tl;dr
- Finding the last modified timestamp of the file that maps names to IP’s accessed.
Description
As the description says, we need to find the last modified time of a file that maps DNS names to IP’s recently accessed.
I don’t have much knowledge on Mobile Forensics. It is time to sharen my skills on Mobile Forensics. Magnet Forensics has decided for a weekly CTF, new challenge every Monday for the last quarter of 2020. You can find more info in the blog post released by Magnet Forensics.
Initial Analysis
With my limited experience in Mobile Forensics, I started to look for hosts file as it is responsible for mapping IP’s to DNS names(Similar to Windows and Linux).
Let’s go a head and load the Android Image in Autopsy. You can download the image here.
If you don’t know how to load an Android Image in autopsy, found this blog post and followed that and loaded the image in Autopsy.
After loading the android image in autopsy, on checking the files present on the device, I found something intersting in Downloads folder(/data/media/0/Download).
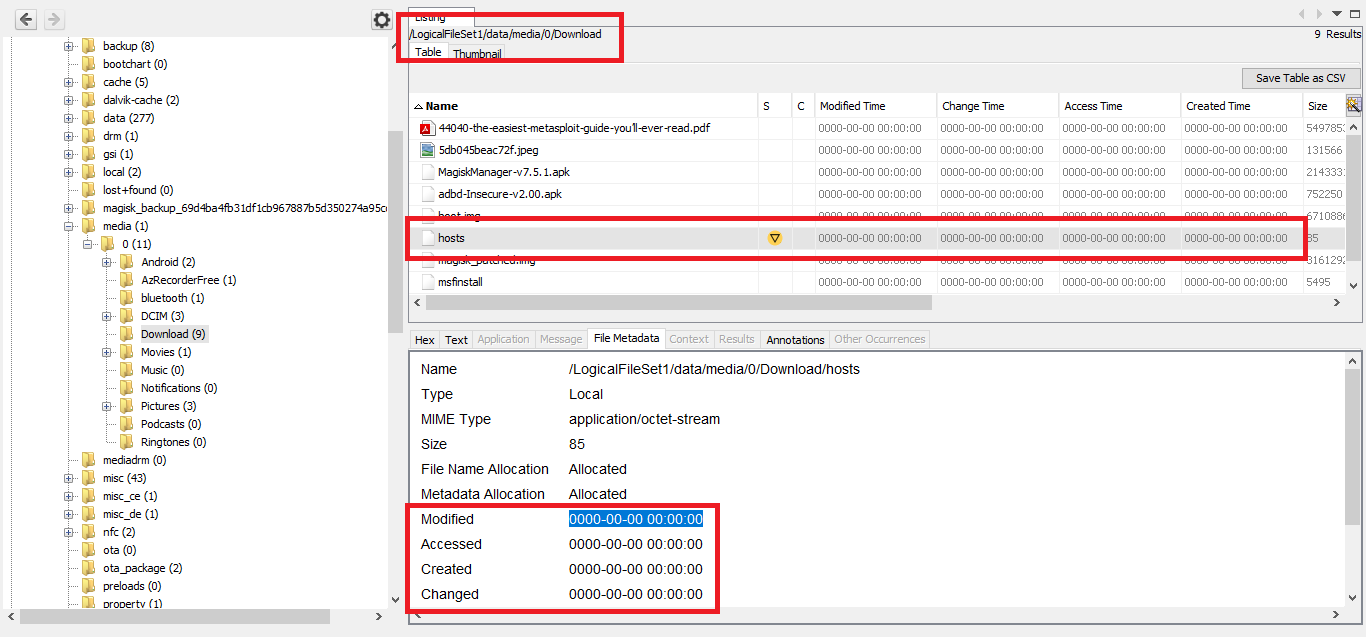
This seems to the required hosts file, Normally it won’t be stored in any local folder, So to confirm I searched for the hosts file location in android device.
Retrieving hosts file
Upon seaching for the hosts file location, got hit, saying that it will be stored in /device/system/etc/system.
When I checked it, etc folder is not there in the mentioned location.
