tl;dr
- Challenge is a Nintendo GameBoy ROM image.
- Reverse the ROM and figure out the implementation
- Analyze the calling function’s checks to find the path along which we must move.
Challenge points: 936
No. of solves: 13
Challenge Authors: officialcjunior and k4iz3n
Challenge description
Move the flag in just the right ways or just hack the game!
Initial analysis
We are provided with a single file: a 256Kbit Game Boy ROM image.
In the absence and impracticability of using the actual hardware, we’ll load it up on a GameBoy emulator.
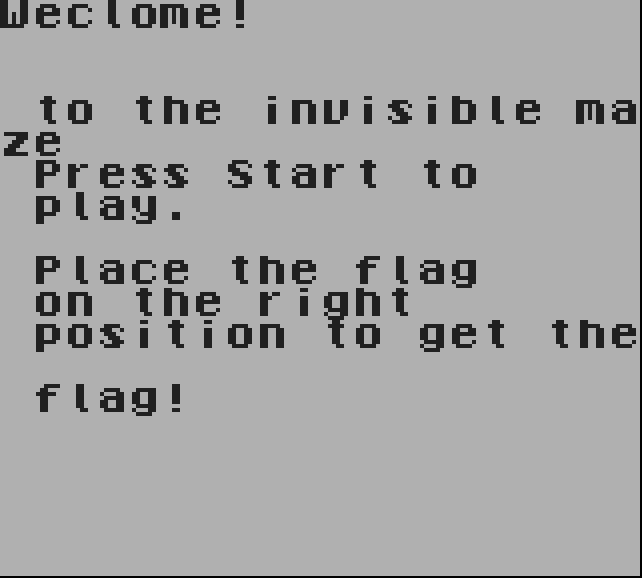
After the splash screen, you’ll be greeted with the challenge description and then, a screen with a movable flag. Briefly speaking, we just need to find where the checks are being done, which in turn track the movement of the flag.
On further reversing, you’ll find checks like the one below, quite often.
1 | 0x00000ace fe0f cp 0x0f |
Adding this to what the description suggests, we can imply that they are checking the position of the flag on the screen. And going 15 pixels to the right and 10 down from zero, which is at the top left corner, the game makes a different beep compared to the normal beep.
Similarly, while moving through the other five positions, the game makes the different beep. They are the positions through which the flag must be moved.
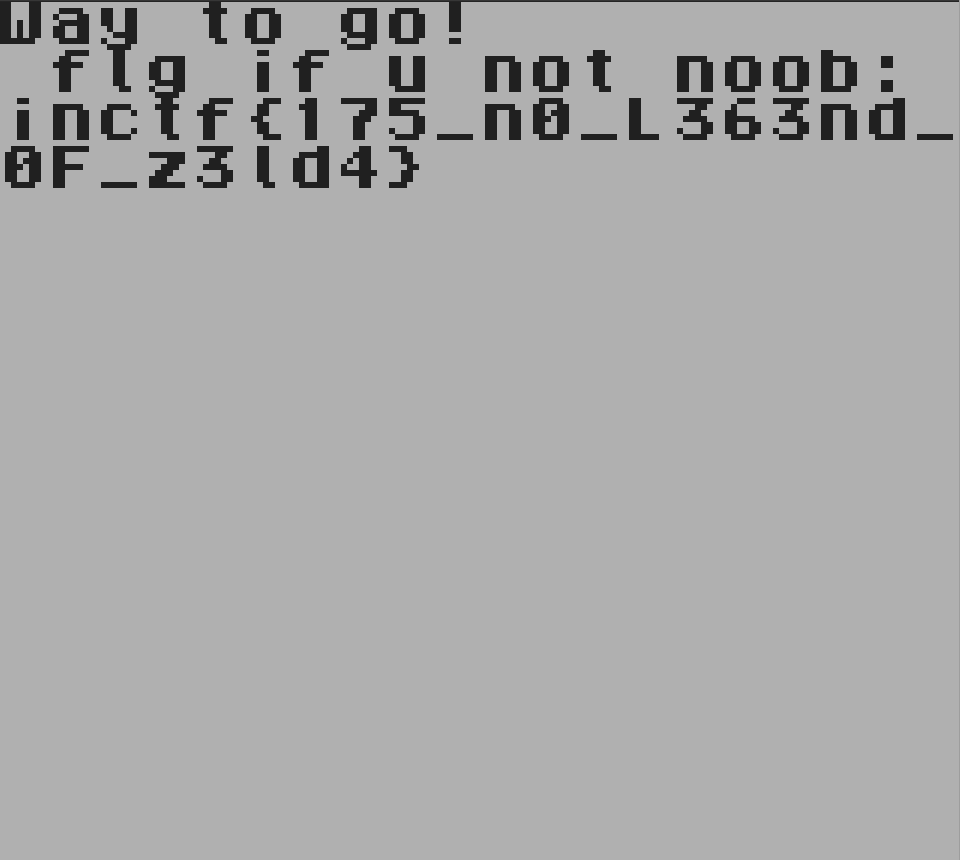
After passing through all the checks, you’ll be greeted with the flag.
Side note
It can also be inferred that at the function at 0x0000200 is the one which is generating and printing the flag. And the arguments passed to it, the position of the flag, are of the type Ubyte (8-bit unsigned bytes), which makes it possible to brute force all the possible combinations.
Flag
FLAG: inctf{175_n0_L363nd_0F_z3ld4}