tl;dr
- SSTI in the valentine card
- bypass filter by setting ejs delimiter option
- RCE :yay:
Challenge Points: 80
No. of solves: 116
Solved by: sk4d
intro
I played hxpCTF 2023 last weekend with my team bi0s. There a were a lot of awesome web challenges. I have worked on most of the web challenges and this is the write-up for the challenge valentine
Initial analysis
The application lets us to create a fully customisable valentines card. The application asks us to personalize our card using the <%= name %> tags and it gets replaced with the value in the name parameter we send to the template, this can be seen in the source
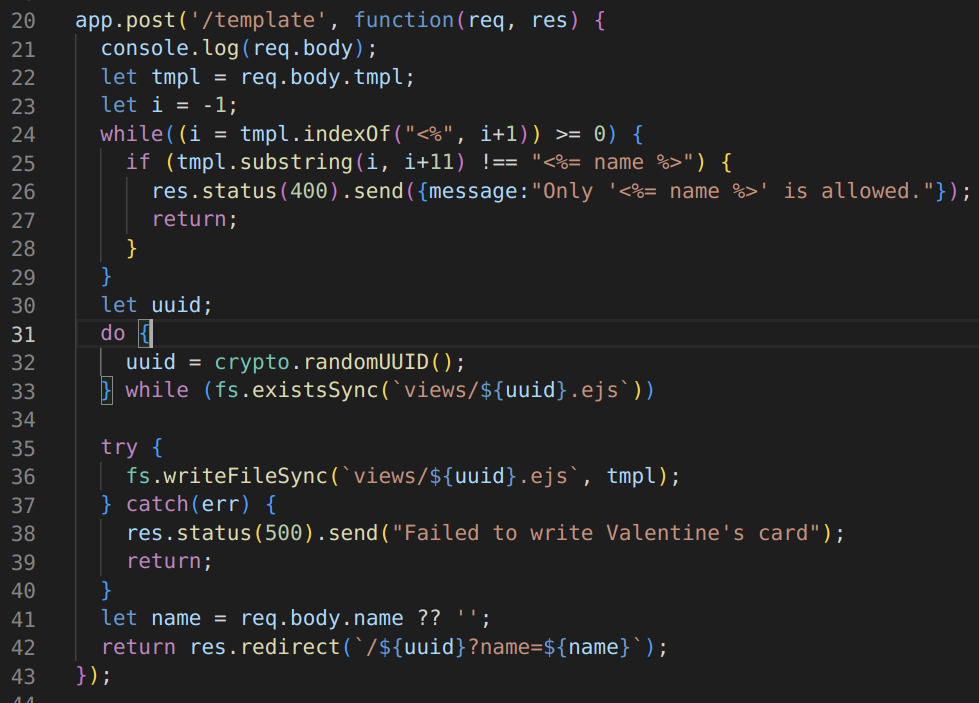
here we can see that our input is passed to the tmpl varible on line number 22 and then on line number 36 , tmpl is written to a ejs template file. This template is later rendered
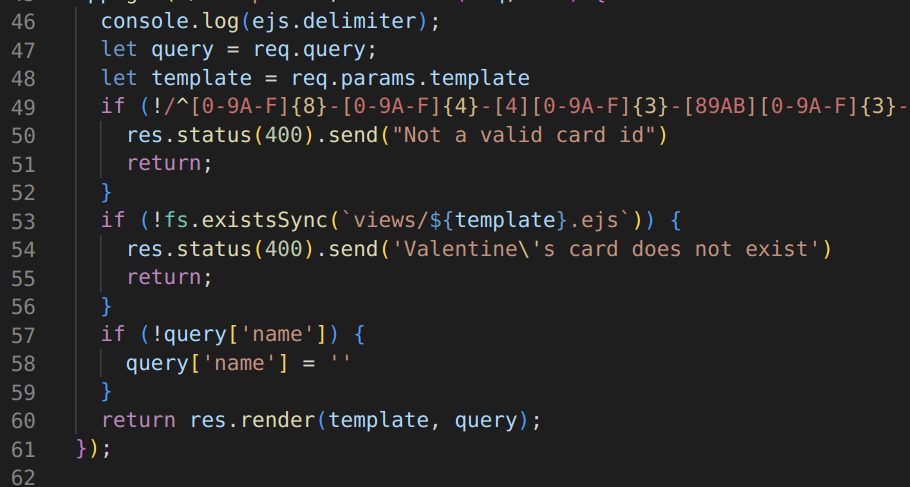
in line number 60 which results in an ejs SSTI. This looks easy but no :) there is a filter on line number 24 which blocks every templates other than <%= name %>
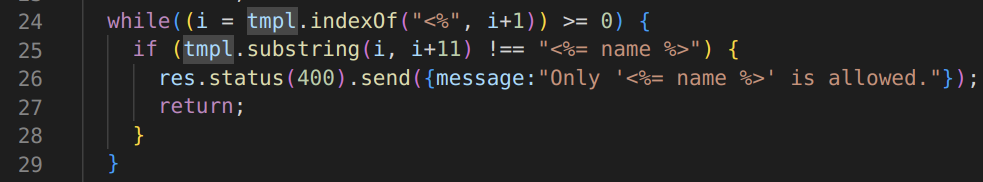
this filter checks for the occurences of <% in our template and from there takes the next 11 characters and checks if it matches the string <%= name %> and if this check fails the program returns 400. So we basically can’t pass anything other than <%= name %> in our template.
Exploitation
We found this interesting blog by Eslam Salem which explained an interesting feature in ejs which allows us to overwrite the template options with the request parameters. This happens because ejs merges our parameters with the options object if the options object is empty and our request has valid option names as params
libs/utils.js:135
1 | var _OPTS_PASSABLE_WITH_DATA = ['delimiter', 'scope', 'context', 'debug', 'compileDebug', |
we can see the option called delimiter which enables us to use custom characters in our ejs tags to make templates, You can read about the different ejs options here. This is exactly what we were looking for and we can use this feature to bypass the filter in line 24 by setting a custom delimiter like delimiter=? and then we can execute payloads like <?= process.mainModule.require(\'child_process\').execSync(\'/readflag\').toString() ?> to read the flag
Payload
1 | curl -i -s -k -X $'POST' \ |
1 | curl -i -s -k -X $'GET' \ |
flag
1 | hxp{W1ll_u_b3_my_V4l3nt1ne?} |
Closing thoughts
Thanks to the hxpCTF 2022 -_(0_0)_- organizers. The challenges were fun and we learnt a ton :)