tl;dr
- Disk Dump extraction.
- USB leftover Capture data extraction.
- Zip file cracking.
Challenge points: 144
No. of solves: 89
Solved by: g4rud4 & f4lc0n
Challenge Description
Initial Analysis
We found that the given network capture contains the USB traffic. Their communications captured are between a few USB devices to the HOST. One of them is a Mass Storage Device and the other is a Keyboard.
Further Proceeding
The Mass Storage Device is actually carrying a FAT32 Disk Dump. We extracted the data transfered using scapy
1 | #!/usr/bin/env python |
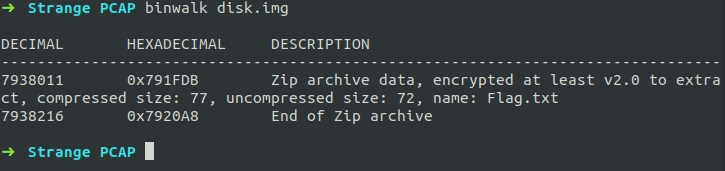
As the extracted file seems to be a disk dump, we can extract the contents using binwalk.
1 | $ binwalk -e disk.img |
We have found a zip file in the binwalk output. So after extracting it and opening it, it asked for a password.
As said earlier, there is some USB Keyboard data is being transferred. So kept a filter usb.capdata for getting the leftover capture data and storing those into another pcap and running the code given below, will get the password for the zip file.
Here is the code for extracting the USB Hid Keys,
1 | import os |
The zip file password is: 7vgj4SSL9NHVuK0D6d3F
Flag
Unarchiving the zip file using the above password, gives us the flag.
Flag: HackTM{88f1005c6b308c2713993af1218d8ad2ffaf3eb927a3f73dad3654dc1d00d4ae}