tl;dr
- Decrypt the encrypted GPG file found in Outlook Express with the private key stored on the device.
- Decrypt the firefox saved passwords and log in to the website that the terrorist used.
Challenge points: 627
No. of solves: 30
Challenge Author: g4rud4
Challenge description
You can download the challenge file from Mega or Google Drive.
Initial analysis
We are provided with an E01 file(Expert Witness format image). There are a lot of ways in analyzing these files, I choose to use Autopsy for analyzing this. Let’s go ahead and load our E01 file in Autopsy. You can visit Autopsy’s documentation if you don’t know how to add a data source to autopsy.
From the description, we have a clue that the terrorist is using a genuine chat client, lets see what all applications are installed in the device.
As we know, all the applications present on the device can be found in Program Files. Some of the applications we need to check are GPG, Mozilla Firefox, NetMeeting, Outlook Express. Let us dig more into it and check if they have identified and configured.
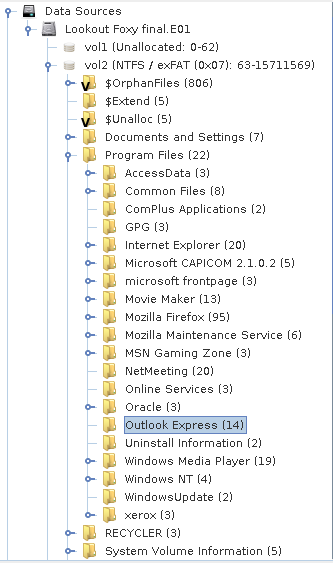
So by checking application data, we can say that Outlook Express and Mozilla Firefox are configured. Let us dig more into them.
First part solution
As the Outlook Express is configured on the device, it leaves us useful forensics artefacts on the device.
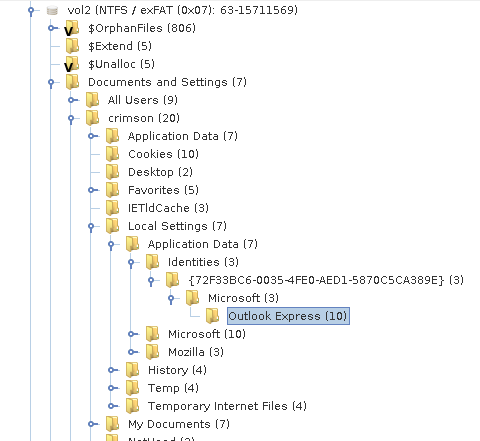
Some of them are the emails received and sent. Whenever we receive a mail or delete a mail or sent a mail it will be stored in a .dbx files. Ex: for Inbox Emails - inbox.dbx, Sent Emails - outbox.dbx etc.
These files are stored at C:\Documents and Settings\Crimson\Local Settings\Application Data\Identities\{random characters}\Microsoft\Outlook Express\
In our case, these are stored at C:\Documents and Settings\Crimson\Local Settings\Application Data\Identities\{72F33BC6-0035-4FE0-AED1-5870C5CA389E}\Microsoft\Outlook Express\
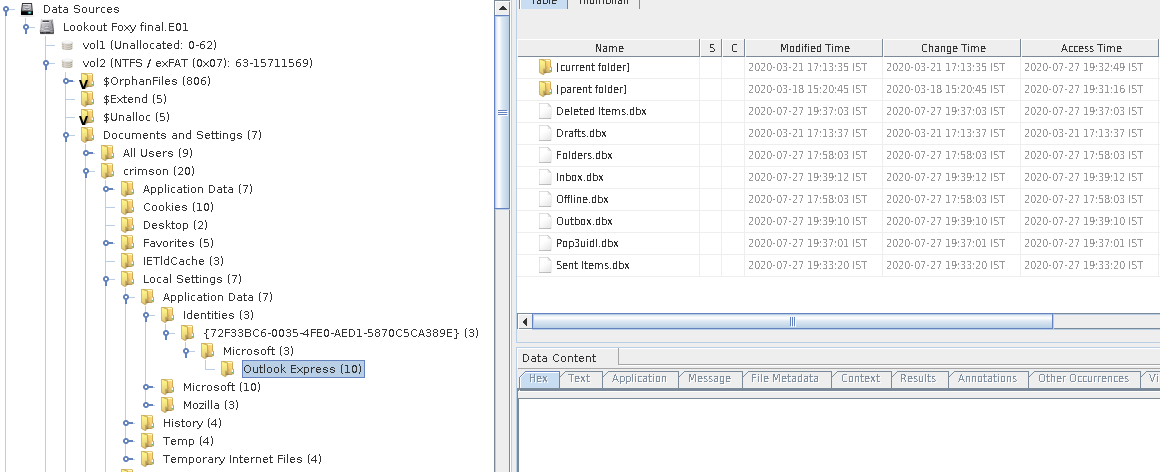
You can see .dbx files being listed there on right. We know that we can’t view the messages stored in DBX files. So I have converted the DBX file into a PDF file using this link. There are other ways too, as this gives us something similar to the GUI, I used this. And one of the best things is to do strings on the DBX files.