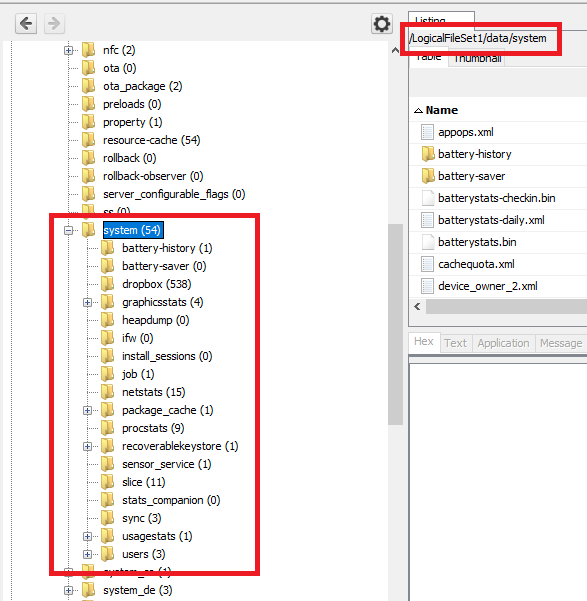
Upon searching and got an another hit saying that it will be stored in adb folder of the image.
Location: /adb/modules/hosts/system/etc/hosts
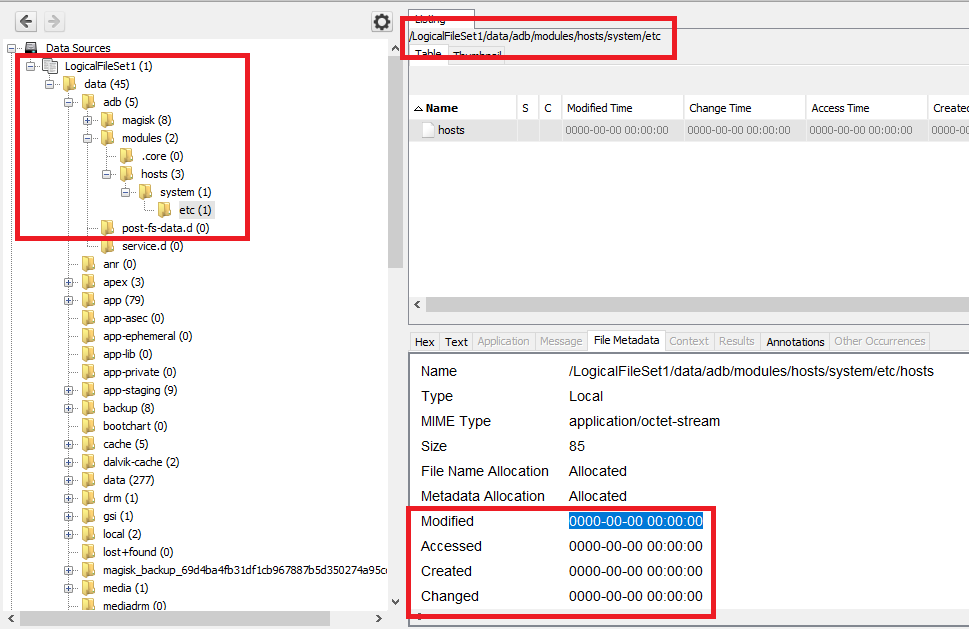
In the same way I am not able to view the metadata on Autopsy for that file.
As I have extracted the tar file, I went to that location and viewed the metadata of that file.
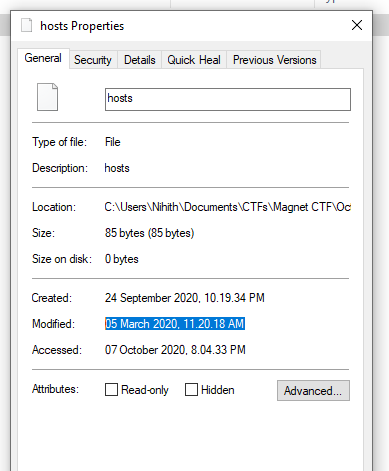
Upon converting the timestamp 05 March 2020, 11.20.18 AM from IST to UTC, we get 05 March 2020, 05.50.18 AM
Flag
03/05/2020 05:58:18