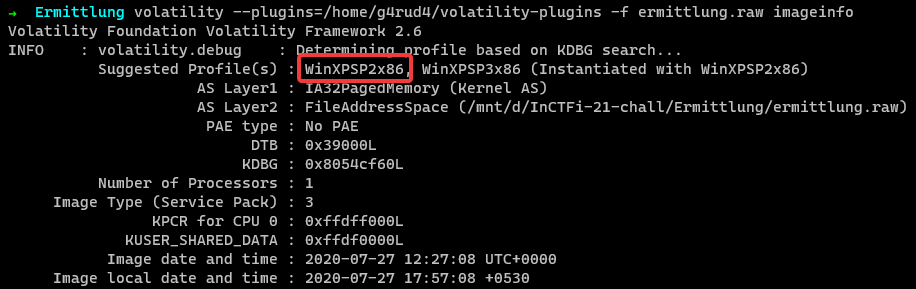
I will be using WinXPSP2x86, as the profile for this challenge.
Scanning active processes
As we don’t know what all processes were running during the memory capture. Let us check the active processes in the system for better understanding.
1 | $ volatility -f ermittlung.raw --profile=WinXPSP2x86 pslist |
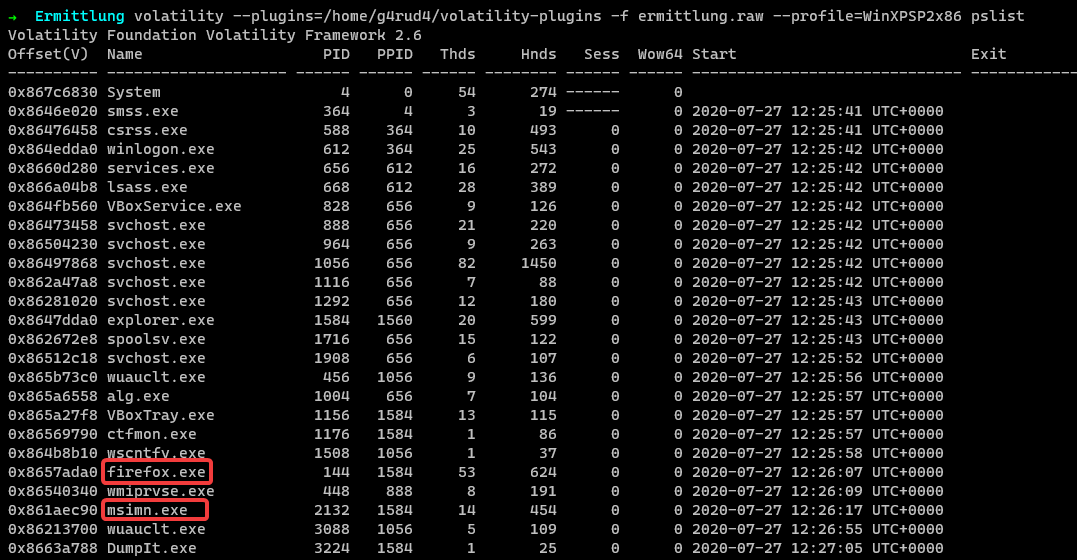
We observe firefox.exe, msimn.exe are running.
Listing Firefox history
Let us use firefoxhistory plugin to check any suspicious url. You can get this from superponible github repo.
1 | $ volatility --plugins=volatility-plugins -f ermittlung.raw --profile=WinXPSP2x86 firefoxhistory |
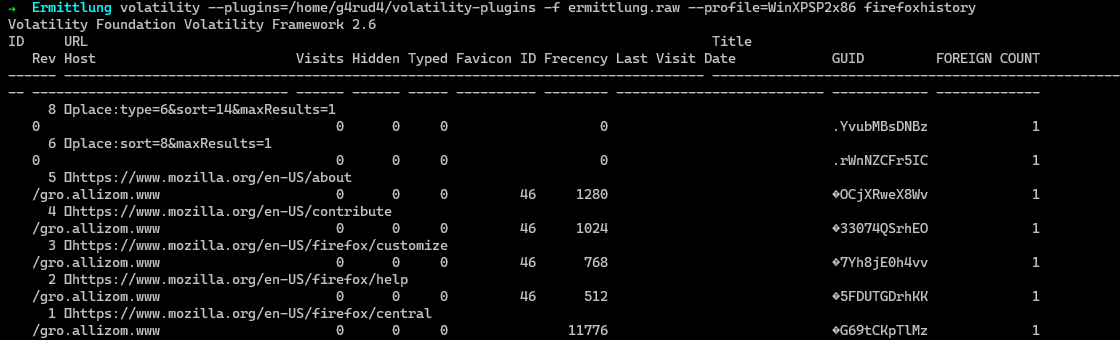
Well there is nothing much in it which we can make use of.
Answering 1st Question
- What is the name of the chat application program?
Finding chat application
We found msimn.exe, which a quick Google search or via using the plugin cmdline, we can find, this excutable is part of Outlook Express.