Converting the Inbox.dbx to PDF, One will be able to see that there is a mail from David Banjamin davin.banjamin@gmail.com with a subject Secret File. And a file named secret.gpg has been attached.
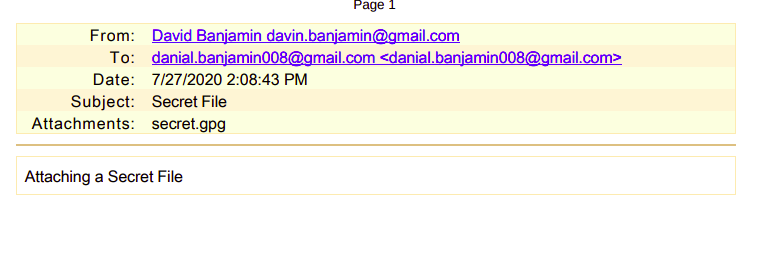
We can get this file by a simple keyword search in Autopsy or check below.
So these attached files are stored in this location, unless the user saved it into a specified location C:\Users\{username}\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\{random characters}.
We have 4 directories listed there, so rather than traversing through all directories, I used Autopsy’s Web Downloads Result. There we can see that there is a secret.gpg.Zone.identifier file. These Zone identifier files are generated automatically by applications/programs when files are downloaded to a Windows computer. So by checking the Source file path we can get the random characters. So going into that directory(U0PDHEH3), we can get the secret.gpg file easily.
