
Team bi0s is a student-run cybersecurity club of Amrita Vishwa Vidyapeetham, Amritapuri (Kerala). The club is focused on building students and individuals with interdisciplinary skills in the field of cybersecurity and has a prosperous history spanning more than a decade. The team has been the top performer in the well-known cybersecurity contest - ‘Capture The Flag’, in the national and international arena.
Our mission to teach and improve cybersecurity awareness has never been more urgent and necessary. In the past year alone, we’ve seen huge changes in the way people live and interact with computers, with the pandemic being the catalyst to it. The digital landscape is changing, so is teambi0s. The hard work and the commitment of the members of teambi0s translated into meaningful results and progress of the club. The Year in Review 2021 reflects a few.
Year 2021
Around the world, 2021 was about revival. As the world started to crawl back into normal daily life, away from the proliferating virus which kept coming back in different variants, things slowly looked up far away from the lethargic progress we had in the previous year. For teambi0s, the year was also about rejuvenation. We acted proactively through the chain-reaction of unprecedented events that the continuing pandemic had bestowed upon us, improving the team spirit and culture, ending the year with prodigious achievements, insights, and progress.
The team wrapped the year up as the best CTF team in the country and 28th worldwide, according to CTFtime‘s official ranking charts. We were placed firmly in the top 10 for many of the best international CTFs. We were at the top of the scoreboard for YASCON CTF, runners up for the year’s ISFCR Hackathon, 5th for TAMU CTF, 6th for b01lers CTF, 7th on ISITDTU CTF Finals, and 8th on Aero CTF.

bi0s was invited to attend and play the onsite Volga 2021 finals, which was an international inter-university CTF. Volga is a high-profile, international jeopardy-styled CTF conducted by a group of IT enthusiasts based in Samara, Russia. Nearly 300 teams registered for the CTF worldwide, including the most prestigious teams who have been pioneering in the field of cybersecurity and research. The finals was scheduled on September 16, where the team finished in the 16-th position on the scoreboard. Our members Jaswanth Bommidi, Pranjal Singh and Sourag K flew to Russia and participated in the contest.
For the year’s DOME CTF, two members of the team: Prajwal C P and Adhithya Suresh Kumar brought the trophy home. DOME CTF was a premier CTF tournament held at the c0c0n cybersecurity conference with the support of Beagle Security and Kerala Police Cyberdome. They received a total of 50,000 rupees as the grand prize for the same.
Furthermore, Prabith Gupta got into IDCSS 2021- the Indian Dutch Cyber Security School. He attended a few weeks of talks from professional speakers around the globe and his team project was presented at the conference. And Adhithya Sree Mohan from the binary exploitation team was selected for the winter school for ‘Security, Privacy and Trust in Cyberspace’ conducted by IIT Bhilai and ACM.

We hosted InCTF Nationals, InCTF Junior qualifiers, and the conference and finals to be held in January 2022, completely online, just like from the previous year.
In 2021, InCTF attained new heights with more than 10,000 registrations from all across the country. A new breed of the game named InCTF Professional was also realized, aimed at security professionals and members of the industry.
In the second week of August, we hosted InCTF Internationals - bi0s’ premier hacking event targeted at hackers of all ages. As always, the challenges of the event were responsibly innovated and loaded with the latest vulnerabilities to help the players stay current and have an enjoyable time and experience. At CTFtime- a popular CTF players’ community, InCTFi received a weight of 54 along with enough feedback and insights to do better next time.

Among the technical companies who sponsored InCTF and InCTF Junior, CBSE (Central Board of Secondary Education) had also supported and co-organized the CTF and the conference with bi0s. With CBSE, we are positive that we were able to inspire more students than ever before through InCTFj 2021.
As always, we pledged to create a fair, engaging experience for the participants, spectators, and first-time players, proudly honoring the legacy and lineage of InCTF and we believe that we ended up doing so. At our deepest core, we are honored to see CBSE and all our sponsors, believing in the vision and the purpose of InCTF and InCTF Junior.
Team Shakti, our girls-only team organized Shakti CTF- a CTF exclusively for women and ShaktiCon conference aimed to train and support women from all over the globe in the area of cybersecurity. Both were a huge success and attracted a lot of young girls into cybersecurity. This time, ShaktiCon had a huge list of speakers from even outside the tech industry, making it an exciting and rewarding experience for many.