1 | $ volatility -f ermittlung.raw --profile=WinXPSP2x86 cmdline -p 2132 |
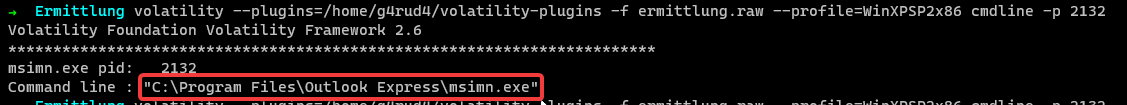
Other than this, we couldn’t find any other chat applications running on the system. We got our answer to the 1st question. Which is Outlook Express
We got the name of the chat application. Now, let us find out when was the last time this application executed.
Answering 2nd Question
- When did the user last used this chat application?
Finding Last execution time
We can find answer for this in 2 ways, One by checking the start time from the pslist and another from registry.
PsList
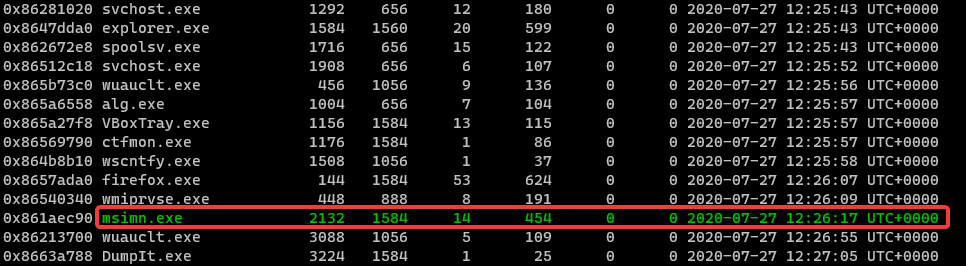
Registry
Using UserAssist from NTUSER.dat, we can also find the last executed time of Outlook Express. Let us use userassist plugin.
1 | $ volatility --plugins=/home/g4rud4/volatility-plugins -f ermittlung.raw --profile=WinXPSP2x86 userassist |
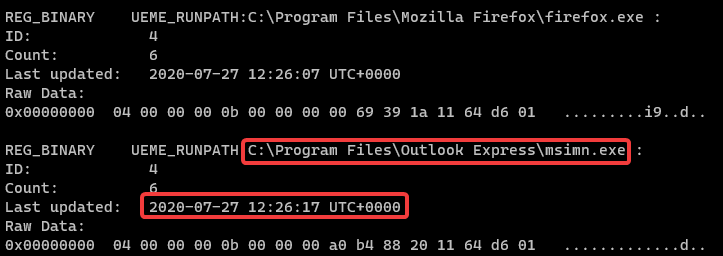
As highlighted, we get the last execution time as 2020-07-27 12:26:17. Converting that to the format mentioned in the description would result in 27-07-2020_12:26:17.
Answering 3rd Question
- How many unread messages are there in the chat application that the user is using?
Finding message count
We find the message count from NTUSER.dat registry hive. Let us dump the NTUSER.dat registry hive.
To dump the registry hive, 1st we need to find the virtual address of the NTUSER.dat. For that we can use hivelist plugin and list all hives.
1 | $ volatility --plugins=/home/g4rud4/volatility-plugins -f ermittlung.raw --profile=WinXPSP2x86 hivelist |
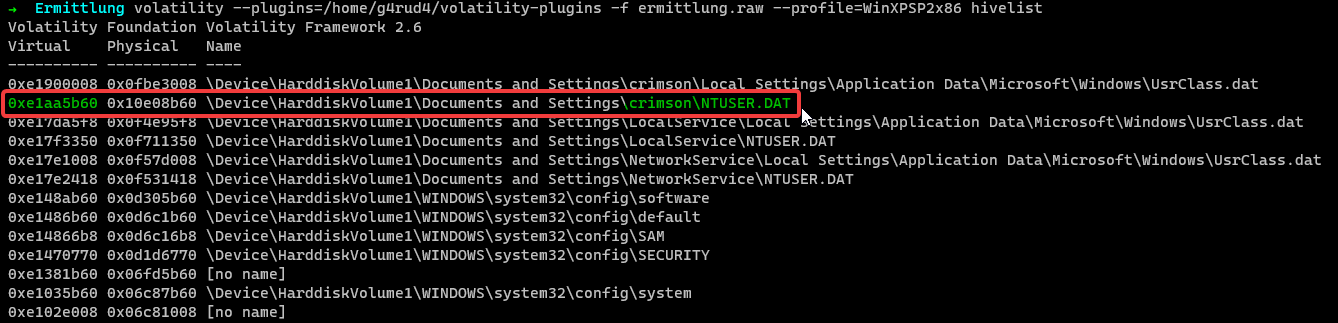
NTUSER.dat is located at 0xe1aa5b60 offset, now we can use dumpregistry plugin to dump the registry hive.