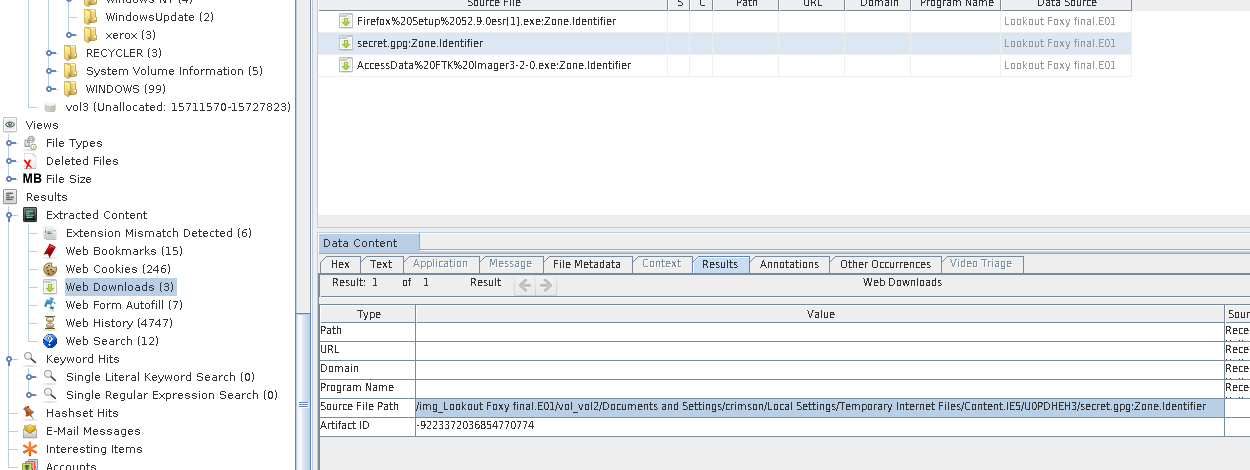
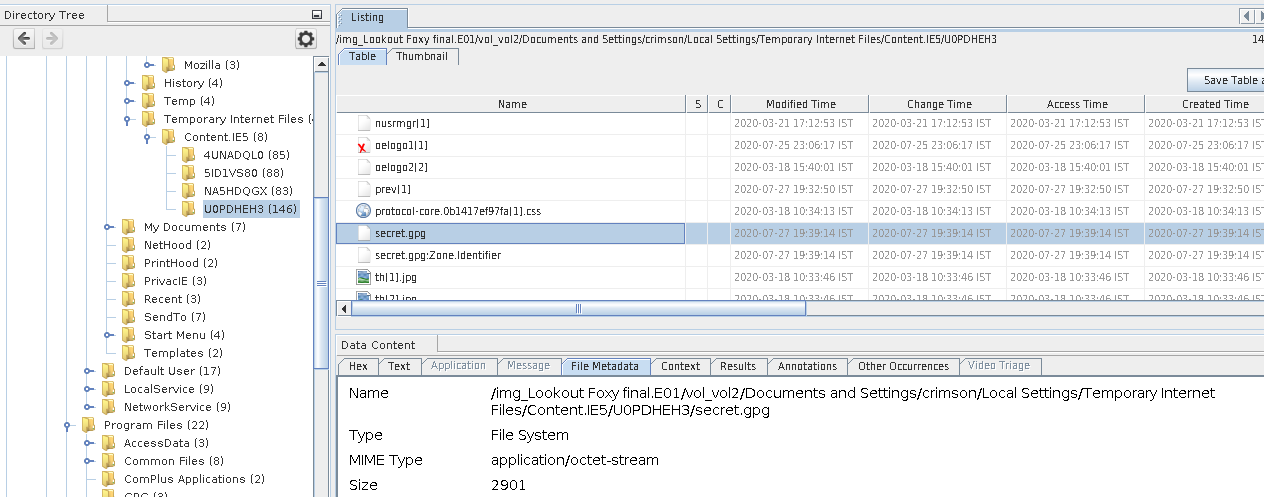
We know that the gpg files can only be decrypted by the Owner’s private key. As we have seen a directory named GPG while traversing through the program files. Going into this directory we can find the secret.key.
Importing the private key and decrypting the encrypted GPG file, we can get the first half of the flag.
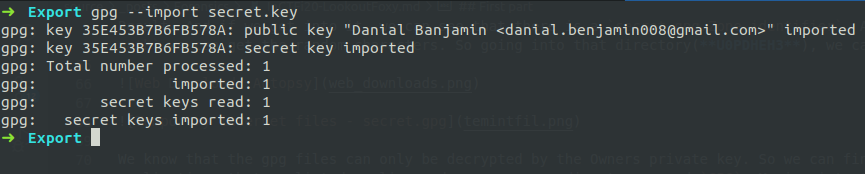
1 | $ gpg --decrypt secret.gpg |
Snipping the output,
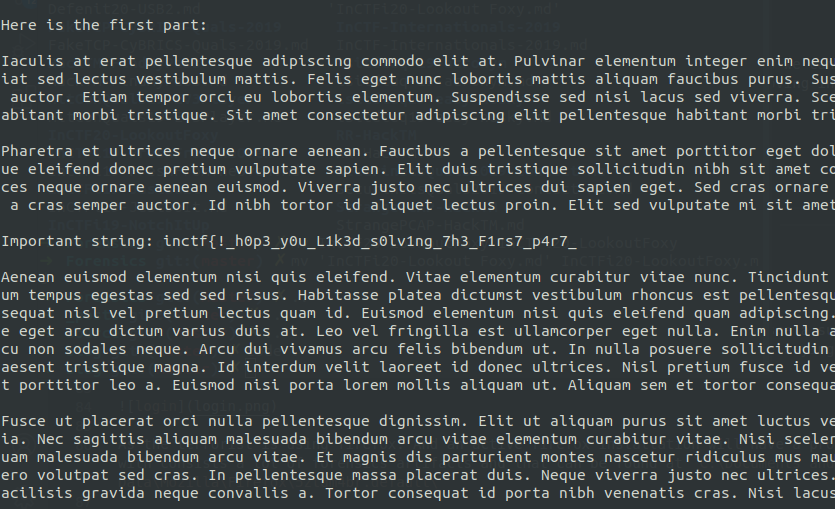
First half: inctf{!h0p3_y0u_L1k3d_s0lv1ng_7h3_F1rs7_p4r7
Second part solution
As we see that there are a lot of web searches listed out in Web History results in Autopsy and going through them we can see a suspicious link http://35.209.205.103/ in the history. So going to that link there is a login page. And there is a note saying Don’t brutefore the Password. So the password must be saved somewhere.