Two members of Team Shakti - Simran Kathpalia and Namitha S presented a talk at The Diana Initiative- which is a conference committed to helping all the underrepresented communities in Information Security.
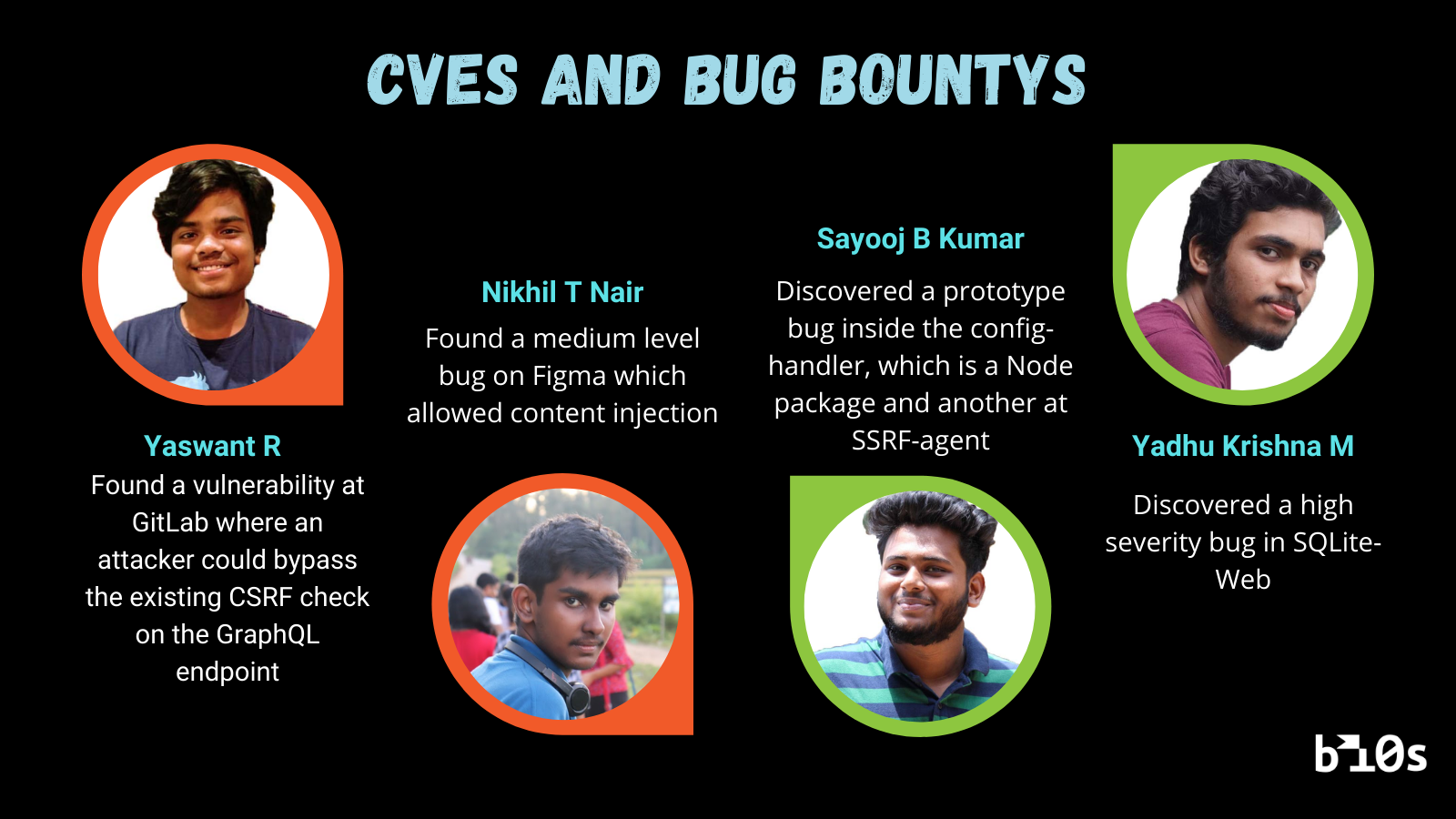
Speaking about achievements in vulnerability research. Our members,
- Yadhu Krishna M discovered a high severity bug in SQLite-Web and also found numerous bugs at web services of Kalyan Jewelers.
- Sayooj B Kumar discovered a prototype pollution bug inside the config -handler, which is a Node package and at ssrf-agent. Both were awarded a CVE (Common Vulnerabilities and Exposures) for the discoveries.
- Yaswant found a vulnerability at GitLab where an attacker could bypass the existing CSRF check on the GraphQL endpoint. He also received a bug bounty for his findings.
- Nikhil Nair discovered bugs in Figma, which included Several High severity bugs.