1 | $ volatility -f ermittlung.raw --profile=WinXPSP2x86 dumpregistry -o 0xe1aa5b60 -D output |
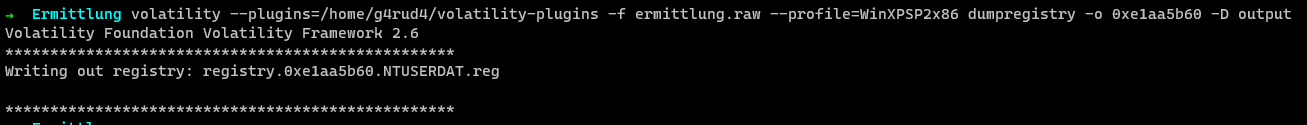
We can use our preferred registry viewer to open the dumped registry hive.
We can got to this Software\Microsoft\Windows\CurrentVersion\UnreadMail\ hive, where we can find the count of unread messages under the email used in Outlook Express.
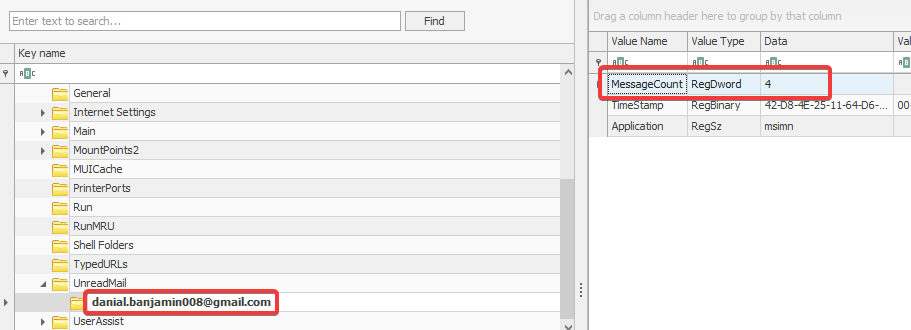
From the register, we get Message Count as 4.
Note: We can also use volatility’s printkey plugin to retrieve the Message Count from registry.
Answering 4th Question
- What is the current version of the chat application that’s being used?
Finding version of chat application
Version that the chat application is using can be found in NTUSER.dat or by dumping the process from memory and checking out the little endian strings.
From Registry
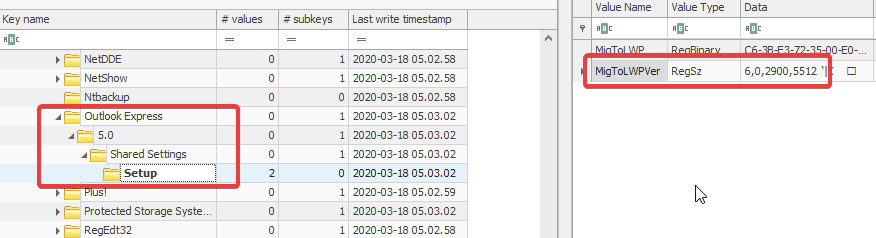
As we have already dumped NTUSER.dat registry hive, we can got this Software\Microsoft\Outlook Express\5.0\Shared Settings\Setup hive, and the sub-key MigToLWPVer gives us the version of the chat application being used on the system.
From Process dump
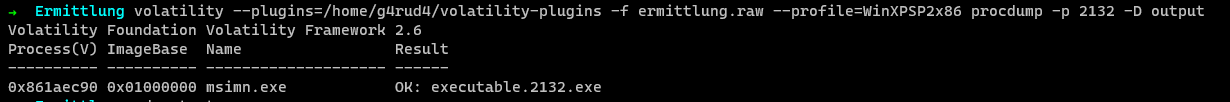
From the pslist we can see that the executable is running at PID 2132. We can use procdump plugin and dump the process.
1 | $ volatility -f ermittlung.raw --profile=WinXPSP2x86 procdump -p 2132 -D output |
Now, we can use strings commands, to get all the little endian strings from the dumped executable.
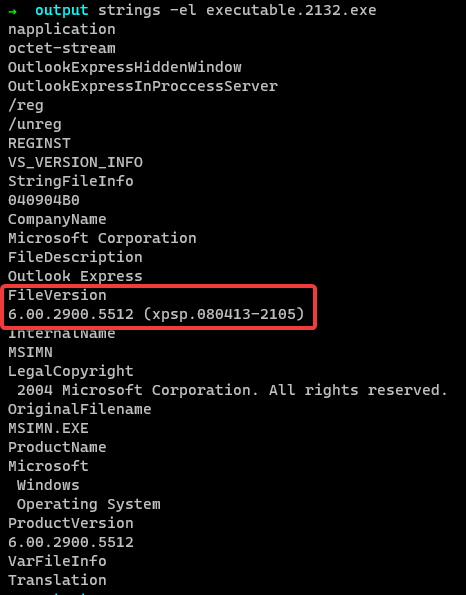
As highlighted, the version of the application is 6.0.2900.5512.
Flag
Concatinating all answer, we can get the flag.
inctf{Outlook_Express_27-07-2020_12:26:17_4_6.0.2900.5512}
For further queries, please DM on Twitter: https://twitter.com/_Nihith