As the terrorist is using firefox. And an active firefox installation will have a profile(in our case - 5ztdm4br.default) which consists of a lot of forensics artefacts and that can be found generally at C:\Documents and Settings\{Username}\Application Data\Mozilla\Firefox\{random characters}.default\. In our case, these are found at C:\Documents and Settings\Crimson\Application Data\Mozilla\Firefox\5ztdm4br.default\
By Checking the Web Form Autofill results in Autopsy or by looking at the formhistory.sqlite database present in the firefox profile, we were able to see that the username as Danial_Banjamin and we need to find out the password.
As the username and password are stored in formhistory, that means passwords are stored in firefox saved passwords. We need to decrypt the saved passwords to get the original password.
Here comes the interesting part of decrypting Firefox saved passwords. There are a lot of ways
- By dumping the whole profile and passing the dumped folder location to firepwd.
- By dumping only the required files from the profile.
I am choosing the second way and here are those files:
logins.json - Place where all login information such as encrypted username and password are stored.
cert8.db and key3.db/key4.db - These are encrypted SQLite database files, and the entries
encryptedUsernameandencryptedPasswordfound in logins.json are encrypted with the keys found in both databases.Permissions.sqlite - It contains permissions for installing add-ons, cookies, etc.
After dumping all these files from the firefox profile mentioned above, I used pwdecrypt to decrypt the password. It’s a Debian package and can be installed by with apt.
1 | $ sudo apt install libnss3-tools |
Then, I used a JSON parser(jq) to parse the JSON file and redirected the output to pwdecrypt.
Here is the JSON parsed output of logins.json.
1 | $ jq . < logins.json |
As we are having so many entries, and we only need the username, password and URL. So added those entries to JSON parser and redirected it to pwdecrypt.
1 | $ jq -r -S '.logins[] | .hostname, .encryptedUsername, .encryptedPassword' logins.json | pwdecrypt -d . |
As the master password was not set by the terrorist we were able to get the decrypted password. So logging in using those credentials gives the second part of the flag.
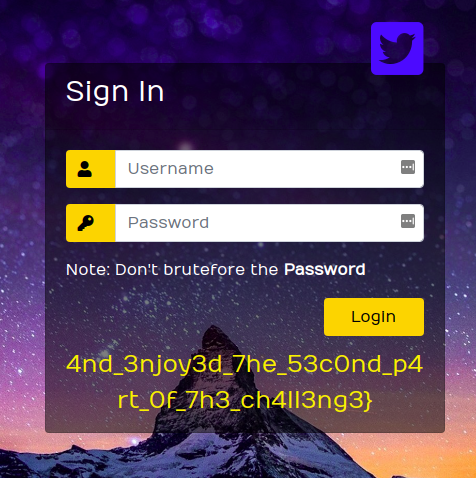
Second Part of the flag: 4nd_3njoy3d_7he_53c0nd_p4rt_0f_7h3_ch4ll3ng3}
Flag
By concatinating two parts, here is the final flag:
inctf{!_h0p3_y0u_L1k3d_s0lv1ng_7h3_F1rs7_p4r7_4nd_3njoy3d_7he_53c0nd_p4rt_0f_7h3_ch4ll3ng3}
If you have any queries, Feel free to ping me. I am available on Twitter @NihithNihi
References
Here are some of the resources I came up while making the challenge. Hope it will be useful.