From the humble inception of the team, the members also had been regularly participating in open source development and are always advised by our mentors to help the international software community when possible. This year, four members of the team did their Google Summer of Code project at various organizations.
- Vishnu Madhav worked on GCC compiler tools.
- Pranjal Singh worked at Xen, which is under The Honeynet Project.
- Simran Kathpalia enhanced syzkaller support for the FreeBSD kernel at FreeBSD Project.
- Aswin C added support for CPU and platform profiles at Rizin Organization.
Additionally, 11 members of the club got selected to attend BlackHat USA and Europe Conference in 2021. Namitha, Nidhin, Shravya, Aiswarya, Adhithya, Arya, Nikhil, Abhishek, Vishvesh, Akshith, and Gourav attended the trainings and the workshops from various cybersecurity experts around the globe.
Our Digital Forensics team bagged the second rank among the international teams in the 5 months long Digital Forensics challenge (DFC) organized by Korea Institute of Information Security & Cryptology (KIISC). The team consisting of Abhiram Kumar P, Jaswanth Bommidi, Bolisetty Krishna Sai Nihith, Anand Balaji, Pranav Nair, Sridevi K, Arya Arun, Goutham Rajesh, G Sai Sampath, S Abhishek participated and solved challenges varying from different branches of digital forensics, ranging from steganography, multimedia forensics, operating system forensics (Linux, Windows, and Android), memory forensics, shellcode analysis, reverse engineering, malware analysis and from other similar domains.
DFC started on the 1st of May 2021 and concluded on 30th September 2021. The Digital Forensics Challenge had 24 challenges with varying points from 100 to 500 and 4-5 challenges released each month.
Our members were also invited to present their work at the Annual International Digital Forensics Workshop, held on November 5th in Seoul, Korea.
Pentest Team

Varun Nair and Abhishek Sidharth, members of the penetration testing team became a Certified Red Team Professional (CRTP) by Pentester Academy. They are the first members of the team to do so and had to go through 32 days of learning and complete a 24-hour attack lab to gain the certification.
Meanwhile, Abhishek Sidharth found an Arbitrary Code execution bug at Tenable and was awarded a CVE for it. He also received a bounty from Google and Synack for the vulnerabilities that he had recently discovered.
The pentest team’s Anjana Suresh got a training scholarship from WiCyS- a global community of women in cybersecurity.
Furthermore, Abhishek Praveen from pentest secured 3rd place in the SANS and DreamtoSucceed CTF. He got access to a SANS security course and a free attempt at GFACT certification at the prize.
Hardware Team

The members of the Hardware team: Nidhin Naushad, Athul Menon, Aswin C, Ranit Pradhan had participated in the IEEE National RFID Challenge 2021 conducted by IEEE RFID TA in collaboration with CRFID, IEEE YP India Council, and IEEE RFID Council Kerala Chapter, and the team was the runner up of the competition. Their project prototype was vaccine verification using RFID-based secure authentication, and Nidhin got a chance to present the work at the 11th International IEEE RFID TA Conference.
The team also got into the finals of the CSAW Embedded Security Challenges (ESC). This year’s ESC was based on Side-Channel Attacks and Fault Injection Analysis using ChipWhisperer Nano. They got a chance to present their work at the CSAW conference.
Team projects and Personal achievements
When talking about R&D, our members:
- Pranjal Singh and Vishnu Madhav developed a Python module for demangling function names for executables written in the Rust programming language. The tool is a port to Python and makes reversing and scripting on rust binaries much easier.
- Abhiram Kumar developed a forensic tool that could parse vital forensic information from the EventTranscript database and other similar databases containing Windows Diagnostic Data.
Coming to internships, FTE’s and other employment opportunities:
- Our members: Aditya Vardhan Padala, Ritvik T, and Suraj K Suresh got a chance to spend their summer at Payatu as security research interns.
- Suraj had also won the FlareOn belt buckle from FireEye- which was the award for completing the eighth annual FlareOn challenges.
- Sourag C, a member of the binary exploitation team, did his internship at Secfence, an Information Security research company.
- Akul Pillai, Geethna TK, and Ayushi Sharma got into Purdue University as research scholars.
- Saastha Vasan started his Ph.D. at the University of California, Santa Barbara (UCSB), and Siddharth Muralee, Ashwin Nambiar started their Ph.D.’s at Purdue University, Indiana.
- Nikhil T Nair, Yaswant, Meenakshi SL got into VMware, and Sandra Bino and Geethna TK got into Hackerone.
Team bi0s is evolving. The club is dynamically progressing through the perils of the pandemic and the repercussions of being remote. Even between these sweeping, swift changes, the legacy and the lineage of teambi0s remains unchanged; the team’s comradery attitude to progress and to improve the team and the general notion to help, teach and espouse cybersecurity remains as unaffected as humankind’s quest for the final frontier.
